What is IAM?
IAM is a framework of policies, technologies, and processes that ensures the right individuals have access to the right resources at the right time and for the right reasons. These individuals can include employees and contractors (Workforce IAM), end users like customers or subscribers (Customer IAM, or CIAM), and external partners such as vendors or service providers [Business-to-Business (B2B) IAM].
It combines key functions like:
- Authentication: Verifying that a user is who they say they are
- Authorization: Granting or denying access based on user roles or policies
- Provisioning: Creating, managing, and removing user accounts
- Auditing and Reporting: Tracking and logging access for compliance and security analysis
In modern organizations, IAM plays a crucial role in enabling secure, seamless access to hundreds of systems spanning cloud and on-premises environments, across both internal and external audiences/
Employees, contractors, consumers, and partners interact with a wide range of tools daily – Salesforce, Microsoft 365, Google Workspace, Slack, Jira, ServiceNow, internal databases, VPNs, and more. IAM systems streamline access to these resources while maintaining control and visibility in the background.
For example, when an employee joins a company, their digital identity is created and provisioned with appropriate roles. As they access tools like email, internal dashboards, or project management systems, the IAM system authenticates them, applies access policies, and grants access accordingly. Similarly, a customer creating an account on a retail app or a supplier accessing a logistics platform is authenticated, authorized, and monitored using the same IAM principles.
This unified approach replaces manual provisioning, reduces reliance on insecure password habits, and ensures that access privileges are consistent and auditable across systems.
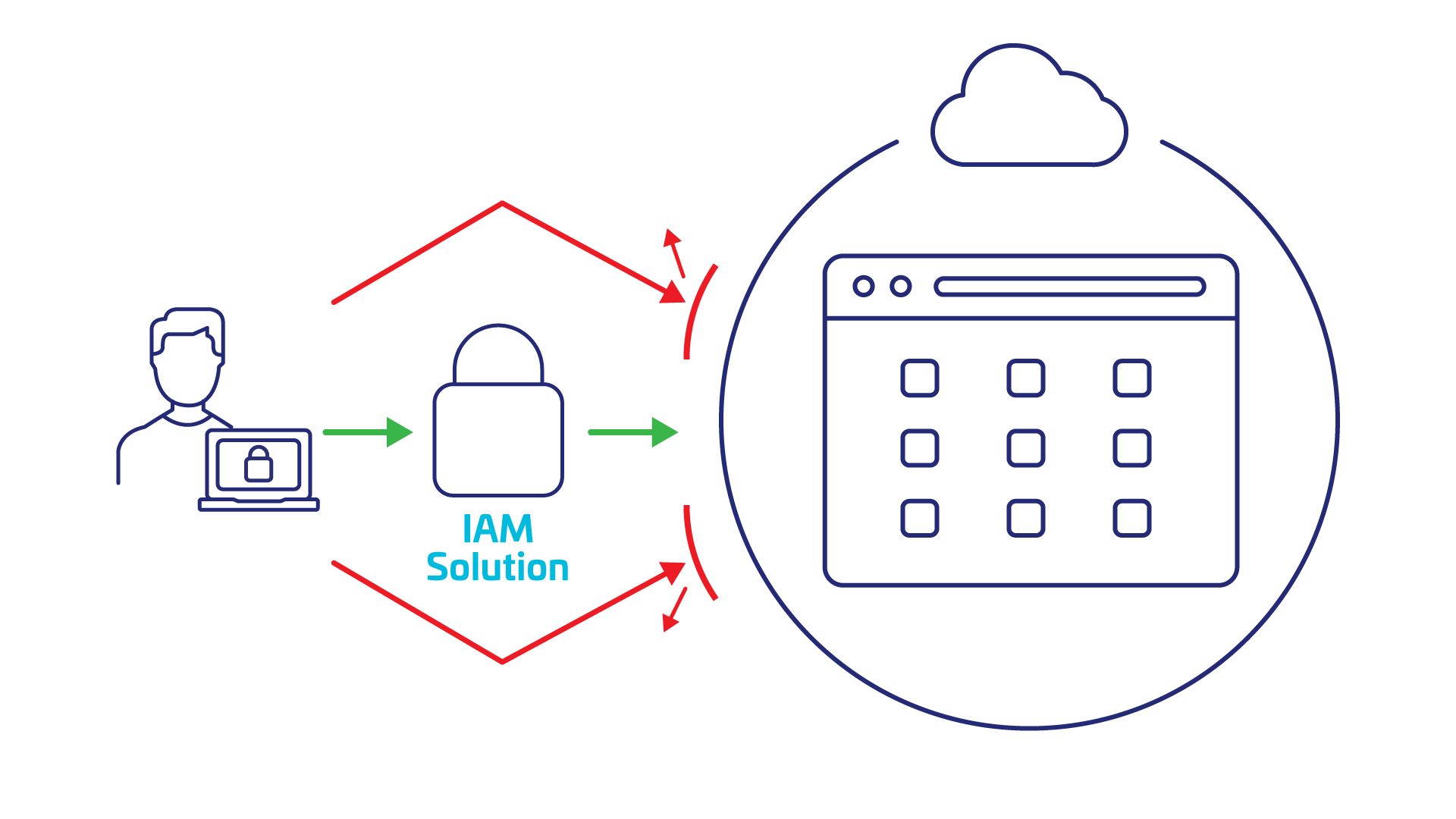
Why is IAM Important?
