Last month, I presented at the FCW Continuous Diagnostics Mitigation (CDM) Summit. The vision of the CDM program, created in 2012, is that all federal networks should be continuously scanned to identify and respond to threats and breaches. Consistent with the federal government’s deployment of Information Security Continuous Monitoring (ISCM), the CDM program is a dynamic approach to fortifying the cybersecurity of government networks and systems. It provides cybersecurity tools, integration services, and dashboards to participating agencies to support them in improving their respective security posture.
The topic of my presentation at this summit was a “Data-centric approach to DEFEND”. DEFEND is the fourth phase of the Department of Homeland Security’s CDM program. The key focus of this phase is data security.
To address complexity, try a decision tree approach
Data protection and security can obviously cover a broad range of methods and integrations based on where the data is created and stored…not to mention the impact cloud and digital transformation have on an organization’s data protection strategy.
I always take a data-centric approach to security discussions beginning with the application stack—at the point where a user authenticates to an application, which writes to a database that is running on an OS. I follow that path down to where that data is stored. Along the way, I highlight where and why industry best practices for encryption, policy and access controls can be applied. Leveraging this type of “decision tree to security” (see Figure 1 below) helps organizations validate the points of weakness and the tools available to achieve not only compliance but to provide the highest-level security posture.
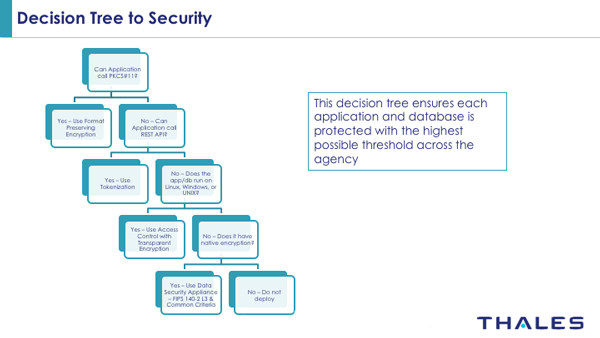
Fig. 1: Developing a decision tree approach to security
In general, I’ve found that this approach really resonates with the security teams and CISOs that I speak with on a regular basis. In addition, lately I’ve been asked to help them sell data-centric approaches internally. This internal audience can range from application and data store owners to cloud architects. Interestingly enough, the decision tree approach has helped demonstrate (and sell internally) where data security can be applied for the most potent layer of defense.
The decision tree approach can be a vital tool in understanding your data security options, how they can be applied, and selling the concepts internally when trying to apply CDM DEFEND practices to your data.
Data protection done right
It is all about data protection when it comes to CDM DEFEND. Every organization has their unique internal infrastructure and business owners, but a decision tree can help simplify, organize and streamline considerations. (see Figure 2 below)
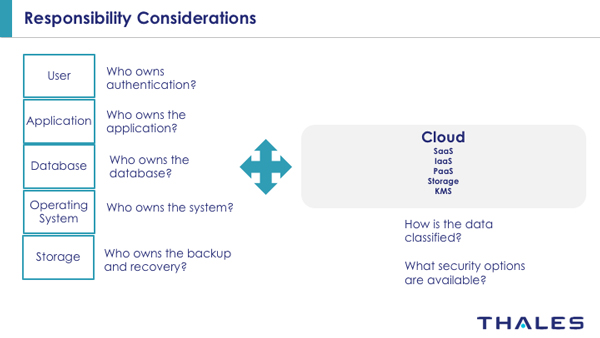
Fig. 2: Streamlining considerations
Cybersecurity can get political and complicated with so many voices that often it is hard to know where to start. The good news is that it doesn’t have to be.
Fortunately, Thales provides a data security platform that can apply data protection controls at the highest level all the way down to key management for native approaches. For more information on how Thales can help you address CDM, please read our white paper on Addressing Continuous and Diagnostics Mitigation requirements.

 Brent Hansen | Federal CTO
Brent Hansen | Federal CTO