Recently, we released the results from the cloud edition of our 2015 Insider Threat Report. My colleagues Andy Kicklighter and CJ Radford delved into the results in their blog posts from March 24 and March 26, and I’ve gone into a bit more detail about the findings below. But, the purpose of this blog is to do two things: a) discuss what we hear matters when it comes to successful and safe SaaS consumption and delivery and b) with this feedback in mind, outline the tools and capabilities necessary to make this happen.
ClickToTweet: It’s all about the SaaS – SaaS Bill of Rights @kessalan #DefenderOfData http://bit.ly/1xBP8fI
Stormy Clouds Ahead?
It wouldn’t be an exaggeration to say that cloud computing has changed the way organizations approach IT; it’s enabled them to become more agile, introduce new business models, provide more services and reduce IT costs. Perhaps unsurprisingly, the Cloud and Big Data Edition of our 2015 Insider Threat Report found that 54 percent of respondents globally reported keeping sensitive information within the cloud.
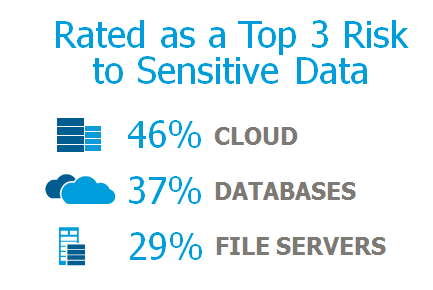
But, the movement towards wide-scale cloud adoption doesn’t come without worries. Our survey also found that most IT decision makers have concerns about relinquishing security and control when they deploy cloud technology – which is an issue when 46 percent report market pressures are forcing them to use cloud services. In the U.S. cloud environments (46 percent) outpace databases (37 percent) and file servers (29 percent) as the location perceived as being the greatest risk by enterprise organizations.
Your (Cloud) Type–and How it Affects What You Want
As an enterprise customer and consumer of SaaS, we get it. From our conversations with enterprise customers, partners and through our own experiences, this is what we hear matters:
- IaaS: When it comes to the consumption of IaaS, there are certain security capabilities you want to ensure maximum data security and control over your data, including:
- Data-at-rest protection (data encryption with the ability to perform privilege user access control is a key requirement in this environment to remove the custodial risk of IaaS infrastructure personnel accessing sensitive data)
- Along those lines, the ability to manage who and which applications in your IaaS environment can access your data
- The ability to control and manage your own keys, even as your data is stored in an IaaS environment
- The ability to receive audit log information to monitor the administration of your data and data policy by your IaaS provider
- SaaS: When it comes to SaaS, we’ve found you’re generally looking for:
- The ability to encrypt data before it leaves your premises
- Compliance without interfering with functionality
- Visibility and audit logs for tracking data access and movement between users and the cloud service
- Key management that works across many different use cases across your enterprise and can deliver consistent policy implementation between systems, reducing training and maintenance costs. With this, comes:
- The ability to control what data can be viewed and reported on by your SaaS provider including having a kill switch to your data when you turn down a service
- The ability to control who within the SaaS environment can see your data and have the flexibility to control access to the keys necessary to view sensitive data in the SaaS cloud
- Ability to separate the keys from the data repository. This typically means the encryption keys stay on the customer premises or at least are only managed by the customer.
As you can see, there’s a recurring them here: transparency and visibility. The transparency point is important, most notably in an environment where you may host a wide range of applications, data types and operating system/computing environments. You would like to have a data security solution that is broadly applicable across structured and unstructured data and across a broad range of operating environments and supports public, private and hybrid clouds.
The Cloud Is All Around Us
Many enterprises operating in a B2B context are not only consuming Infrastructure as a Service (IaaS) and Software as a Service (SaaS) services, but are delivering solutions to their business customers via SaaS. (If you need a refresh of how these cloud models are defined, I recommend you check out our excellent Data Security in the Cloud White Paper).
What do I mean by this? Well, let’s say you’re Company X. As Company X, you deliver enterprise products that allow other enterprises to analyze their data. One of those enterprise products comes in the form of a cloud-based service. Concurrently, you also consume SaaS for your own internal purposes. You might, say, use Salesforce. Or AWS. Or BOX. So, you have a lot of (cloud) balls in play. Chances are, your security stress level is high. This has to do with the fact that you simply don’t have the visibility and control you do when using your own resources–and you also want to ensure your customers feels protected.
