It’s my privilege to share my insights on IoT security that were published recently in the esteemed ISACA Journal on June 3 (available only to registered members here1).
In the article, I attempt to answer a number of questions important to IoT manufacturers:
- What are the risks affecting IoT stakeholders?
- Why and how are IoT devices impacted?
- How can IoT manufacturers secure their devices and customers’ data?
I use a number of well-known IoT hacks to illustrate the security issues in IoT devices and their impact on end users. I further describe these incidents and how they affect IoT devices. These range from attacks on industrial devices such as those in power plants to consumer products such as automobiles and children’s toys. It has been found that these IoT devices are all inherently prone to attacks due to several factors, namely:
- Devices lack self-protection mechanisms against misuse/malware attack;
- The environments in which they are deployed make them unsuitable for field upgrade; and,
- The desire to improve security yields to budget constraints.

Figure 1 Article “Security for Internet of Things Device Manufacturers”, copyrighted by ISACA
I also explain that the case for sound security exists today where benefits can be realized for both consumers and manufacturers. This is because:
- Good security prevents counterfeits and therefore protects an organization’s investment;
- Various regulatory mandates including those from the United States and European Union change the mindset of security from “should” to “will”; and,
- Upgradable security can create a good business case where consumers can enjoy continual protection while IoT manufacturers and service providers can ensure recurring revenues by providing upgrades throughout the life-cycle of devices.
With the root cause identified and the business case to remediate the risks established, the next task is to understand the mitigating measures to be executed. I highlight that the business goals of IoT manufacturers will be met by following five principles:
- Ensure the device will behave as specified => Trust the source of the data
- Prevent counterfeits => Communicate with only trusted entities
- Ensure security and privacy => Only authorized entities have access to data
- Ensure sustainable operation => Enable security updatability on devices
- Ensure sound situational awareness => Continual assessment and assurance
Public Key Infrastructure (PKI), which is the foundation of the above principles, has been widely deployed in the commercial world. In Figure 2, the concept of “Chain of Trust” is illustrated. To ensure this “chain” is secure, I look into the protection of the “Root of Trust”. Note that this trust model is prevalent in many deployment scenarios, including the seven Secure Properties2 from Microsoft and SAFE-IoT SAFE3 from GSMA. Protecting this Root of Trust can now be achieved by operating the necessary hardware and trust procedures on-premises or as-a-Service from the cloud4.
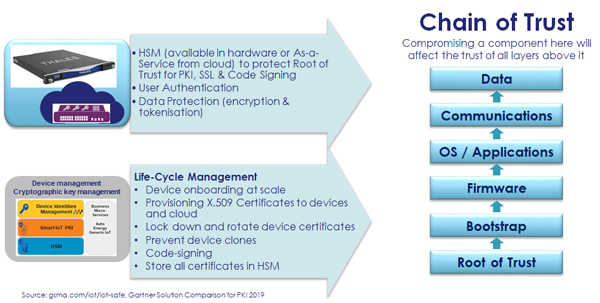
Figure 2 Protecting the chain of trust: From devices (chip level) to code and finally to data
In summary
Although the “why” and “what” of the risks associated with IoT are well documented, there is clearly work to be done to implement secure IoT. Through this article, I describe the framework and procedures to achieve the “how” on the mitigation aspect. Security at the IoT device level is attainable and, by protecting the chain of trust, IoT can defend itself. By doing this, manufacturers and operators can minimize losses from counterfeits, attain regulatory compliance, reduce misuse and facilitate future maintenance.
For more information on how Thales can help address these issues, learn more about “Data Protection On Demand.”
1Welland Chu, “Security for Internet of Things Device Manufacturers”, ISACA Journal 2020 Vol. 3,
2Microsoft, “Seven Properties of Highly Secure Devices,” March 2017, https://www.microsoft.com/en-us/research/wp-content/uploads/2017/03/SevenPropertiesofHighlySecureDevices.pdf
3GSMA, “Common Implementation Guide to Using the SIM as a ‘Root of Trust’ to Secure IoT Applications,” 3 December 2019, https://www.gsma.com/iot/wp-content/uploads/2019/12/IoT.04-v1-Common-Implementation-Guide.pdf

 Welland Chu | Business Development Director, Asia Pac
Welland Chu | Business Development Director, Asia Pac