With penalties as high as $500k a new Florida law, effective July 1, adds big teeth to the state’s data breach notification statute. One of the most interesting changes redefines the concept of ‘personal information.’
The new Florida Information Protection Act of 2014, states an organization must provide written notice to the state attorney general no later than 30 days after determination that a breach affecting 500 or more Floridians has occurred, down from 45 days in an earlier law.1
<ClickToTweet:> In the wake of recent attacks, @Vormetric report provides legal obligations to prep for the next encryption battle. bit.ly/1kFJjRF
Here is a quick rundown of some of the important aspects of the report3.
Florida’s definition of personal information:An individual’s first name or first initial and last name in combination with any one or more of the following data elements for that individual:
- Social security number
- Driver license or identification card number, passport number, military identification number or other similar number issued on a government document
- Financial account number or credits/debit card number in combination with any required security code, access code, or password that is necessary to permit access to an individual’s financial account.
- Any information regarding an individual’s medical history, mental or physical condition or medical treatment or diagnosis by a health care professional.
- An individual’s health insurance policy number or any unique identifier used by health insurers to identify the individual
- A username or email address, in combination with a password or security question and answer that would permit access to an online account.
Though Florida’s law brings cracking down on security policies to an entirely new level, we have read countless stories about cyber threats pushing all states to crack down on covert surveillance, security breaches and data loss, just to name a few. This ‘countlessness’ has created a global awakening in the minds of the public. This in turn has prompted law makers and regulators alike to become increasingly engaged in implementing new legal frameworks while defining new obligations for data security.
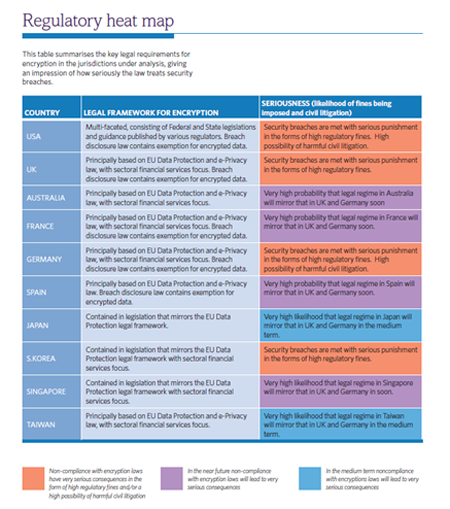
Examining the legal and regulatory obligations to encrypt personal data in three of the major economic regions of the world: Asia-Pacific region (Singapore, South Korea, Japan, Taiwan and Australia), European Union (United Kingdom, France, Germany and Spain) and the US, I’ve found the laws in these jurisdictions give rise to a clear need to deploy encryption technologies to protect personal data.
As the world progresses from a mere “information age” into an age of “big data”, it is a simple truism that the volume, granularity and sensitivity of individual data will grow exponentially. With this growth comes severe risks and consequences of losing that data. Keeping this in mind, and reflecting on the trends that developments in data security law have shown to date, we will undoubtedly see the law becoming even more prescriptive over time. Let’s face it, in the wake of recent attacks like those at Target, concerns about data security awareness – or, more accurately, the lack thereof –over the past twelve months has drawn significant attention. While encryption is a critical weapon in the data security battle, organizations must cast a wider net and take legal obligations into account.
Legal Framework: Encryption in APAC
Australia
The Privacy Act 1988 is the core legislation in Australia and, in December 2012, the Australian Parliament passed the Privacy Amendment (Enhancing Privacy Protection) Act 2012 (the Privacy Act). Principle 4 provides that ‘an organization must take reasonable steps to protect the personal information it holds from misuse and loss and from unauthorized access, modification or disclosure.
Japan
The Japanese Act on the Protection of Personal Information (APPI) applies to organizations (or information handlers) who utilize their databases containing personal information relating to 5000 or more individuals. Article 20 of the APPI includes an express obligation to take “necessary and proper measures for the prevention of leakage, loss, or damage and for other control of security of personal data”.
South Korea
The Personal Information Protection Act (PIPA) is one of the strictest data protection regimes in the world. It is also supported by sector specific legislation such as the Act on Promotion of Information and Communication Network Utilization and Information Protection (the IT Network Act) and the Use and Protection of Credit Information Act (UPCIA).