That being said, the economic and operational benefits of cloud technology are compelling enough to drive your business partners within the organization to consume cloud services. But, you still need a guarantee of security as a consumer and deliverer of cloud services – and this means you need a platform that contains features/capabilities addressing the concerns outlined above. Below, I’ve walked through some methods for getting to a secure place.
Techniques for Protecting Data in the Cloud
Data Protection/Encryption
Let’s start with data protection. You own your own data and you safeguard your customer’s data. That’s a lot of data to worry about. So – and this is somewhat dependent on the use case – you will need to protect that data at the file level or application level. A file level solution using transparent encryption is quick and easy to deploy and protects databases (structured data), files (unstructured data) and big data repositories. Application level encryption encrypts the sensitive data fields form within the application itself. This has the added advantage of assuring not only encryption of the data at rest, but also the data in motion starting at the application server. This method gives very granular control of what fields to encrypt.
Another granular method of encryption is through the use of tokenization. Tokenization replaces sensitive information in databases with a token, which is a meaningless placeholder that even if stolen, can’t reveal the data it’s protecting because the actual data has been replaced and a token is irreversible. By using tokens, threats are mitigated from both inside your organization and from outside attackers because the object of their hacking doesn’t contain the information they desire. The sensitive data itself is kept in a token vault, which is encrypted and in a very secure and controlled location, thereby drastically cutting down the amount of people with access to the sensitive information.
Another consideration when displaying data to an end user is to implement dynamic data masking. Dynamic data masking is pretty much exactly what it sounds like: it’s the process of hiding original data with a replacement characters. Common reasons for employing dynamic data masking are to protect classified data, such as Social Security numbers, credit card numbers and financial information that only needs to be partially displayed to certain users.
For example, when you view your credit card statement online, you often see only the last four digits of the credit card number. The first digits are obfuscated with a character pattern such as XXXX-XXXX-XXXX. This is dynamic data masking in action. As the end-user, you only need to see your last four digits to know which credit card is represented on the statement.
The target markets for tokenization and dynamic data masking are generally those that must follow strict compliance regulations. Examples include retail, which must abide by the Payment Card Industry Data Security Standard (PCI DSS) and healthcare, which is beholden to HIPAA. Big data lakes also often present a large need for data masking and obfuscation, because much of the data contained in those lakes is unstructured. For more information on the fascinating topic of data lakes, I invite you to check out a blog by our VP of product development and partner management, Ashvin Kamaraju and a blog by our CSO, Sol Cates.
We recognize not everyone is on the encryption train. So, if you don’t want to (or can’t) encrypt data before it leaves the confines of your network, we recommend working with SaaS providers who provide strong security.
Key Management
Earlier, I delved into key management because it’s an important component of encryption. If you’ve chosen to encrypt data, it means you (or someone else) has a handle on the decryption key.
When it comes to key management, there’s basically two models to consider for encrypted data. Either you own and manage the key, or you allow your service provider to own and manage your key on your behalf. Each model has its own risks and that will depend on the level of risk and cost you’re prepared to take on. As a best practice, as the owner of the data, we recommend you own and manage the key.
Regarding the transparency point I brought up earlier: Vormetric Cloud Encryption, for example, includes encryption key management within the solution and is completely transparent to applications and users. This allows for existing processes and usage to continue with no changes. Thus, you can protect any data file within cloud environments simply, easily and efficiently.
Key management basically allows for access control, which means limiting access to encrypted data to only those whose work requires it.
An intelligent implementation of access control will allow system and application maintenance and operations without exposing data to the privileged users who carry out these tasks. It also meets myriad compliance requirements and stops the threat of legal or physical compromise of the cloud environment. Even if someone walks away with the drive, or more realistically finds their way to your data by finding a security flaw in the provider’s environment, they won’t see a thing of value. And if you control your own keys, legal challenges to see your data in the cloud provider’s jurisdiction aren’t possible without your knowledge and cooperation.
Conclusion
In a nutshell, the end goal for you, the enterprise, is to trust your cloud service providers, trust your employees that are using the cloud to make their workflow more efficient and streamlined and trust that any cloud-based solutions you are delivering to your business customers will not open them up to security risks.
Although I’m just a tad biased, I like to think our existing data security products (and some soon-to-be-announced new updates!) meet the majority of needs outlined above. I’m so confident about this, I invite you to come take a look for yourself while you’re at RSA (you will be at RSA, right?)
You can find us at booth #3015 (North Hall) and booth #515 (South Hall). Bring your shopping cart by, and our team will show you the goods.