The exponential growth of a global information economy, driven by new technologies and disruptive business models, means that an ever-increasing amount of sensitive data is collected, used, exchanged, analysed, and retained. In all cases, this data requires protection from unauthorised access to ensure the privacy and security of both individuals and organisations.
The 25th of May marks the second anniversary of the GDPR. However, the demand for protection of personal data is not limited to the EU. The trust deficit is widening around the globe causing people to change the way they behave online. As countries around the world are increasingly addressing similar challenges, they are equipping themselves with new data protection rules or modernising existing ones. For example, in the US the California Consumer Privacy Act (CCPA) will be enforced on July 1, while India’s Personal Data Protection Bill is waiting to be endorsed by the Indian Parliament. These laws often have several common features that are shared by the EU data protection regime.
Privacy compliance demands visibility
The sheer volume of sensitive data means there is an ever-increasing number of accidental or intentional data breaches, incorrect or lost data records, and data misuse incidents. At the same time, SOX, HIPAA, PCI, CCPA and GDPR compliance regulations demand that organisations provide complete visibility into, and an uninterrupted record of, what data is accessed or changed, when, and by whom.
Having visibility into your assets, whether they are data or devices, is the cornerstone of every robust security programme. You can’t protect something you don’t know exists. Therefore having visibility into where your sensitive data resides and tying it back to obligations is critical to “implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk” presented by “unauthorised disclosure of, or access to personal data transmitted, stored or otherwise processed.”
With remote working as the new normal, an unprecedented number of workers are logging in from diverse locations, personal devices, applications, and cloud accounts, creating new risks for companies. In a rush to maintain business continuity, organisations are likely to overlook critical security considerations, leaving themselves vulnerable to hacking.
In fact, violation of Article 32 of the GDPR, which dictates organisations to implement the appropriate security controls to safeguard sensitive data, accounts for the majority of fines imposed by the National DPAs during the first two years of GDPR.
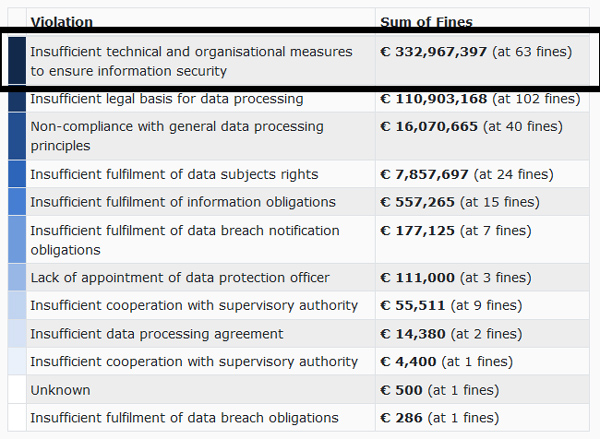
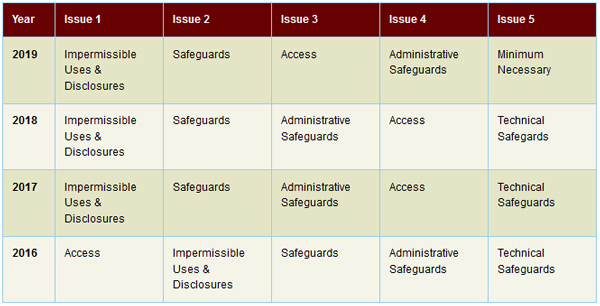
Not surprisingly, the same reasons account for the majority of the cases investigated for the violation of the HIPAA Privacy Rule.
Are businesses ready for privacy compliance?
The above statistics demonstrates that businesses are not ready for privacy compliance. According to a survey by Capgemini, only 28% of the respondents believe they are fully GDPR compliant. For many organisations, the true size of the GDPR challenge only becomes apparent as they begin the initial projects to identify the applicable data that they hold.
Companies must prioritise data risks by creating a classification policy based on data sensitivity. Policies must be developed and implemented that determine what types of information are sensitive and what methods, such as encryption, should be used to protect that information. In addition, companies must monitor the transmission of information to ensure that the policies are adhered to and are effective.
How can you gain visibility into your sensitive data?
Luckily, new technology solutions can help enterprises gain complete visibility into their sensitive data and strengthen their GDPR compliance. Solutions like Thales CipherTrust Data Discovery and Classification allow organisations to discover their sensitive data, assess the risk associated with this data, then define and enforce security policies. Besides being able to facilitate GDPR compliance at any given moment, your organisation can save money, while building trust with your customers and partners.
Learn how to efficiently discover and classify sensitive data, get a clear understanding of data and its risks, and take actions to close the gaps, from a single pane of glass, on the Thales CipherTrust Data Discovery and Classification page or join our webinar Privacy Regulations compliance like GDPR, start with knowing your sensitive data on Thursday, June 18.

 Tzach Kaufmann | Director, Product Management Data Discovery and Classification
Tzach Kaufmann | Director, Product Management Data Discovery and Classification