IAM has never been more important. Remote work, regulatory scrutiny, data breaches, and cyberattacks are all on the rise. IAM is no longer just an IT concern; it’s a business necessity.
As traditional network perimeters dissolve, identity has become the new perimeter. Users now connect from anywhere across a mix of cloud services and on-prem systems, often using personal or unmanaged devices. In this environment, the most effective way to protect sensitive data and systems is to verify who someone is, what they should have access to, and under what conditions.
Today’s organizations must secure both cloud environments and legacy infrastructure that’s unlikely ever to move off-premises. IAM bridges these worlds, delivering both strong security and a smooth user experience for all user types – ranging from internal teams to customers and business partners.
The Challenges Driving IAM Adoption
Fragmented IT Environments
Most organizations now use a mixture of cloud services and on-premises applications. Internal databases, VPNs, and line-of-business applications remain vital, especially in industries like banking and critical infrastructure. Similarly, customer-facing services and partner integrations often reside in the cloud, requiring IAM systems to unify across internal and external environments.
Without unified identity governance, managing access becomes complex and inconsistent.
Lack of Legacy System Support
While cloud IAM platforms have advanced rapidly, many still struggle to cover legacy systems that can’t be migrated. For mature or regulated industries, these systems are non-negotiable. They still require strong authentication, policy enforcement, and auditability, but are often left behind in cloud-first IAM strategies. This is true for both internal systems and legacy customer-facing applications that remain critical to service delivery.
Overreliance on Passwords
Despite the rise of more secure methods, passwords remain the most common authentication mechanism. They’re also one of the weakest. Users forget them, reuse them, or store them insecurely. Even one compromised password can open the door to sensitive systems. This challenge spans employee accounts, customer logins, and third-party access points.
Misaligned Security Controls
One-size-fits-all authentication doesn’t work across varied users, devices, and data types. Some users need high-assurance controls like step-up authentication, while others benefit from low-friction access to low-risk systems. IAM enables adaptive security policies for different identity types – ranging from privileged admins to everyday customers.
Evolving Workforce and Access Models
Remote work, BYOD policies, and the growth of third-party access mean that traditional perimeter-based access models no longer suffice. Users now expect secure access from anywhere, on any device, at any time. This also applies to customers accessing mobile apps and APIs, as well as vendors collaborating via shared systems.
Increasing Regulatory Demands
Regulatory frameworks like PCI DSS, ISO 27001, and NIS2 require organizations to apply strong access controls, protect sensitive data, and maintain audit trails. CIAM and B2B IAM play a critical role here, ensuring external access also complies with industry and regional regulations.
Core Benefits of IAM
- Enhanced Security: By centralizing authentication and authorization, IAM provides a single control point to enforce consistent security policies. This includes mandating stronger authentication methods and applying conditional access rules, significantly reducing the risk of credential compromise across all user types.
- Better User Experience: IAM enables frictionless access to the systems users need to do their jobs, without unnecessary logins or confusing processes. This leads to higher productivity and fewer support requests. It also improves customer satisfaction by enabling smooth, secure login experiences.
