 Haider Iqbal | Director of Product Marketing
More About This Author >
Haider Iqbal | Director of Product Marketing
More About This Author >
 Haider Iqbal | Director of Product Marketing
More About This Author >
Haider Iqbal | Director of Product Marketing
More About This Author >
American lawyers Samuel D. Warren and Louis Brandeis first defined privacy in 1890 in a transformative essay entitled "The Right to Privacy." The article, widely regarded as the first US publication to advocate a right to privacy and one of the most influential essays in the history of American law, argues that privacy is fundamentally a "right to be left alone."
Considering that the Internet was born in 1983, and the first iPhone in 2007, it is remarkable how Warren and Brandeis’s essay states, “…numerous mechanical devices threaten to make good the prediction that 'what is whispered in the closet shall be proclaimed from the house-tops,'” mostly pointing to instantaneous photographs and newspapers. Our world has warped into something far more intrusive. But the principle of privacy remains the same.
What is Privacy by Design?
Privacy by Design is a proactive approach to data protection, embedding privacy principles into every stage of product development and organizational processes. By building privacy directly into systems and practices, Privacy by Design helps organizations safeguard user data from the ground up, ensuring compliance with regulations like GDPR and fostering consumer trust.
In today’s digital landscape, where personal data is constantly at risk, Privacy by Design not only addresses regulatory requirements but also elevates privacy to a core organizational value. Embracing this approach demonstrates a commitment to responsible data stewardship and positions privacy as a key element in building brand loyalty and competitive advantage.
Whether digital or physical: Privacy is a human right
With many of us spending more time online than offline, it’s important that we see digital privacy as important as its physical counterpart. Unfortunately, the business world doesn’t always see it as such.
Established regulations like GDPR, PIPEDA and CPRA or emerging ones like APRA are already forcing organizations to think differently. Businesses, however, have enough incentives to respect our privacy, going far beyond mere compliance.
The 2024 Thales Digital Trust Index found that 89% of consumers would only consent for organizations to use their data if certain caveats are met. And McKinsey reported that 85% of consumers want to know the company’s privacy policy before making a purchase.
Privacy by Design: Through a Maslow lens
Maslow's pyramid is a psychological theory that outlines human needs in a hierarchical order, starting with basic needs (like food and shelter) and progressing to higher-order needs (like self-actualization). We can translate this theory into a Pyramid of Privacy.
The Pyramid of Privacy progresses from basic compliance, where organizations meet essential legal requirements, to advanced practices, where privacy is ingrained in the organization's culture and strategy, reflecting a higher level of commitment. But let's look a little closer.
