Criminals use a wide range of methods to commit fraud. The increasing trend of using mobile payments for in-store purchases (especially during the pandemic) is leading criminals to increasingly focus their efforts on defrauding people through online fraud and scams.
Fraud and scams move to the web
The Verizon DBIR 2020 report indicates that financially motivated attacks against retailers have moved away from Point of Sale (POS) devices and controllers, towards web applications. This largely follows the trend in the industry of moving transactions primarily to a more web-focused infrastructure. As the infrastructure changes, the adversaries change along with it to take the easiest path to data.
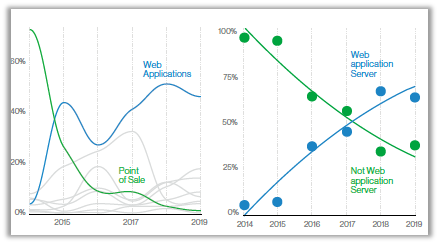
Figure 1: Web application breaches in the Retail industry. Source: Verizon DBIR 2020
The web applications attack pattern is composed of three main action varieties: the use of stolen credentials, online skimming, and the exploitation of apps vulnerabilities. Even when banking organizations are upgrading security posture to safeguard sensitive financial information, hackers can steal the data intelligently by tying known vulnerabilities together, and making it turn out to be a potential attack.
Stolen credentials
As reported in the UK Finance “Fraud: The Facts” 2020 report, the theft of personal and financial data through data breaches was a major contributor to fraud losses in 2019. The stolen data is used both to commit fraud directly and indirectly. For example, compromised card details are used to make unauthorized purchases online and personal details are used to take over an account or apply for a credit card in someone else’s name. Criminals use personal and financial data to impersonate customers and add apparent authenticity to a scam.
Online skimming
Online skimming is an adverse activity of stealing payment information during card-not-present transactions by infecting e-commerce sites with sniffers. Once the malware is injected, it is very hard to detect the traces of it on the website. After gaining access to the retailer’s payment page, the attacker starts skimming the payment information such as billing address, CVV2, PAN, card expiration date, etc. during the transaction process without the knowledge of both customer and service provider.
Security researchers often use the term “magecart” to refer to different groups of cybercriminals that perform various types of skimming attacks. Recently, PCI SSC has released a bulletin warning e-commerce merchants and service providers to be aware of the emerging online card fraud, mentioning the potential threat and the steps to be taken to prevent it.
Vulnerabilities exploitation
When the bad actors are not using other people’s keys and credentials against your infrastructure, they are using unpatched vulnerabilities in your web apps to gain access. As more and more people and businesses rely on mobile banking applications, they become vulnerable to fraud. In fact, recent reports highlight that “half of all mobile banking apps are vulnerable.” The influx of new mobile users due to the COVID-19 crisis has caused banks to swiftly add new features to their applications to meet the increased demands by their customers. Coupled with the fact that only about half of all vulnerabilities in the retail industry are getting patched within the first quarter after discovery, it is easy to understand the risks of being defraud by criminals.
Securing digital transactions
The banking and finance industry is taking proactive steps to secure online and contactless transactions. As the digital economy plays an increasing part in our lives, it is vital that electronic payments are secure, convenient, and accessible to all.
Strong Customer Authentication (SCA)
The Payment Services Directive 2 (PSD2) aims to secure online transactions for Payment Service Providers (PSPs). As such, it introduces enhanced security measures and requires that Strong Customer Authentication (SCA) is applied to all electronic payments - including proximity, remote and m-payments - within the European Economic Area (EEA). The SCA mandate is complemented by some limited exemptions that aim to support a frictionless customer experience when transaction risk is low.
Supported by the new EMV 3DS protocol, SCA requires that the payer is authenticated by a PSP through at least two factors, each of which must be from a different category as summarised in Table 1.
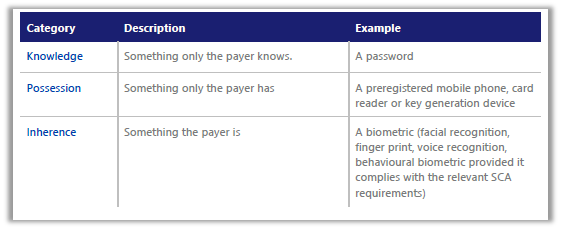
Table 1: Strong Customer Authentication Factors. Table courtesy of Visa
Factors must be independent such that if one factor is compromised, the reliability of the other factor is not compromised.
In addition, PSPs are required to have effective transaction monitoring mechanisms in place, to detect unauthorised or fraudulent payment transactions. These mechanisms should allow capturing of the following information:
- lists of compromised or stolen authentication elements
- the amount of each payment transaction
- known fraud scenarios
- signs of malware infection in any sessions of the authentication procedure
- in the case that the access device or the software is provided by the PSP, a log of the use of the access device or the software and any abnormal use.
Big Data and EMV 3DS
Fraud detection is where big data and machine learning come in handy. The EMV 3DS protocol delivers 10 times more data, such as device channel and payment history, than the previous version, to provide adaptive authentication and step up stronger authentication methods if a transaction is qualified as high risk. Using machine learning, algorithms can go through huge transactional data sets to spot unusual behaviour.
The use of big data analytics by the banking sector can lead to enhanced fraud detection and superior risk assessment. Supported by increased computational power, banking systems can analyse billions of real-time transactions, coupled with additional data including device, geographical, behavioural and threat intelligence input. By combining this with historical data, the bank can build a profile of a customer’s behaviour so that any unusual and potentially fraudulent activity can be identified and flagged up.
Banks are also increasingly looking at ‘behavioural biometrics’ tools to identify potential cases of fraud and prevent them where possible. Some banks have adopted software that monitors the ways in which consumers type and swipe on their devices or how they hold their device in terms of grip, when logged into banking apps.
Protect card-on-file transactions
A card-on-file transaction is a transaction where a cardholder authorises a retailer to store the cardholder’s card payment details (also known as PAN, Primary Account Number). Then the cardholder authorises that same retailer to bill the cardholder’s stored card account. The information contained on these stored credentials are sensitive and if attackers get hold of them can impersonate legitimate customers and make fraudulent transactions. There are two ways to protect customers’ PAN, encryption and tokenization.
Using payment Hardware Security Modules (HSMs) the retail and banking industry can encrypt card-on-file information and protect the subsequent processing of payment transactions. Payment HSMs provide native cryptographic support for all the major card scheme payment applications and undergo rigorous independent hardware certification under global schemes such as FIPS 140-2 and PCI HSM.
In addition to encryption, with card-on-file tokenization, a cardholder’s PAN is replaced with payment tokens, which are submitted through the payment process. Assigning a token to replace a card number ensures payment information stays safe since this information would be meaningless to anyone who might encounter it—like hackers, fraudsters, etc. There are two methods of tokenization, namely PCI tokenization and EMV tokenization, named after the respective organisation that introduced the standard.
Financial service providers must take strict security measures to protect customer data from bad actors and other cyber threats. In the next part of these series, we will examine the differences between the two methods of card-on-file tokenization. Meanwhile, the Thales Data Threat Report can help you understand the cyber threats financial institutions face today.

 Paul Hampton | Cloud Security Expert, Thales
Paul Hampton | Cloud Security Expert, Thales