 Randy Hildebrandt | Product Marketing, Data Protection
More About This Author >
Randy Hildebrandt | Product Marketing, Data Protection
More About This Author >
 Randy Hildebrandt | Product Marketing, Data Protection
More About This Author >
Randy Hildebrandt | Product Marketing, Data Protection
More About This Author >
To most of us, perhaps unknowingly, data is everything. Whether it is a groundbreaking idea, sensitive health records, or confidential business strategies, data underpins both our personal and professional lives. That is why protecting it at every stage (at rest, in transit, and in use) is no longer optional. It is essential.
But in today’s fast-paced digital environment, ensuring that data stays secure is becoming more challenging than ever. Organizations are rapidly shifting to the cloud, embracing hybrid work, and collaborating across borders. These shifts offer agility and scale, but they also introduce new vulnerabilities and regulatory pressures.
How can businesses stay ahead of these challenges without slowing down innovation?
That’s where Thales’ End-to-End Data Protection (E2EDP) comes in. Designed to meet the needs of modern, multi-environment enterprises, Thales E2EDP ensures that your data stays always protected, no matter where it travels or who accesses it. By combining robust encryption, confidential computing, such as Intel® Trust Domain Extensions (TDX), Intel® Tiber™ Trust Authority and major cloud providers, this solution brings continuous, verifiable protection to even the most sensitive workloads.
Who Needs E2EDP?
Organizations in highly regulated industries or those subject to mandates such as Digital Operational Resilience Act (DORA) or National Institute of Standards and Technology (NIST) will benefit significantly from E2EDP’s persistent protection and zero-trust approach. Whether it is public sector data, financial transactions, or healthcare records, E2EDP ensures your data remains safe, even in unfamiliar new environments.
In this blog, we will explore several real-world use cases that show how organizations can secure their data, from cloud migrations to multi-party collaborations, thanks to the powerful alliance between Intel®, Thales, and today’s leading cloud platforms.
Confidential AI: Unlocking Insights Without Exposing Data
Artificial Intelligence (AI) is transforming industries like finance, healthcare, and retail, but training AI models often requires sensitive data. How do you harness the value of AI without compromising security or privacy?
By executing AI workloads with Confidential Computing using E2EDP, the pipeline of Confidential AI is set; this secure approach allows different organizations to collaborate between them, sharing sensitive datasets within Confidential Computing Trusted Execution Environments but at the same time, preserving the privacy of their own datasets, without revealing the raw data itself to the other parties. Let us look at an example.
A bank working to prevent fraud and money laundering needs to analyze large volumes of financial data. To find broader patterns, it may need to share insights with other institutions. Traditionally, this meant risking customer privacy. With Confidential AI, however, multiple banks can analyze combined datasets without exposing any sensitive information. Thanks to confidential computing, independent attestation, and data protection powered by Thales.
With E2EDP it's ensured that:
- Only authorized users can access the raw datasets and results.
- Preserving the privacy of raw data that stays invisible to unauthorized parties.
- All operations happen in a verified, isolated environment.
