 David Ortega | Principle Solution Architect
More About This Author >
David Ortega | Principle Solution Architect
More About This Author >
 David Ortega | Principle Solution Architect
More About This Author >
David Ortega | Principle Solution Architect
More About This Author >
It started with a well-meaning mistake.
Bernie, a project manager at a mid-Atlantic regional health provider, was coordinating a data science initiative with an external partner. As part of the collaboration, sensitive patient and business data was uploaded to a data lake hosted by a major Cloud Provider.
Unfortunately, the external partner mishandled the credentials needed to access that data. To streamline access, the partner emailed the credentials to their own database team. Those credentials were then copied into a shared project folder on the partner's cloud storage drive—publicly accessible without their knowledge.
A bot, commonly used by cybercriminals to crawl and index open file shares, found the exposed folder. It parsed the text, flagged the credentials, and a hacker quickly gained unauthorized access to the health provider’s cloud data lake.
Within hours, the attacker logged into the cloud-hosted database, using the compromised credentials. The permissions tied to the credentials were extensive—administrator-level. The activity appeared legitimate to monitoring systems. No alarms were triggered.
The attacker moved silently and efficiently. Gigabytes of sensitive data were exfiltrated, including customer payment card information (PCI), employee social security numbers (PII), and confidential financial documents. Because the stolen credentials had the necessary privileges, the attacker was able to decrypt the data at rest. No data loss prevention (DLP) systems caught the activity.
Then came the note.
It appeared simultaneously on every company computer screen:
“Your data has been copied. Pay 500 Bitcoin within 72 hours, or we release it all.”
It was signed by a well-known ransomware group. Attached were screenshots—real data from the compromised database—to prove their claim.
The leadership team froze. Legal was on the phone with the FBI. PR scrambled to draft a disclosure. The CISO stared at his screen, stunned by how a single lapse could spiral into disaster.
And Bernie—who had only wanted to keep the project on schedule—sat quietly in the war room, eyes locked on the floor, as chaos spread around him. The company was paralyzed. Its operations, reputation, and digital sovereignty had all been compromised.

The situation at Bernie’s company can happen easily and quickly. The Thales 2025 Data Threat Report cited “In 2024, a large national healthcare provider was the victim of ransomware, resulting in the theft of medical, billing, and personal records of a substantial proportion of the American population. The attackers demanded a ransom in exchange for the return of the stolen data.”

What is Data Sovereignty?
Data sovereignty means an organization's right to control and regulate data generated and owned by the organization, ensuring that data is protected and kept confidential subject to the organization’s applicable laws and regulations. This principle also extends to individuals and groups who have the right to control their own data, including its collection, storage, and interpretation. In the context of organizations, it means complying with data privacy and sovereignty laws in the various countries where they operate and ensuring that, through privacy and confidentiality, businesses can operate securely.
What is Data Privacy?
Data privacy is the practice of keeping data confidential and outside the purview of unauthorized entities. Data privacy includes how organizations collect, store, and use nonpublic data. It ensures that personal data is protected from unauthorized access, misuse, and theft.
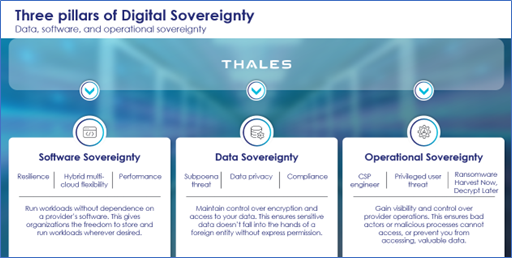
How do they tie together?
Digital sovereignty and data privacy are not mutually exclusive; instead, they are complementary approaches to data protection. Digital sovereignty provides the legal and policy framework for controlling data, while data privacy focuses on protecting data in use, while using technical controls to enforce, mitigate risk, and ensure compliance, even when data is being processed, that is while data is in use.
How do these apply to you?
Organizational Data Protection Custodians, InfoSec professionals, and Cyber Security Officers face many challenges in protecting the privacy of their sensitive and nonpublic organizational data. Further complicated by changes in international diplomatic relationships and changing administrations, public and private sector, nonpublic data has never been under greater threat. The challenge of keeping data private continues to grow. Rarely does a week go by without news of another massive data breach, exposing the sensitive information of millions.
The Threat
These incidents, like the recent breach at a large healthcare provider, underscore a sobering reality: current data protection measures are often inadequate. Adding to this complexity is the ever-evolving web of privacy regulations, with governments worldwide enacting stricter rules about how data must be handled. Concerns about keeping citizen data private have led to regulatory actions such as GDPR and CCPA, although regulatory action cannot protect the data from being accessed improperly.
Failure to be Compliant, Manage Privacy, Sovereignty and Mitigate Risks
The importance of digital sovereignty has grown exponentially in our globalized digital economy. Data flows seamlessly across borders, fueling innovation and economic growth. However, this interconnectedness also creates vulnerabilities and complexities. Organizations operating internationally often face conflicting data privacy laws and regulations. For example, the European Union's General Data Protection Regulation (GDPR) grants individuals’ significant rights over their data, while other countries may have less stringent requirements. The Schrems II decision further complicated matters by raising concerns about data transfer to countries with inadequate data protection laws. Digital sovereignty provides a framework for navigating this complexity, enabling organizations to comply with local regulations and avoid legal conflicts.
Thales Solution for Data Privacy and Governance
While digital sovereignty focuses on where data is stored and processed, data privacy addresses how data is protected in storage, in transit and during processing. In traditional computing, data is decrypted when processed, making it vulnerable to attack. Confidential computing and field-level protection strategies mitigate this risk by performing computations within a hardware-based Trusted Execution Environment (TEE) or based on conditional reveal and decryption policies.
