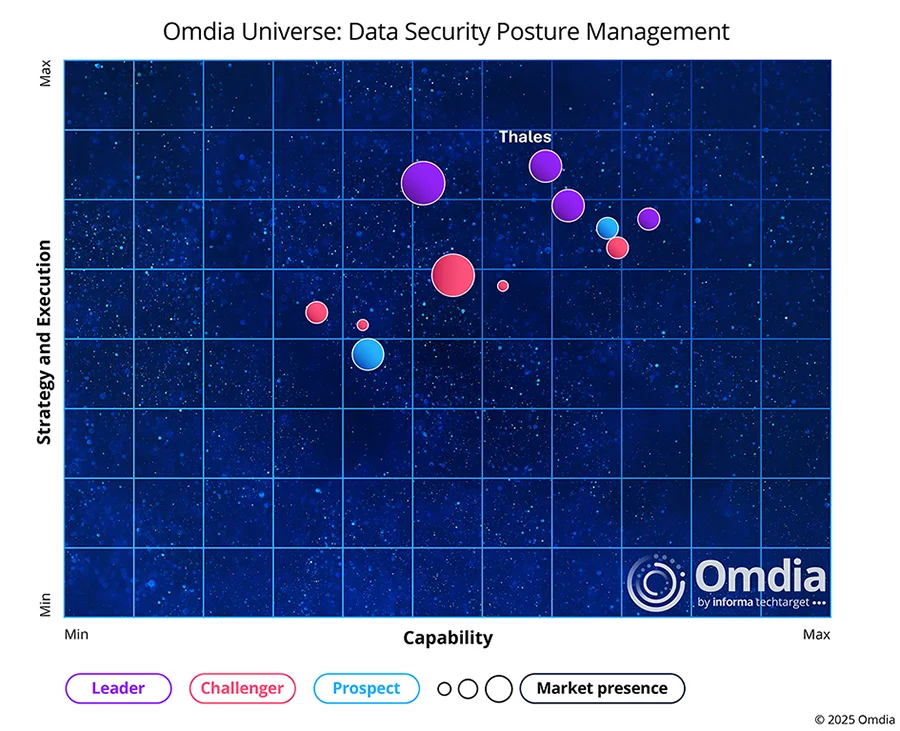
Thales eclipses other DSPM solutions
We're proud to be a Leader in Omdia Universe 2025
“Omdia assesses the Thales DSPM proposition as a Leader and with three ‘Best in Class’ ratings for core technology, momentum and execution, together with 2 other ‘Top tier’ ratings, the vendor has grown significantly over the last three years to become one of the premier DSPM and cybersecurity providers.”
Read Omdia’s assessment why Thales was named a leader for its DSPM capabilities and data security solutions, including:
- Key strengths in the scope and scale of not only its DSPM offering, but also in the entirety of its CipherTrust data security platform.
- Why Thales is considered unique in the IT market and it’s distinct edge
- How Thales uses its fundamental knowledge to protect customer environments and sensitive data
Thales' recognition as a Leader in the Omdia Universe: Data Security Posture Management Universe is well-deserved. Their comprehensive platform unifies data discovery, protection, and access controls with a precision that goes beyond basic security measures. With three 'Best in class' ratings for core technology, momentum, and execution, the organization has built on its defence heritage to deliver enterprise-grade data security that few competitors can match.

Strengthen your security posture
CipherTrust Data Security Posture Management
CipherTrust Data Security Posture Management precisely identifies the locations of your sensitive data, whether it's in the cloud, on-premises, or within SaaS applications.
Leveraging years of industry expertise, CipherTrust DSPM effectively detects, classifies, protects, and monitors interactions with your most valuable asset: your data.
Data Discovery & Risk Control
- Reign in data exposure due to rapidly expanding and fragmented data.
- Inventory your data estate through data discovery and classification of structured and unstructured data.
- Understand interactions with sensitive data and apply proper security controls.
- Address unknown vulnerabilities like ‘Shadow data’ and unmanaged data flows.
Security & Threat Protection
- Apply data protection, including encryption, and secure the metadata that makes it readable and usable.
- Build post-quantum-ready controls to counter future AI and quantum-powered threats.
- Halt data sprawl by limiting access to authorized audiences.
- Proactively detect external and insider threats through advanced analytics.
Governance & Compliance Automation
- Comply with strict data protection regulations (GDPR, PCI, HIPAA).
- Accelerate data governance with built-in automation.
- Build contextual insights and risk intelligence by integrating tools.
DSPM FEATURES
Gain the visibility, analytics and security needed to face today’s modern risks
Understand your data estate
Know where your data, especially sensitive data, lives and how users and entities interact with it:
- Identify structured and unstructured data across cloud SaaS, and On-premises with database activity monitoring and file activity monitoring.
- Classify data based on sensitivity and business value, while assessing risks.
- Pinpoint which accounts, applications, and APIs access sensitive data.
- Map data flows across repositories to ensure protection and informed decision-making.
