 Code Blue For Your Healthcare Data
Code Blue For Your Healthcare Data
Few look forward to a doctor’s visit. Unfortunately, this is more the case than ever before, and it is not because of what you might think. Today, patients worry about the information they may have to divulge at the doctor’s office and where it might end up. They say that the best way to stay healthy is to not go to the doctor at all and alarmingly it may also be the best way to keep your confidential information safe.
ClickToTweet: Code Blue for your Healthcare Data @mjrothschild http://bit.ly/1FecNFA
With the digitization of health records (ePCR), identity, credit and health information are all available at the practitioner’s fingertips which makes for the easy transfer and treatment of the patient. Regardless of the treatment plan that the patient will follow, all of this information seamlessly follows the patient with the click of a button. At a moment’s notice, the hospital can receive critical patient information from EMTs in the field before the patient ever enters the facility. This information will follow the patient through his/her stay in the ER, OR, and post-secondary care facilities. Allied health professionals including nurses, dieticians, clinicians, insurance agencies billing and more will all have access to this information. And while the convenience and continuity of care is facilitated by this seamless transfer of information, recent breaches in the healthcare industry gives one pause to wonder if the healthcare facility is appropriately safeguarding patient data in addition to their health.
Risk Reduction
Healthcare facilities are faced with a veritable alphabet soup of federal, state and local compliance regulations. Rules and amendments continue to be phased into mandates, which are updated regularly. Organizations must keep up or face stiff penalties. Equally important is security within the organization. With more people accessing the network from more locations, segmentation of the network and user-based access controls are only the tip of the iceberg. Many endpoint devices such as MRIs and CAT/PET scans cannot be taken offline or even updated with patches, because they are critical devices or because patch updates may invalidate the manufacturer's warranty. Despite the challenges, security and compliance are essential to ensure the protection of patient health and identity information, as well as the organization's assets and operations.
The vast majority of healthcare organizations have done an admirable job in adhering to compliance regulations. This was no small undertaking as many organizations needed to make sweeping changes in policy and infrastructure investment. Nevertheless the question that must be asked is even with all of the legislation and religious adherence to these mandates, why do colossal security breaches happen on a regular basis?
Protecting the Target
The way we consume data is fundamentally different than a decade ago. Back then, we lived in cyber communities which we secured with a big wall around it known as perimeter security. We deployed firewalls, IDS, VPN and much more to ensure that the cyber-criminal was relegated to the other side of the wall. Today however, with virtualization, distributed communities, users leveraging third party and unmanaged devices combined with data being ubiquitous, it is impossible to protect the perimeter because the perimeter no longer exists. While getting to this reality has been painful for many organizations that have suffered a security breach, it is equally important to realize that achieving regulatory compliance is a bare minimum that often does not protect organizations from attacks that are extremely dynamic. The only way to adequately secure information is to protect the attack target namely the data rather than the delivery mechanism, namely the network.
An Eye to the Future - Encrypt Everywhere
To remain competitive, today's health organizations must secure that which is most sought after by the cyber-criminal, be they and insider or traditional outsider. Recognize that regardless of the steps taken to secure your network, breaches happen. Often times, it is not a question of “if” it will happen, but rather “when”. Encrypting your most sensitive data whether in the cloud or in storage will render the data useless to the hacker that has defeated your security countermeasures. Ensuring that insiders only have access to the data they require to do their job is essential and masking data such as credit card information, social security numbers and other sensitive data can greatly reduce the temptation and incidence of unauthorized releases of data.
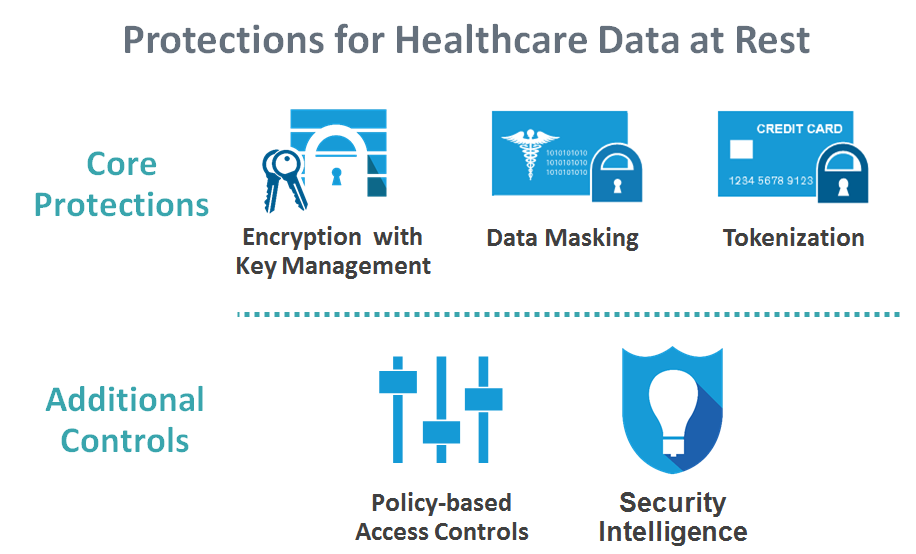 The best way of strategically positioning your organization for success is to deploy a layered security approach that protects the infrastructure, but perhaps more importantly protects the data. Use compliance as the bare minimum, but build from there to protect what really matters where it matters. Going to the doctor is never pleasant, but deploying the right security will eliminate the important and sometimes most painful question, “Doctor, is my data safe?”
The best way of strategically positioning your organization for success is to deploy a layered security approach that protects the infrastructure, but perhaps more importantly protects the data. Use compliance as the bare minimum, but build from there to protect what really matters where it matters. Going to the doctor is never pleasant, but deploying the right security will eliminate the important and sometimes most painful question, “Doctor, is my data safe?”