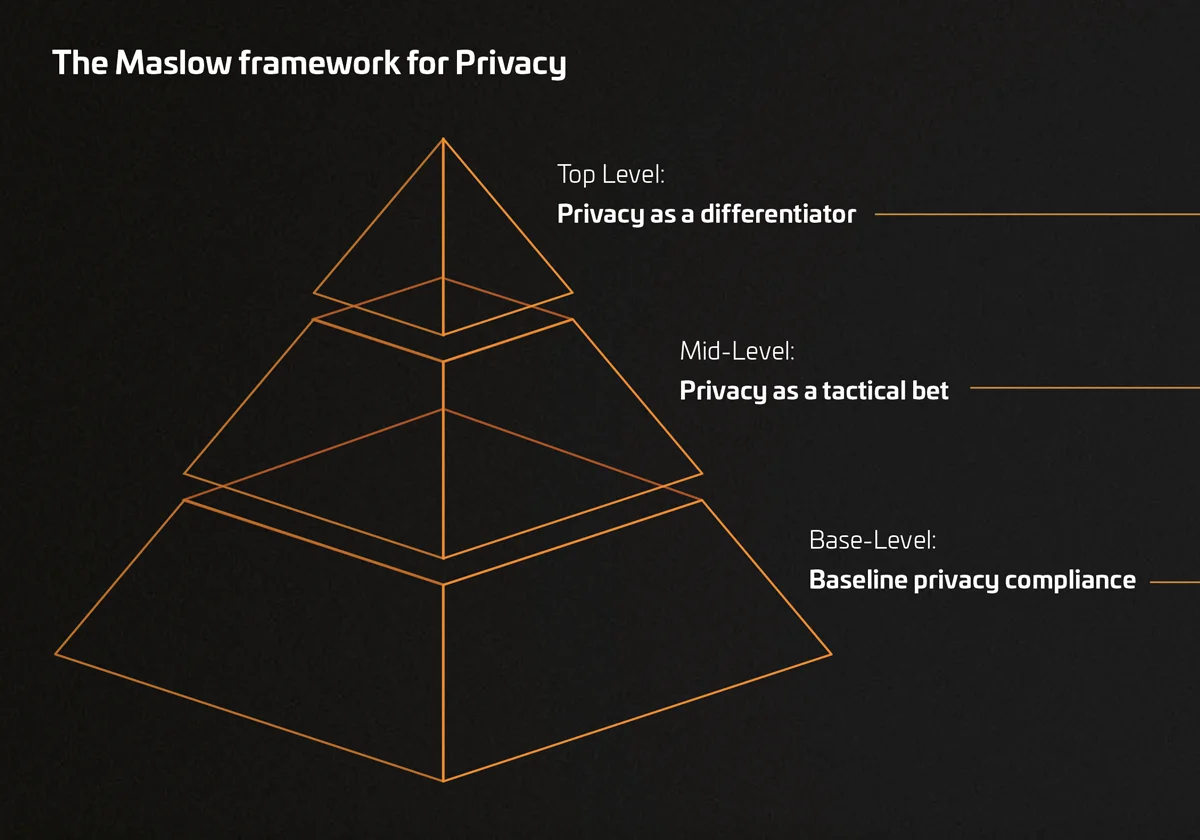
The Maslow framework for privacy
- Base-Level: Baseline privacy compliance: The pyramid's base represents the minimum standard of privacy practices that organizations must adhere to. At this level, the focus is on adhering to laws and regulations to avoid penalties and ensure basic privacy protections for consumers. This level of privacy, the bare minimum required of an organization.
- Mid-Level: Privacy as a tactical bet: Organizations at the mid-level view privacy not just as a compliance requirement but as a tactical asset. They start to anticipate the evolutions in the privacy landscape and try to evolve with them. The focus shifts to integrating privacy considerations into the broader business strategy. This approach might include more robust data protection measures or proactive privacy risk management and represents the rudimentary principles of a privacy-by-design approach.
- Top Level: Privacy as a differentiator: Organizations that fully embrace privacy as a core value and differentiator sit at the top of the pyramid. They care. These organizations go beyond compliance and strategically leverage privacy to distinguish themselves in the market. They reflect a genuine commitment to protecting user data and promoting trust. This means implementing privacy-by-design principles across all operations, innovating with privacy-enhancing features, and advocating for privacy rights.
Evolving from basic compliance to privacy as a strategic differentiator
Organizations that genuinely integrate privacy into their culture go beyond compliance – and will be rewarded for doing so. To evolve from essential compliance to privacy as a strategic differentiator, organizations should:
- Build a privacy practice: Recognize that privacy is not the same as security and develop a dedicated approach.
- Plan to be agile: The privacy landscape is fluid, with regulations constantly changing and evolving. As such, your approach to privacy must be agile and changeable.
- Adopt privacy-by-design technology: Ensure data protection and compliance is integrated into every stage of the digital lifecycle.
- Focus on the consumer: To achieve the top level of privacy, businesses must not treat it as a checkbox exercise, instead, they must focus on improving user experience and recognizing privacy's ability to be a differentiator.
Privacy can be a business enabler, a tactical asset, and a strategic differentiator—but only if you want it to be.
The privacy landscape and awareness around this concept shows no sign of slowing down. Implement a privacy-by-design program to stay on the right side of compliance consumers.

Keep Learning
Discover the Future of Identity Management
This article originally appeared in IAM 360, our magazine dedicated to exploring all aspects of identity and access management (IAM). Check out the latest issue for fresh perspectives, practical advice, and the latest news and trends in IAM.