The more we know about the threats we face, the better our chances of keeping our data secure and our business name out of the headlines. This is exactly the purpose of the annual Verizon Data Breach Investigations Report, now entering its 13th year. This year, the report analyzes 32,000 incidents and 3,950 were confirmed data breaches. The report findings are broken down by industry and aligned with the MITRE ATT&CK framework and CIS Controls.
While we issue our own annual Data Threat Report each year (see our 2020 Thales Data Threat Report-Global Edition), it is interesting to see what other industry leaders uncover when it comes to data breaches
According to the report, one intriguing finding is that criminals seem to be focused on credentials because they make life easier. In fact, the use of credentials is constantly on the rise in both security incidents and breaches. Together with social engineering attacks, like phishing, and human errors, such as misconfiguration and misdelivery, the report notes that credential misuse is the main cause of 67% of breaches.
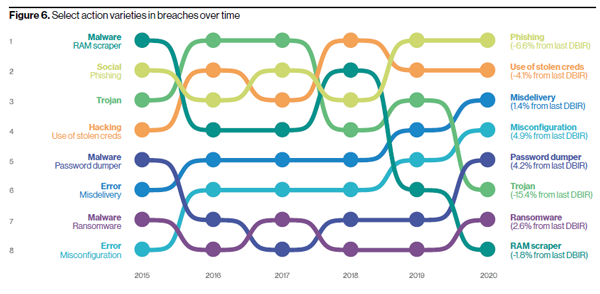
Figure 1: Action varieties in breaches over time. Image courtesy of Verizon.
Key Findings
Attacks on web applications were a part of 43% of breaches, which is more than double the previous year. As workflows move to cloud services, it makes sense for attackers to follow. The most common methods of attacking web apps are using stolen or brute-forced credentials. Personal data was involved in 58% of breaches, nearly twice the percentage of last year’s data. This increase is mostly due to the regulatory requirements for reporting all incidents or breaches that involve breaching the privacy of personal data.
Credential Theft
Top 3 attack tactics
Credential theft, along with social engineering attacks, and exploitation of human errors prove effective for attackers, so they return to them time and again. For most organizations, these three tactics should be the focus of the bulk of security efforts. #Remote Workers - employees working from home - could be particularly vulnerable to these attacks. So in these uncertain times, it makes sense to focus prevention efforts here. For more information on this topic, read our recent blog post about “Securing Corporate Data When Working Remotely is the Norm.”
Malware in decline due to stolen credentials
Criminals love to get the job done the easy way, which explains why malware has been on a consistent and steady decline as a percentage of breaches over the last five years: from a little above 60% in 2015 malware dropped to 17% in 2019. Attack types such as hacking and social breaches benefit from the theft of credentials, which makes it no longer necessary to use malware to maintain persistence.
The trend of using or abusing credentials means that malware varieties and vectors used in breaches are all associated with credentials, one way or another. Password dumper, used to get credentials, has the top spot among breach malware varieties. Email compromise and direct malware install, both associated with the use of stolen credentials, are the top malware vectors.
Hacking is fueled by credentials
Hacking usually involves exploiting vulnerabilities and using backdoors and Command and Control (C2) functionality, but it is fueled by credential theft. Over 80% of breaches within hacking involve brute force or the use of lost or stolen credentials. These hacking varieties are associated in a major way with web applications, where 77% of cloud breaches involved compromised credentials.
As businesses are adopting hybrid workloads, so too are the criminals. These findings are not so much an indictment of cloud security as it is an illustration of the trend of cybercriminals finding the quickest and easiest route to their victims.
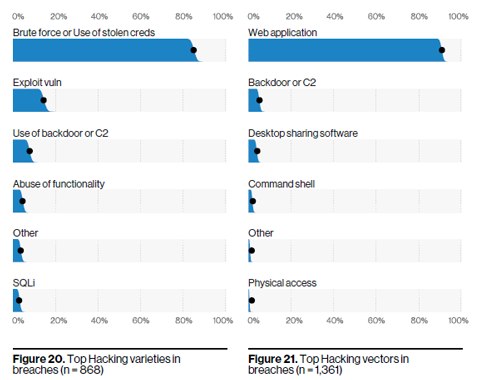
Figure 2: Hacking varieties and vectors in breaches. Image courtesy of Verizon.
Privacy Regulation Benefits are Visible
Personal data is stolen far more often than in previous years. Thefts are being reported more due to the disclosure requirements associated with privacy regulations such as GDPR. As a result, personal data was involved in 58% of breaches, nearly twice the 30% from last year’s data. This includes email addresses, names, phone numbers, physical addresses, and other types of data that one might find hiding in an email or stored in a misconfigured database.
Another benefit of the various privacy and security regulations, such as HIPAA, PIPEDA, PCI DSS, and GDPR is the improved reporting requirements for every action that can lead to an incident or a breach. For example, the report indicates a high number of internal, error-related breaches this year, 881 versus last year’s 424. While people are certainly still far from perfect, this increase is likely from improved reporting requirements because of new legislation and changes to existing laws rather than insiders making more frequent mistakes.
Recommendations Based on CIS Controls
To align the report findings with the corporate security efforts, the Verizon report includes recommendations based on CIS Controls, such as data protection (CSC 13) and account monitoring and authentication (CSC 16).
One of the best ways to limit the leakage of information is to control access to sensitive data. This came through loud and clear in our 2020 Thales Data Threat Report-Global Edition. Our report found that half of all corporate data is stored in the cloud and nearly half (48%) of that data is considered sensitive—everything from intellectual property to employee, financial or personal data. Controls that are useful to protect data include maintaining an inventory of sensitive information, encrypting sensitive data and limiting access to authorized cloud and email providers. In addition, locking down user accounts across the organization is key to keeping bad guys from using stolen credentials, especially with multifactor authentication or, even better, by adopting passwordless, adaptive authentication mechanisms.
I invite you to download our 2020 Thales Data Threat Report-Global Edition and read more about other key findings in my blog post, “Organizations Struggle with Cloud Security in the Post Digital Transformation Era-Highlights from our 2020 Data Threat Report-Global Edition.”

 Tina Stewart | VP, Global Market Strategy
Tina Stewart | VP, Global Market Strategy