 Scotti Woolery-Price | Partner Marketing Manager, Thales
More About This Author >
Scotti Woolery-Price | Partner Marketing Manager, Thales
More About This Author >
 Scotti Woolery-Price | Partner Marketing Manager, Thales
More About This Author >
Scotti Woolery-Price | Partner Marketing Manager, Thales
More About This Author >
Enhancing Security and Maintaining Control of Data used by Copilot
As an experienced CISO or data protection specialist, you know the critical importance of maintaining the security of confidential data and meeting regulatory compliance, especially in today's remote working environment. This is particularly crucial for sectors such as financial services, government, and healthcare.
One Size Does Not Fit All
Risk-based controls are not one-size-fits-all; they depend on your industry, operational regions, and overall risk appetite. Common concerns include insider threats, outsider threats, and regulatory compliance requirements—ranging from industry-specific to national regulations.
Classifying Sensitive Data
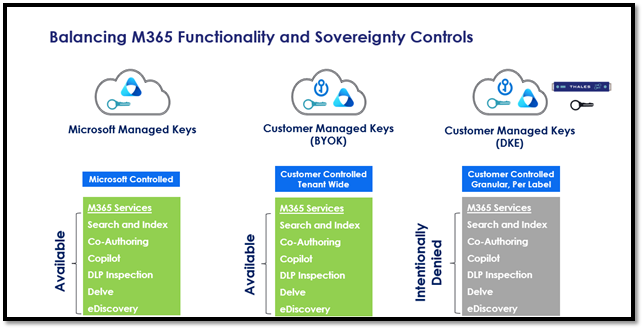
As you likely already categorize your data by sensitivity level, it is essential to apply advanced encryption solutions accordingly. Sensitivity labels should be defined based on your organization's risk tolerance. A sizable portion of your data is probably not extremely sensitive and can be protected with standard Microsoft Managed Keys. To manage data based on its sensitivity label, Thales supports Double Key Encryption (DKE) for Microsoft 365, ensuring compliance with regulations such as HIPAA, PCI DSS, GDPR, and Schrems II.
Protecting Your “Crown Jewels” Using Double Key Encryption
Highly sensitive data, or "crown jewels," typically comprise less than 10% of your organization's total data. However, if compromised, this data could have severe repercussions, including erosion of customer trust, exposure of intellectual property, and loss of competitive advantage. The sensitivity of this data can evolve over time; for example, quarterly earnings reports are extremely sensitive before disclosure but lose their sensitivity afterward.
Double Key Encryption leverages two keys to access protected content. Microsoft retains one key in Microsoft Azure, while you hold the other. This ensures that your most sensitive data remains secure and accessible only to authorized personnel.
Double Key Encryption allows our customers to maintain complete control over their sensitive data.by integrating seamlessly with our DKE partners, we provide a robust data protection solution that addresses evolving security and compliance needs in today's multi-cloud environments."
DKE and Copilot
DKE encrypted data is intentionally inaccessible to the rest of M365 services, including Copilot. This ensures tight control over who within your organization can access your data. Learn more about Copilot best practices.
Addressing Security and Compliance Challenges
Managing security in multi-cloud environments and meeting overwhelming regulatory compliances can be complex. DKE simplifies this by providing a robust encryption solution that ensures data protection always lies with the end customer.
Flexible Deployment Options
Thales solutions like CipherTrust Manager and Luna Key Broker for Microsoft DKE can be deployed in the cloud, on-premises, or in hybrid environments. They also work seamlessly with Luna Network HSMs and Luna Cloud HSMs, offering you the flexibility to choose the deployment model that best suits your needs.
Integrated and Convenient Service
DKE is designed for mission-critical data, which typically constitutes around 5-15% of your total data, depending on your industry. With a Microsoft 365 E5 license, you can store documents and files protected with DKE on-premises.
Content protected with double key encryption requires users to have access to both keys to decrypt. Authorization and the first-level key are performed in Microsoft 365. If the user is authorized to view the data, the still-encrypted key protecting that data is released to the client. The client calls the double key encryption service, going through a second round of authentication and authorization. If authorized to use the second key, the service releases the encryption key, allowing the client to decrypt. This ensures that the content key and plaintext content are never available to Microsoft.
Achieving Operational Sovereignty in the Cloud
Hybrid cloud environments often result in proprietary tools and APIs, creating challenges in orchestrating effective security controls. Thales key management supports all hybrid cloud scenarios and partners with major cloud service providers to deliver comprehensive security solutions. For customers that require their keys to be held outside of Microsoft, another effective approach is Bring Your Own Key (BYOK), allowing you to meet compliance requirements while maintaining full functionality to manage and control encryption keys for data at rest and enhancing compliance with data protection laws like GDPR and HIPAA. BYOK is applied tenant-wide and protects all data regardless of its sensitivity label.
Protect What Matters Most
Double Key Encryption offers a powerful solution for enhancing your organization's security and compliance posture. By leveraging Thales CipherTrust Manager or Luna KeyBroker with DKE for Microsoft 365, you can ensure your most sensitive data remains secure and compliant with industry regulations. This solution strikes a balance between risk mitigation and user experience. Remember, risk mitigation should be viewed as an enabler, not a business impediment. Protecting all data indiscriminately isn't necessary; instead, use the appropriate tools for specific tasks.
Next Steps
Ready to enhance your organization's security and compliance with Double Key Encryption? Contact us today to learn more about how Thales solutions can help you protect your most sensitive data and meet regulatory requirements. Let's work together to secure your digital future! Learn more by watching this webinar on demand.
Please visit the CipherTrust Manager Community Edition from the Microsoft Marketplace to enable a 90-day free trial, or try the as-a-service option from the Thales DPoD Marketplace under CipherTrust Data Security Platform Services. Then configure CCKM for Microsoft DKE.