A TEE is a secure enclave within a processor that provides a protected environment for executing code and processing data. Data is encrypted before it enters the TEE and decrypted only within the TEE itself. This means that even if the operating system or hypervisor is compromised, the data within the TEE remains protected. Confidential computing also involves attestation, which verifies the integrity of the TEE and ensures that the code running within it is authorized. This helps prevent tampering and ensures that the data is processed in a secure and trustworthy environment.
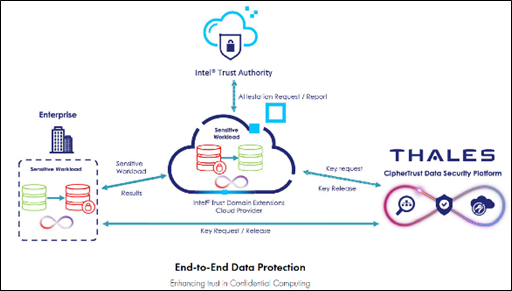
The benefits of confidential computing are significant. It protects sensitive data from a wide range of threats, including insider attacks, privileged access abuse, and vulnerabilities in the underlying infrastructure. It also enables organizations to securely process and analyze data in multi-party collaborations without exposing the raw data to each other.
In addition to confidential computing, organizations must implement strict controls to keep data private at rest and private at the time of use unless provided a valid attestation. Organizations face the challenge of protecting sensitive data at rest and during use. Field-level protection strategies offer a granular approach to data security, ensuring that specific data elements are secured according to their sensitivity and usage policies. Tokenization, format-preserving encryption (FPE), and data masking are key techniques in this approach.
Tokenization replaces sensitive data with unique, randomly generated tokens. These tokens have no intrinsic value and are useless to attackers, effectively safeguarding the original data. The data is stored in a secure vault, and access to this vault is strictly controlled. Tokenization is widely used to protect credit card information and other sensitive personal data, allowing for secure processing without exposing the underlying sensitive values.
Format-preserving encryption (FPE) is a specific encryption technique that transforms data into ciphertext while maintaining its original format. This is crucial for ensuring compatibility with existing systems and applications that rely on specific data formats. For instance, an encrypted credit card number can retain its original length and digit structure. FPE enables strong encryption while minimizing disruption to business processes.
Data masking, on the other hand, obscures sensitive data by replacing it with altered values. This can involve character substitution, shuffling, or using realistic, fictitious data. Masking is often employed in non-production environments, such as development and testing, to protect sensitive information while allowing for realistic data manipulation.
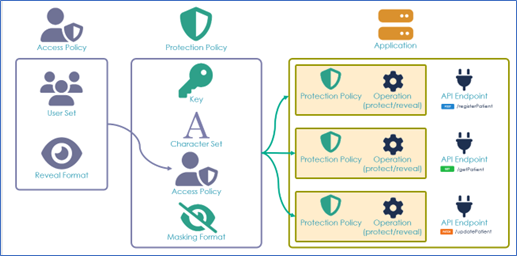
Implementing these field-level protection strategies can help organizations enforce fine-grained control over data access and usage. Data can be stored at rest using strong encryption or tokenization. Then, based on predefined policies, it can be dynamically masked, partially revealed, or fully decrypted at the time of use. This ensures that sensitive information is only accessible to authorized personnel and for legitimate business purposes, enhancing data security and privacy.
How Thales Helps with Data Privacy and Governance
Organizations can achieve a more robust and comprehensive data protection strategy by combining these two approaches. For example, an organization might store its data in a data center located in a specific country to comply with data sovereignty regulations. It could then use data privacy strategies to process that data, which is decrypted and used in a secure enclave, ensuring it remains protected even during processing. Combined with the use of field-level encryption strategies, organizations will have a strong defense against legal and technical data privacy threats.
Implementing this combined approach requires careful planning and execution. Organizations must develop a comprehensive data governance framework that addresses data protection's legal and technical aspects. They must also choose cloud providers or technology partners supporting digital sovereignty principles and confidential computing capabilities. This may involve evaluating data residency options, security certifications, and support for specific TEE technologies. Furthermore, organizations must implement robust encryption and access control mechanisms to ensure data is protected throughout its lifecycle.
Summary
The importance of data privacy will only continue to escalate. New and evolving data privacy regulations are constantly being introduced worldwide, reflecting a growing recognition of the value of data and the need to protect individual rights. Simultaneously, cyberattacks are becoming more sophisticated, with malicious actors constantly seeking new ways to exploit vulnerabilities and steal sensitive information. Furthermore, there is a growing public awareness and concern about data privacy, with individuals demanding greater control over their personal information.
Digital sovereignty, confidential computing and protecting data in use will become increasingly essential for organizations in this context. Organizations prioritizing these concepts will be better positioned to maintain a competitive advantage by building customer trust, ensuring long-term compliance, and avoiding costly penalties. Moreover, these technologies will enable organizations to foster innovation while safeguarding sensitive information, allowing them to explore new opportunities without compromising privacy.
In conclusion, the path to robust data privacy and protection in the digital age requires a multi-pronged approach. Digital sovereignty provides the necessary framework for organizations to control where their data is stored and who has access to it, aligning with legal and regulatory requirements. Confidential computing and field level data protection strategies ensure that data remains protected even when being processed, mitigating the risks associated with data in use and ensuring privacy.
View our Data Protection Solutions Webpage to learn more about how data protection solutions enable you to be more secure and compliant.