It’s hard to believe it’s mid-October. Along with autumn, comes National Cybersecurity Awareness Month (NCSAM). The NCSAM 2019 focuses on personal accountability. Driven through mass public engagement, the ‘Own IT. Secure. IT. Protect IT.’ theme will help to encourage personal accountability and proactive behavior in digital privacy, security best practices, common cyber threats and cybersecurity careers.

As part of their digital transformation process, more and more businesses are moving to the cloud. Many companies think that by moving your data to the cloud, the service provider will be responsible for the security of your data. This is a misconception.
The hard truth is that most breaches in cloud computing environments are related to data or applications “living” in the cloud and not with the actual infrastructure of the cloud service. While we often listen to misconfiguration as a root cause, there are other causes as well, such as lack of access control and management, unsecure storage, poor permissions management, etc. These security incidents prove that you must have the right controls in place from a security and governance perspective.
Although cloud computing has become a foundation of digital business, many organizations still struggle to optimize this powerful tool. In fact, a new global study from Thales, with research from the Ponemon Institute, reveals that even though nearly half (48%) of corporate data is stored in the cloud, only a third (32%) of organizations admit they employ a security-first approach to data storage in the cloud.
Cloud computing represents one of the most valuable innovations in current IT and business strategies but continues to be misunderstood and underutilized. Organizations need to familiarize themselves with the benefits of cloud computing and the associated security risks. This will ensure that every employee that has the potential to use the cloud accepts their responsibility for making sure that any data they place in the cloud is secure. Everyone must accept that security extends beyond the personal boundaries of the smartphone and includes a responsibility at work too.
All cloud service providers (CSPs) have a shared responsibility model that dictates who is responsible for what. Knowledge of everyone’s responsibilities can help you take the protective measures required to ensure integrity and confidentiality of your data.
The Shared Responsibility Model
Who’s responsible for the integrity and confidentiality of the services provided by CSPs and the data therein? It is important to understand the shared responsibility model, where a great deal of misunderstanding and fog exists. Let us examine the typical cloud provider model.
As an example, the AWS shared responsibility model is that “Security and Compliance is a shared responsibility between AWS and the customer.” Specifically, AWS is responsible for the “security of the cloud”. “AWS operates, manages and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates.”
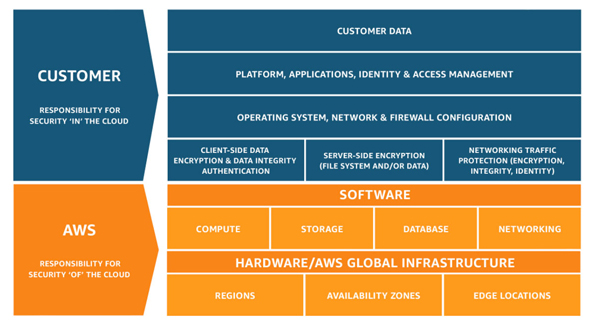
On the other hand, the customer is responsible for the “security in the cloud”. According to AWS “The customer assumes responsibility and management of the guest operating system (including updates and security patches), other associated application software as well as the configuration of the AWS provided security group firewall. Customers should carefully consider the services they choose as their responsibilities vary depending on the services used, the integration of those services into their IT environment, and applicable laws and regulations.”
Microsoft Azure has a bit of a different approach to shared responsibility, but essentially responsibility for identity and directory infrastructure, as well as network controls and applications for PaaS and IaaS are retained by the customer. The only aspect of security that transfers wholly to Azure is physical security. According to Microsoft Azure “Ensuring that the data and its classification is done correctly, and that the solution will be compliant with regulatory obligations is the responsibility of the customer. Physical security is the one responsibility that is wholly owned by cloud service providers when using cloud computing.”
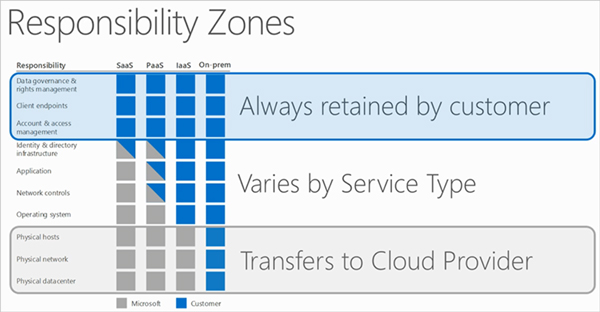
The clarifications above should help clear away the fog on who is responsible for what. Clearly, it is the customers’ responsibility to own the security of the data stored in any cloud computing environment.
There are a variety of factors to consider in order to minimize user error and improper implementation – and this becomes doubly important when we consider the fact that almost 60% of the decisions to use the cloud are now taken by Shadow IT – people not familiar with the usual IT security policies of a company. First, every person who has the potential to use the cloud needs to be trained to consider the type of data they are uploading to the cloud and how it is to be protected. Just because they can store something doesn’t mean you necessarily have a business need for cloud storage, set policies determining which classifications of data are suitable for cloud storage. Minimizing your data footprint not only lowers complexity, making it easier to spot misconfigurations, but also reduces the potential damage in the event you do become the victim of a breach.
Second, everyone should follow best practices when setting up new cloud storage or managing a current setup. CSP offered security services cannot serve the needs of enterprise-wide security, especially when the enterprise uses multiple cloud platforms. If your corporate strategy caters to cloud agility, why should your cloud security strategy be pinned to one cloud provider? Organizations that want to be agile and avoid vendor lock-in need a solution that not only provides the ability to centrally enforce security policy but also the ability to standardize roles and responsibilities. This is so applications and their data can truly live within one or more clouds without fear of breaking or slowing operations.
Bring Your Own Key to the Cloud
For enterprises that elect to use encryption to protect their data, securing their encryption keys is their responsibility and it is of paramount importance. Bring Your Own Key (BYOK) allows enterprises to encrypt their data and retain control and management of their encryption keys. A best-practice solution to BYOK is for the enterprise to generate strong keys in an agnostic environment such as a key manager or tamper-resistant hardware security module (HSM) and control the secure export of its keys to the cloud, thereby strengthening its key management practices while retaining total control over the critical “keys to the kingdom”.
Thales Portfolio for Cloud Security
Cloud storage is a great and usually cost-effective tool for storing company data, but there are major security issues it can cause for your business if you aren’t careful. Thales offers a comprehensive portfolio of identity and access management and data protection solutions that ensure you are the only one who controls access and keys to your data – especially across multi-tenant, geographically distributed sites.
For more information, please visit our website to read our Best Practices for Secure Cloud Migration white paper.

 Gary Marsden | Cloud Services Director
Gary Marsden | Cloud Services Director