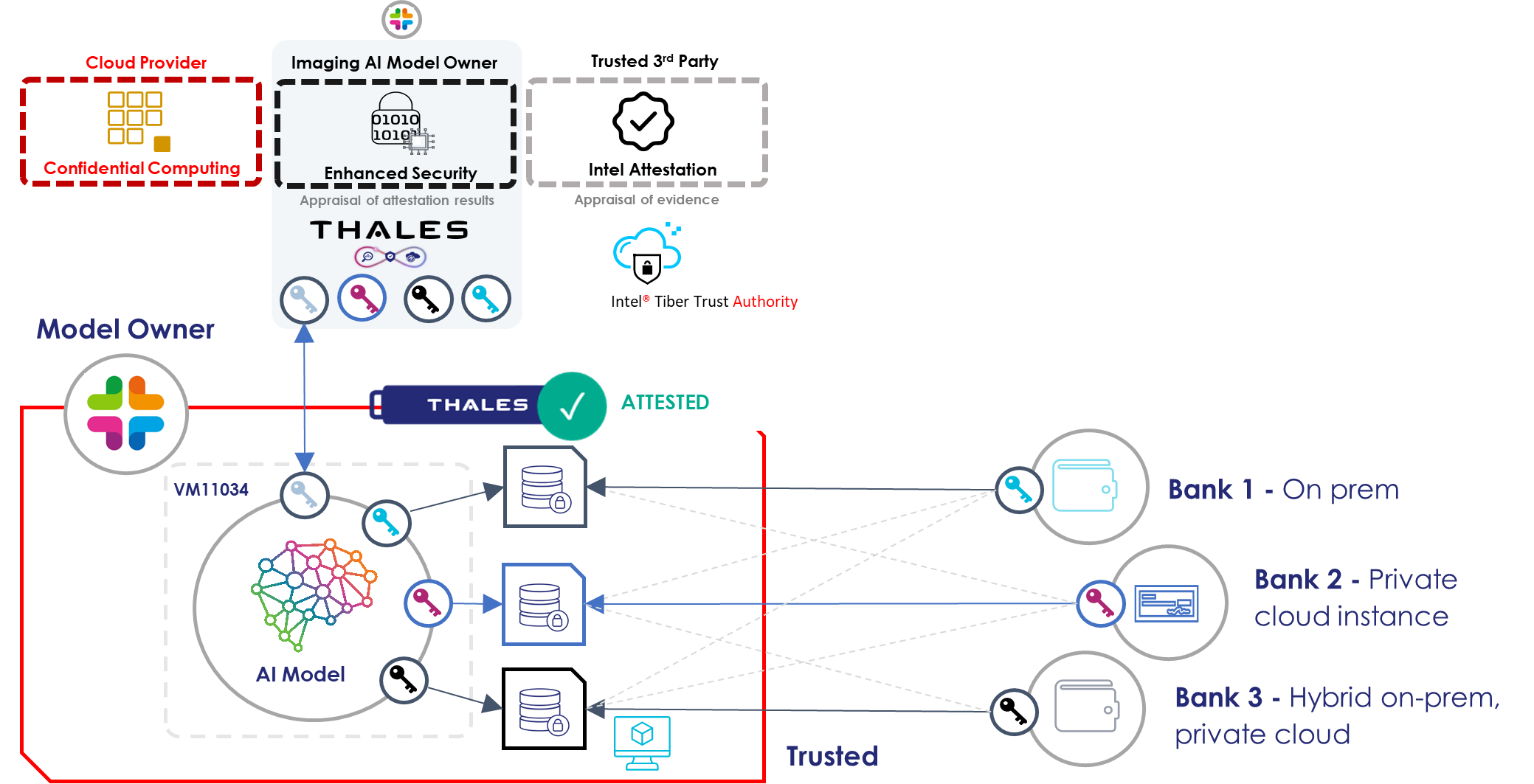
Secure Cloud Migration: Lift-and-Shift with Confidence
Moving legacy systems to the cloud, especially those handling sensitive data, can be risky. But E2EDP makes "lift-and-shift" safe and seamless.
With E2EDP:
- Data is encrypted on-prem and stays protected throughout its journey.
- Customers keep full control over encryption keys.
- Data is only processed within attested secure environments in the cloud.
This enables organizations to migrate workloads with confidence while meeting compliance requirements and enabling secure multi-party collaboration in new environments.
E2EDP, Trusted Security from Edge to Cloud
E2EDP combines state-of-the-art leading technologies of Thales, Intel, and leading cloud providers. This solution is designed for organizations that need to maintain the highest levels of data security, especially in regulated sectors at all stages of data, at rest, in transit, and in use.
