The IoT is transforming the world we live in at a rapid pace. Companies are deploying billions of network-connected devices into mission-critical environments such as medical devices, industrial and manufacturing control systems and autonomous vehicles. This transformation is possible through the collection and analysis of IoT-generated data to drive business value. For all the advantages these connected devices bring, inadequate security practices can quickly undermine their value by eroding the trust and safety of end-users.
The state of IoT security
Due to the crucial infrastructure supported by IoT devices, security is critical. Legacy devices can pose a challenge in attaining adequate IoT security since 85% of these interconnected legacy devices have limited update and patching capabilities. As new privacy rules and regulations continue to evolve, the state of IoT security will become even more complicated in the future
However, awareness for security challenges is growing, as is the recognition of the threats IoT could pose for businesses and society at large. Based on this growing awareness and driven by regulatory compliance, there are strong indications that the IoT market is maturing towards building devices that are secured by default. However, much of the regulatory activity has only generated guidelines, requiring compliance on a volunteer basis.
Aligning IoT security with the NIST Cybersecurity Framework
When it comes to evolving IoT security, well-established frameworks, such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework, can easily be leveraged. The framework consists of five core functions that are not only applicable to cybersecurity risk management but also risk management at large.
To develop an understanding of the organizational risk, we need to Identify the risk that is posed by IoT systems. The first step is to identify the devices that make up the organization, just as we do with personnel. For IoT devices, its digital identity is comprised of both hardware and software. This identity can be leveraged by the organization to gain visibility of all interactions of the device. Just like effective and timely patient care cannot be provided if we do not know who and where they are, organizations cannot secure IoT devices if they have gaps in visibility or identity management. Identification of the people accessing these devices is equally important, as is tracking their interactions.
Based on the identified risk, the Protect step is about developing and implementing appropriate safeguards to manage the risk. Such security controls start by segmenting and securing the network which connects the devices and systems. The device software should be kept up-to-date with signed binaries – to ensure that the software is authentic. Data captured and transmitted by the devices should be encrypted at rest and in-motion with effective key management. Root-of-trust should be leveraged to establish trust at all levels of the IoT system. This trust can be further leveraged to enforce strong access controls and keeping auditable records of the interactions.
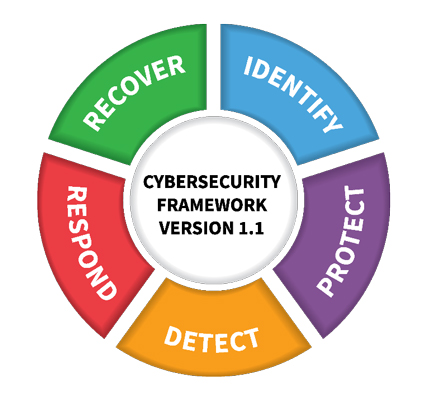
The scope of the Detect function is to become aware of any undesired change in the security configuration of the IoT system (all hardware and software). This can be achieved through intrusion or incident detection mechanisms, continuous monitoring and alerting to identify anomalous device behavior, such as when devices are hijacked and used in botnets. Detection of jailbroken devices (i.e. devices with unauthorized modifications to hardware or software) or access by unauthorized personnel is also an important mechanism.
Once an activity is being detected, we need to Respond and contain it. Revoking the certificate of the compromised device to suspend further access to services and networks, and updating the security configuration are fast and effective controls to limit the impact of the malicious activity. Similarly, revoking personnel access and ensuring decision-making systems are robust enough to operate without the data from impacted IoT devices should be addressed as well.
Finally, the organization must Recover promptly and build resilience. The devices’ chain of trust should be rebuilt by rotating keys and changing the security configuration and the compromised cryptographic algorithms. Signed software updates should be made to provide future mitigation of the threat, along with new technology and or processes. Post analysis may require updates to the architecture of the system or design of the IoT devices.
Five principles of optimizing IoT security
These five core functions are the pillars of an effective IoT security program:
- Unique digital credentials for each device validates its authenticity, enforces access controls and asserts with high assurance that its messages are genuine.
- Secure key storage, preferably in hardware. Hardware Security Modules (HSMs) or other related Trusted Platform Module (TPM) technology are designed to provide hardware-based, security-related functions.
- Digitally signed and verified software. Code signing verifies the author’s identity and ensures the code has not been changed or corrupted.
- Dedicated Roots of Trust. When you manage your roots of trust, you have complete control over the trust anchor to securely perform identity validation of every device or person in the system.
- Updatability of certificates, keys, algorithms, and Roots of Trust to rapidly respond to cryptographic incidents and events, maintain agility, and keep the operation of your IoT systems uninterrupted.
For more in-depth analysis, watch the on-demand webinar Evolving Security for an IoT World or the follow-up Q&A session.
