
Your Data. Their Cloud. Leveraging the Cloud without Relinquishing Control
In today’s organizations, digital transformation is a vital imperative—and cloud services offer a proven path to accelerate an organization’s repositioning to thrive in the digital economy. A successful digital transformation demands that organizations address security, privacy, and compliance objectives. This white paper looks at the factors driving the need to expand the use of cloud services, the critical security, privacy, and compliance objectives that organizations must address, and the core security capabilities required to leverage the cloud without relinquishing control.

As the cloud attack surface expands, organizations must get a firm grasp on the data they have stored in the cloud, the keys they’re using to encrypt it, and the ability to have complete visibility into who is accessing the data and how it is being used."
So, who is really responsible for cloud security?
Too many business leaders assume that cloud security is their Cloud Service Provider’s (CSP’s) total responsibility, which is a dangerous misconception. In reality, the CSP and the customer share responsibility – and ultimately fate.
This is called the Shared Responsibility Model, and it defines clear boundaries:
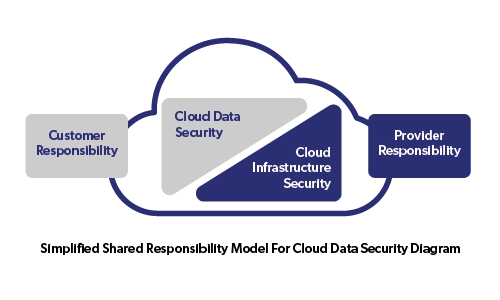
Cloud providers are responsible for securing the infrastructure
You are responsible for securing your data, applications, and user access
The Potential Security Gaps in Cloud Provider Protections
Businesses need to establish who controls their encryption keys, where they are stored, and, importantly, can they retrieve them if needed—or are they locked in by a cloud provider?
When it comes to data encryption, if your encryption keys are managed within the same cloud ecosystem, this could put your business at risk. Here's why:
Single Point of Failure
A breach of the cloud tenant could give attackers access to both the data and the keys protecting it. Bad actors with stolen credentials could potentially decrypt sensitive data. In fact, Insider and privileged account access was cited as a leading risk in the 2025 Thales Data Threat Report.
Regulatory Gaps
Compliance frameworks like GDPR, DORA, PCI-DSS, and the U.S. CLOUD Act now require stricter key control and clear proof of separation of duties. Data sovereignty requirements also mandate control over key management. Businesses must establish whether depending on a CSP meets these evolving regulations.
Lack of Separation of Duties
Security best practice dictates that the entity storing your data should not control the encryption keys. Relying on a CSP-managed encryption model creates a conflict of interest and makes your data security dependent on the cloud provider.
Multi-Cloud Complexity
For organizations using multiple cloud platforms, encryption processes and key management strategies differ between providers. Managing these fragmented systems increases the risk of human error, security gaps, and operational inefficiencies
Read why a successful digital transformation demands that organizations address security, privacy, and compliance objectives