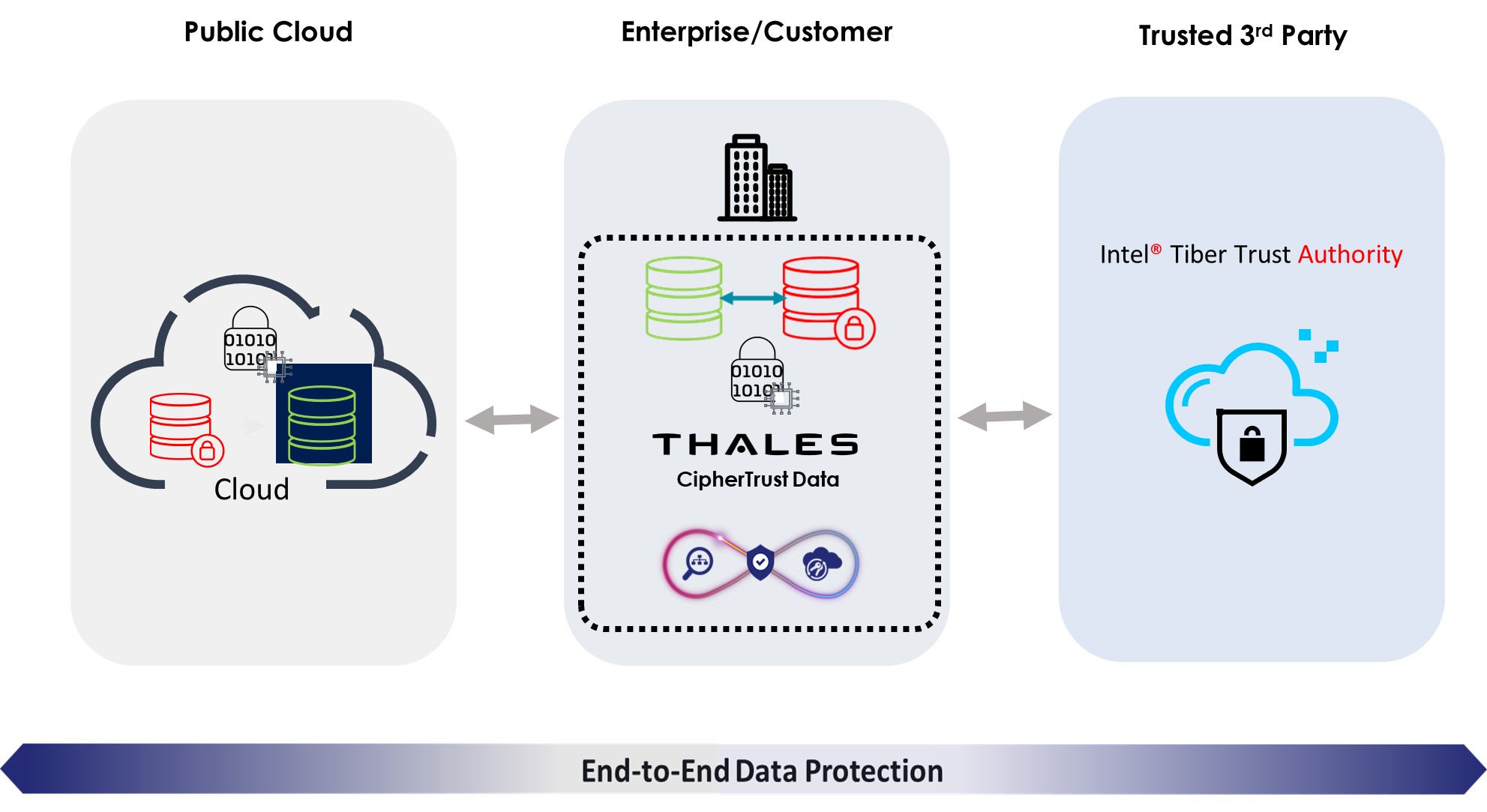
With E2EDP, data is protected at every stage:
- At Rest: Encrypted using Thales CipherTrust Transparent Encryption and controlled by the customer.
- In Transit: Stays encrypted from source to destination.
- In Use: Verified using Intel Trust Authority, with access granted only to authorized parties within confidential computing environments.
This level of protection ensures that no unauthorized user, not even cloud administrators, can view or tamper with your sensitive workloads.
Conclusion: Protect Your Data, Everywhere and Always
The future of secure data is end-to-end protection. Whether you are migrating to the cloud, running AI workloads, or sharing sensitive insights across partners, E2EDP gives you confidence that your data is private, protected, and compliant, wherever it goes.
In a world where trust and privacy are paramount, Thales’ End-to-End Data Protection sets a new standard for secure computing.
See E2EDP in action: https://www.youtube.com/watch?v=HN33iSjK_f0.
For more information, visit End-to-End Data Protection | Thales.