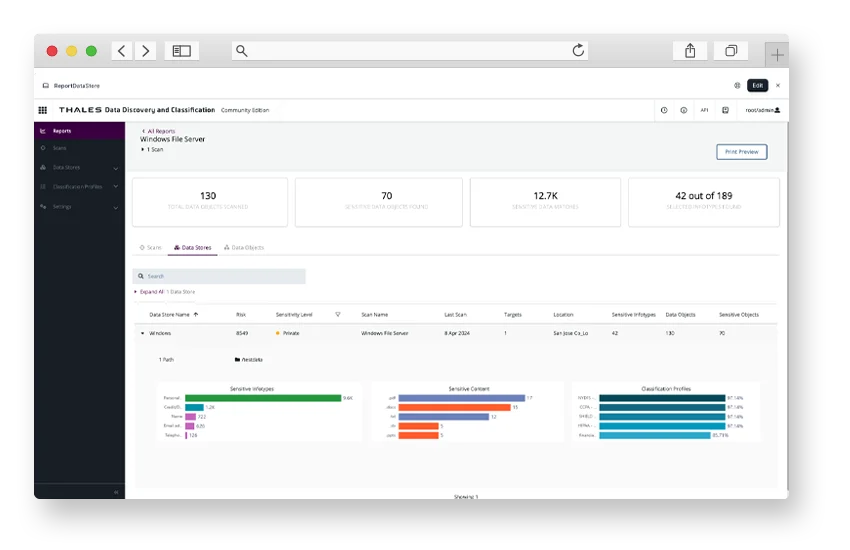
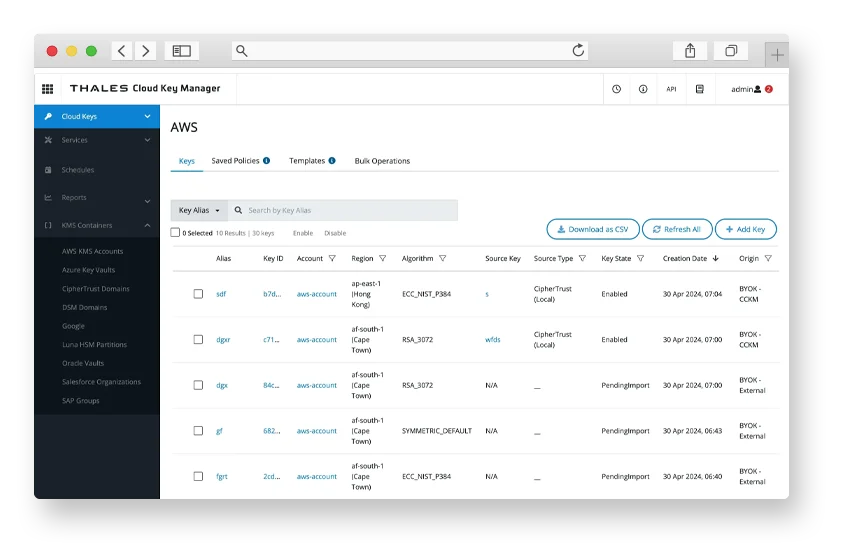
Fortify your data security posture
Protect your data from day one and identify where vulnerabilities and exposures exist:
- Implement strong encryption, masking, and tokenization to protect data at rest and in motion.
- Safeguard associated metadata, such as keys and secrets, to align with industry best practices.
- Track data movement through cloud services and monitor access patterns.
- Establish a post-quantum ready foundation to protect data against AI and quantum computer powered threats.
Continuously improve data security operations
Prioritize areas of risk and execute targeted action plans to improve data security:
- Identify exposures and vulnerabilities to mitigate them before cybercriminals take advantage.
- Ensure compliance with international regulations, privacy laws, and compliance frameworks.
- Promote policy-driven data governance.
- Prioritize security measures based on data risk assessments.
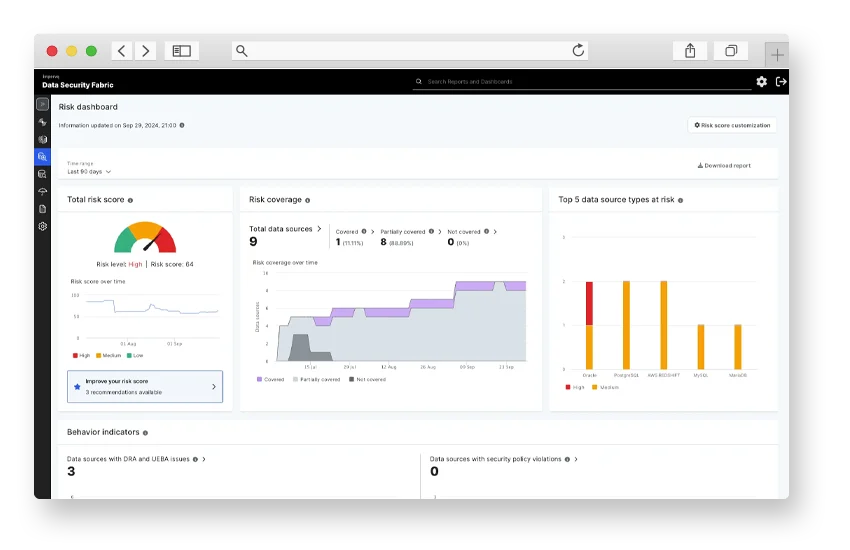
Read Omdia’s assessment why Thales was named a leader for its DSPM capabilities and data security solutions
