Back in April 2013, we investigated the motivations behind IT security spending. Our global online survey, targeted at IT professionals, found that newer IT trends – such as big data, cloud, BYOD and mobile security practices – were major security spending drivers. The survey gathered responses across a full range of markets – banking/financial services, retail, manufacturing, public sector and others. At the time, about 16 percent of respondents selected ‘data breaches’ as the primary data security driver at their organization.
Willing to bet some things have changed since then? We are.
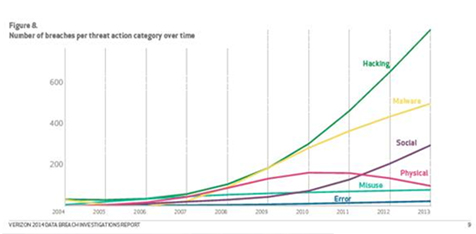
As Verizon’s latest data breach report makes clear, data breaches are rapidly increasing – and they’re the type of data breaches that should worry an IT department, not the Head of Security at the local Macys. Some of the more prominent data breaches you may have heard about include those at Target, Nieman Marcus, Staysure Travel, Snapchat, eBay and Adobe.
How does 432 million sound to you? Pretty good if it’s being deposited in your bank account, not so good if it’s the number of hacked accounts CNNMoney and the Ponemon Institute have accounted for based on data from the Identity Theft Resource Center and CNNMoney’s review of corporate disclosures. The hacked accounts in question also include companies, not just Joe A. Smith down the street. And even worse: this number, released in May of 2014, only tracked data breaches during the prior 12 months. Suffice it to say, there have been additional breaches since then.
So, what can you do to protect your company from being part of a Ponemon statistic? For starters, the key word here is “data.” Standard firewalls, AV and network monitoring solutions won’t be enough to guard against attacks. That said, we’re not recommending you stop using these solutions. We’re just suggesting you get a little more creative – just like the hackers that have turned data breaches into an art.
The addition of a data-centric security practice within your IT Security protection set is the best way to do this. Regardless of the solution that you choose, this includes the following elements:
- Encryption of data on servers regardless of location or application
- Application data tokenization, data masking or encryption that obscures data even within application environments, big data implementations and cloud deployments
- Access control that allows you to limit who can see data that has been protected with encryption or obscured with tokenization or data masking
- Audit / log data that allows collection of who, how, where and when data is accessed
- Analysis with a SIEM or Big Data for Security implementation that can use this data to look for unauthorized access attempts, and unusual access patterns from authorized users that may represent a threat
You’ll also want to have a firm understanding of your industry’s compliance mandates before you select a data-centric solution. Examples of compliance mandates our solutions can help you meet include PCI DSS 3.0, HIPAA, NIST 800-53, FISMA, and Data Residency requirements.
In January, I predicted data-centric security would become a core practice of all enterprises. Although you’ll have to wait for my year-in-review to see if that prediction came to fruition, I can share a real-world example of a major financial customer that reset its IT priorities to focus on data-centric security.
This Fortune 500 financial services customer told us that they recognize that their perimeter either has been breached, or will be at some point. They constantly assess the threat landscape that they are seeing and recognize that phishing attacks and other attempts on their perimeter are a serious threat. As a result they are now implementing a policy of adding safeguards around their most critical assets – their data. For them, the key to reducing breach risks (as well as meeting their compliance requirements), is to implement security controls and protections directly around their sensitive data assets.
In case you thought the fun stops once you decide to turn the knob and invest in a data-centric approach, you’re wrong. In fact, there are even more steps you can take. Once your in place tool set can monitor data access, and correlate access patterns, your IT team can catch an act in progress. Once they’ve done so, you have a number of options, including:
- Closing the vulnerability, either automatically or manually
- Tracking the attack back to sources for forwarding to law enforcement, or pulling law enforcement in to do it themselves
- Sidelining the attack with useless information to throw the attackers off the trail of your legitimate sensitive data
- “Poisoning the attack” with information that will injure the attackers credibility and potentially put them out of business
Data-centric security is the business we’re in at Vormetric. You can find out more about how we help companies ensure data security here; the fact sheet also includes an overview of key platform capabilities and a thorough specification table breakdown. At a high level, our data security platform consists of a set of products that share a centrally managed and extensible infrastructure for simple one-stop data-at-rest security.
Our product line – which continues to evolve to combat the latest threats – currently includes transparent file-level encryption, application-layer encryption, integrated key management, and security intelligence solutions. You can choose to deploy these separately or in tandem to address security policies and compliance mandates across databases, files and big data nodes—located across physical, virtual, cloud and hybrid infrastructures.
Of course, I recognize your first step towards making a change is recognizing your company has a need for a “new balance” in IT security priorities. Hopefully, the information outlined in this blog will help you on your journey – and that you won’t have to learn the hard way.