- Streamlined Operations: IAM can automate user provisioning, deprovisioning, and access reviews, significantly reducing the workload for IT and security teams. IAM streamlines user lifecycle management and helps ensure accounts don’t remain active longer than they should. This applies not only to employees, but also to onboarding and onboarding customers and partners.
- Support for Modern and Legacy Environments: IAM allows organizations to manage access across both cloud and on-premises infrastructure, ensuring that legacy systems are not left out of modern security policies. This includes legacy systems that underpin customer services or third-party workflows.
How does IAM Work?
At its core, IAM is about ensuring that the right people - and only those people - can access the right systems and data. It does this by managing the whole identity lifecycle, from account creation to access enforcement and eventual deactivation. Here’s what that process usually looks like:
- User Enrollment: Whether it’s a new employee, a customer signing up through a mobile app, or a partner being granted limited access, each identity is enrolled and assigned attributes such as role, group, or permissions.
- Authentication: When users attempt to log in, the system verifies their identity. This might involve something they know (like a password), something they have (like a security token), or something they are (like a fingerprint).
- Authorization: Once verified, IAM determines what the user is allowed to access based on their role, risk level, and context (such as device type or location).
- Access Enforcement: IAM enforces access decisions in real time, granting or blocking access to specific systems, apps, or data.
- Monitoring and Auditing: Every access attempt is logged. Security teams monitor unusual activities and organizations can generate reports for compliance and governance purposes. This applies equally to internal systems and public-facing applications.
Key Components Involved
IAM solutions consist of several components that work together to create secure and seamless access experiences across environments.
Identity Management
- Identity Directory: A central repository storing user identities across workforce, customer, and partner populations.
- Identity Lifecycle Management: Automates the full lifecycle – from onboarding and role changes to deprovisioning – whether for employees joining via HR systems or customers registering via web or mobile apps.
- Identity Federation and IdP Support: Enables seamless login experiences across enterprise and customer-facing systems using standards like SAML or OpenID Connect (OIDC). It connects disparate domains, such as workforce systems, partner portals, and customer apps, through trusted identity providers.
Authorization & Access Management
- Role-Based Access Control (RBAC): Provides structured, policy-based access by assigning permissions based on predefined rules. This applies to employee functions, customer subscription tiers, and vendor access entitlements.
- Attribute-Based Access Control (ABAC): Enhances flexibility by incorporating dynamic attributes – such as location, device type, or department – to determine access, allowing for more granular and context-aware policy enforcement.
- Privileged Access Management (PAM): Complements RBAC by securing elevated or sensitive roles. PAM is critical for protecting administrative access for internal staff and also plays a key role when granting temporary or high-risk access to partners or third parties. It ensures such access is tightly controlled, monitored, and time bound.
- Fine-grained Authorization: Enables highly specific access controls at the resource or action level. This approach goes beyond traditional role-based models to enforce detailed permissions, such as limiting a user’s ability to view, edit, or share particular data, based on contextual factors or business rules.
Authentication
- Single Sign-On (SSO): SSO lets users log in once and access multiple applications without having to authenticate again. It reduces password fatigue and improves user experience.
- Multi-Factor Authentication (MFA): MFA adds extra layers of protection by requiring a second (or third) form of verification, such as a push notification, token, or biometric, before granting access.
- Passwordless Authentication: This approach replaces traditional passwords with stronger, phishing-resistant options like FIDO keys, smart cards, or facial recognition.
Auditing, Monitoring, & Governance
- Identity Governance & Administration (IGA): Oversees access reviews, certification, and policy compliance across the user spectrum – including contractors, customers, and partner identities.
- Access Log Analytics: Captures detailed logs of who accessed what, when, and how, which is essential for investigating anomalies and maintaining compliance across workforce, CIAM, and third-party domains.
More of a hands-on person? Try Thales identity security for free
Test out our adaptive and risk-based approach to authentication and access management in your own environment for 30 days at no cost to you.
Industry Spotlight: BFSI
Why IAM Matters in Banking, Financial Services, and Insurance (BFSI)
While all sectors face pressure to secure access, it’s especially important for BFSI organizations. They handle sensitive personal and financial data, operate under intense regulatory scrutiny, and are prime targets for cyberattacks. At the same time, they must offer fast, seamless services to employees, customers, and third-party partners, often across a complex mix of cloud and legacy systems.
IAM provides the foundation to meet these competing demands, offering the visibility, control, and scalability that BFSI organizations need to operate securely and efficiently.
