 The slogan “Internet of Things (IoT) X Big Data = Unprecedented Value!” caught my attention as I was listening to a presentation from Intel Corporation. The scale of the IoT disruption was described in terms of things, data and value:
The slogan “Internet of Things (IoT) X Big Data = Unprecedented Value!” caught my attention as I was listening to a presentation from Intel Corporation. The scale of the IoT disruption was described in terms of things, data and value:
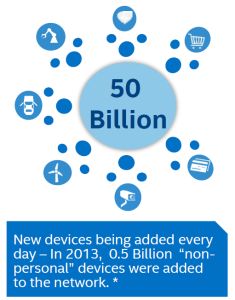
- 50 billion devices are expected to connect to the Internet by 2016. As recently as 2013 this was 0.5 Billion
- These devices will generate 35 Zetabytes of data!
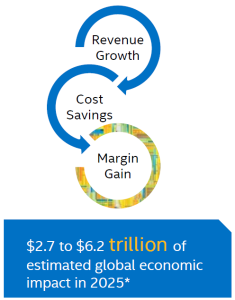
- And can create an estimated value of $2 to $6 trillion in global economic impact.
Now that is huge by any measure!
<Click to Tweet>: IoT Drives Stronger Security for Big Data Environments from @Vormetric #DefenderOfData Ashvin Kamaraju http://bit.ly/1w3qblC
The Internet of Things or IoT is the next big trend promising to connect literally every device on the planet to the internet. IoT will fuel a data explosion that will provide the data needed to improve services, offerings and life in general by analysis and use of the information generated. Much of this data will be sensitive, personal and protected information – driving a critical requirement to safeguard this information wherever it resides - on devices, in transit, in storage and when analyzed.
 Intel Corporation, a technology partner of ours, and a pioneer in IoT, recently announced the Intel® IoT Platform, an end-to-end reference model designed to unify and simplify connectivity and security for the Internet of Things (IoT). Intel also made other announcements that promise to move IoT from infancy to mass deployment. Fortunately security is viewed as a foundational requirement for both dedicated security products using this technology, and hardware and software products based on it.
Intel Corporation, a technology partner of ours, and a pioneer in IoT, recently announced the Intel® IoT Platform, an end-to-end reference model designed to unify and simplify connectivity and security for the Internet of Things (IoT). Intel also made other announcements that promise to move IoT from infancy to mass deployment. Fortunately security is viewed as a foundational requirement for both dedicated security products using this technology, and hardware and software products based on it.
Enhanced Privacy ID, the foundation for IoT security, is a remote anonymous attestation scheme that a service provider will have to use to authenticate a device. The mechanics are complex, but the technology ensures both secure communications and secure identification of devices. Simply put, the issuer or manufacturer of the device issues a unique public/private key pair to the device. The public key is also shared with the service provider who collects data from the device and/or controls it remotely. The device authenticates itself to the service provider by presenting a digitally signed certificate. The device signs the certificate using its private key. The service provider uses the public key to authenticate the device. The devices are also required to use secure technologies for safeguarding their key pairs in more sensitive applications (Intel’s Trusted Platform Module or Trusted Execution Environment). Without such safeguards, hackers could identify themselves as trusted IoT devices with potentially disastrous consequences. Imagine, the havoc that could be caused by breaching a smart power grid!
 As data flows from the edge to the cloud and to Big Data systems repositories hosted by the service provider, a number of data security and privacy issues must be addressed. With almost all of the embedded devices encrypting the data they generate and gateways encrypting data that is ingested from less secure devices and sensors, centralized key management becomes very important. Ideally, a cloud service provider receiving the IoT data will offer key management as a service. This service will allow IoT devices to encrypt the data they generate using keys created, secured and stored in a central location. A key management service can also provision the keys to Big Data servers that have to process the very same data and do the analytics. These Big Data repositories become a very big mixing bowl: Data from IoT devices, data from systems of engagement such as twitter feeds, click streams, Facebook likes etc. and data from systems of record (transactional systems) all come together. Just as important as managing data at this scale is securing the data at this scale. Data security is not only important to prevent data breaches but also to comply with a litany of regulatory requirements.
As data flows from the edge to the cloud and to Big Data systems repositories hosted by the service provider, a number of data security and privacy issues must be addressed. With almost all of the embedded devices encrypting the data they generate and gateways encrypting data that is ingested from less secure devices and sensors, centralized key management becomes very important. Ideally, a cloud service provider receiving the IoT data will offer key management as a service. This service will allow IoT devices to encrypt the data they generate using keys created, secured and stored in a central location. A key management service can also provision the keys to Big Data servers that have to process the very same data and do the analytics. These Big Data repositories become a very big mixing bowl: Data from IoT devices, data from systems of engagement such as twitter feeds, click streams, Facebook likes etc. and data from systems of record (transactional systems) all come together. Just as important as managing data at this scale is securing the data at this scale. Data security is not only important to prevent data breaches but also to comply with a litany of regulatory requirements.
As data flows from multiple sources, avoiding encryption silos and providing a strong, secure key management service will not only help secure the data but also drive ROI for implementations and help make it possible to realize the impact of these two complementary technologies.

 Ashvin Kamaraju | Vice President of Engineering, Strategy & Innovation
Ashvin Kamaraju | Vice President of Engineering, Strategy & Innovation