Singapore
The Singapore Personal Data Protection Act (PDPA) was passed in 2012. The Commission issued advisory guidelines in the PDPA that requires organizations to protect personal data in its control by making “reasonable security arrangements to prevent unauthorized access, collection, use, disclosure, copying, modification or disposal or similar risks”.
Taiwan
In 2010, the Computer Processed Personal Data Protection Law (CPPL) was renamed and amended to create the Personal Data Protection Act (PDPA) and increased obligations on companies, individuals and public organizations, including in relation to security. In addition, Article 12 of the Enforcement Rules of Personal Data Protection Act provided for by the PDPA set out specific security measures which private entities can use to protect personal data.
Legal Framework: Encryption in the EU
As I mentioned in my previous blog post, the EU data protection regime is built around the Data Protection Directive 1995 and the Privacy and Electronic Communications Directive 2002 (ePrivacy Directive). In considering the legal framework for encryption, it is important also to consider the new EU Payment Services Directive (PSD 2).
- Data Protection Directive 1995:Sets the overarching framework for data protection in the EU, and applies to data controllers (i.e. the organizations that determine how and why personal data is processed) that process “ personal data” about living individuals.
- ePrivacy Directive:The ePrivacy Directive applies specifically to the electronic communications sector and to the processing of personal data in electronic communications systems. The ePrivacy Directive also places a number of significant obligations on organizations for the purposes of improving data security.
- Payment Services Directive:The current EU directive on payment services provides the legal foundation for the creation of an EU-wide single market for payments, and applies to firms providing payment accounts, executing payment transactions, issuing payment instructions and providing money remittance services.
Legal Framework: Encryption in the USA
In contrast with the EU, the US data protection regime is based on a ‘ sectoral model,’ meaning that personal information is protected by various laws applicable to particular industry sectors. As a result, organizations must comply with a complex web of laws. With that said, the trend is clear: growth towards encryption is occurring in many sectors and in many US states.
In 47 states, breach disclosure laws currently provide a ‘ safe harbor’ against compulsory disclosures of security breaches where data is protected by encryption. Similarly, the proposed Consumer Bill of Rights (which reflects the US government’s view on privacy) sets out a number of principles which should apply to personal information in online settings. This includes the principle of ‘ security’ which states ‘all consumers have a right to secure and responsible handling of personal data’.
State Level Breach Reporting and Data Security Law
Data protection law in the USA is not only sector-specific but also state-specific and the majority of states have data breach notification laws in place. The state of California, for instance, is regarded as one of the leading regulators in this area, whose laws are regulated and enforced by the Department of Justice’s Privacy Enforcement and Protection Unit. California’s new privacy law introduces a requirement for any company conducting business in California which owns computerized personal data to notify Californian residents of any actual or suspected security breach that compromises the “ security, confidentiality or integrity” of the information, unless the data has been encrypted.
Federal Laws
In the realm of data security, some of the most significant federal laws include HIPAA, Gramm-Leach-Bliley, FCRA, FISMA, Cybersecurity Executive Order and NIST Developments (additional information below), Federal Information Security Amendments Act of 2013 and PCI-DSS.”
Cybersecurity Executive Order and NIST Developments
In February 2013 the White House, in collaboration with NIST, issued Executive Order 13636 entitled ‘ Improving Critical Infrastructure Cybersecuritydesigned to improve the cybersecurity of critical infrastructures in the USA. The Order builds on NIST’s development of cybersecurity technical standards and requires, among other things, for NIST to be responsible for leading the development of the Cybersecurity Framework in the US (the Framework), intended as a best practice guide for banking, defense, utilities and other industries to help protect against cyber-attacks.
Conclusion
Targeted attacks, APTs, and malicious hacks are showing no signs of abating – and this threat landscape has not gone unnoticed. In the US and the EU, the development of national cyber security strategies has highlighted the need to implement real-time access control measures to ensure data can be accessed by only authorized users and have in place pattern recognition technologies to capture intelligence to identify anomalous processes and access patterns.
As far as data security law is concerned, the legal obligation is to act reasonably. When the law is viewed in this way, it becomes easy to understand that a key part of acting reasonably is surveying the technological landscape. Clearly, the use of encryption technologies and access control, authentication and pattern recognition solutions form part of the answer. Along with this, we’ll also see mandatory post-breach transparency, tougher penalties and sanctions and an increase in regulatory guidance to provide organizations the ultimate key to exceed compliance requirements, reduce risk and prevent future breaches.
References