- High Security Expectations: Customer trust is both essential and fragile. A single compromised login or access misconfiguration can lead to financial loss, reputational damage, and regulatory penalties. IAM reduces these risks by enforcing consistent access policies across all systems.
- Growing Regulatory Requirements: BFSI organizations must comply with strict regulatory requirements, including emerging data sovereignty laws. IAM supports compliance by enabling role-based access control (RBAC), multi-factor authentication, audit logging, and enforcement of least-privilege principles. Relevant standards and frameworks include:
- Global:
- ISO/IEC 27001 and 27002
- SWIFT CSCF
- United States
- FFIEC Guidelines
- GLBA and FTC Safeguards Rule
- Europe
- PSD2/PSD3
- DORA
- Global:
- Hybrid Infrastructure: Many BFSI organizations still rely on mainframes and legacy apps that aren’t going anywhere. The best IAM solutions support both modern SaaS tools and on-premises systems, ensuring security and continuity across the entire environment without disrupting business-critical workflows.
- Changing Workforce Models: Remote and hybrid work models mean financial services teams need secure, flexible access to tools and data from anywhere. IAM enables strong authentication and contextual access control across locations, devices, and network environments.
- Customer-Facing Security: IAM secures customer-facing platforms such as mobile apps and online banking portals, enabling fast yet compliant digital experiences.
What to Look for in an IAM Solution
Not all IAM platforms are created equal. While the core goal – managing identity and controlling user access – remains the same, the way different solutions approach that goal can vary significantly. When evaluating an IAM solution, look for one that offers security without friction, flexibility without complexity, and visibility without blind spots.
Here are the key capabilities to look for.
Hybrid Support for Cloud and On-Prem Environments
A modern IAM tool should secure access to SaaS, cloud-native, and legacy on-premises applications. This is especially critical for organizations with longstanding infrastructure that can’t easily be replaced or migrated. Look for platforms that integrate with both modern and legacy systems without requiring parallel toolsets or creating silos.
Flexible, Risk-Based Authentication
Different users, devices, and applications require different levels of assurance. Your IAM solution should support a broad range of MFA methods and be applied intelligently based on risk, context, and compliance needs.
Passwordless Capabilities
Reducing reliance on passwords improves the user experience and removes one of the most common attack vectors. Prioritize support for phishing-resistant methods like FIDO2, biometrics, and certificate-based authentication.
Centralized Policy and Access Control
Your IAM solution should let you define and enforce consistent, granular access policies across your environment. Conditional access based on role, location, device type, or behavioral risk scoring ensures only the right people have access to the right resources under the right conditions.
Seamless User Experience
User-led enrolment, SSO, and context-aware access help reduce login fatigue and minimize support tickets. IAM should empower users to access what they need securely and without disruption.
Compliance-Ready Logging and Visibility
Built-in logging, reporting, and SIEM integration will allow you to monitor access attempts, investigate anomalies, and meet audit requirements. This is particularly important for regulated industries like BFSI, healthcare, and government.
Standards-Based Interoperability
Choose IAM solutions that support standard protocols – such as SAML, OIDC, and SCIM – and integrate cleanly with HR systems, customer identity providers (like social logins), and partner logins. Avoid rigid solutions that can’t evolve with your identity landscape.
Resilience and Continuity
IAM should remain operational even during outages. Features like fallback authentication and high-availability architecture ensure users can still access critical features without disruption.
Secure Access, Seamless Experience
Having the ability to manage who can access what and under what conditions is a necessity.
IAM is the foundation of secure, seamless operations. It ensures that only the right individuals have access to the right resources at the right time, without creating barriers to productivity. It helps security and IT teams ensure consistent policies, reduce human error, and gain complete visibility into user behavior across environments.
For high-risk sectors like banking, financial services, and insurance, IAM offers the control, flexibility, and auditability needed to balance access and assurance.
IAM doesn’t just streamline access – it drives productivity, collaboration, and trust. It empowers employees to do their jobs without friction, frees IT teams from manual provisioning and constant credential headaches, and enables seamless, secure collaboration with third parties. For consumers, it builds trust by ensuring their data is protected and their experience is smooth.
Ultimately, IAM is about more than who gets access; but how, when, and why. That’s what makes IAM essential to secure, resilient business operations.


