I’ve been working in the data-at-rest encryption field for almost three years now. In this short amount of time I’ve seen a real change in the market’s perception and acceptance of encryption. In fact, less than two years ago I was running a marketing and messaging meeting that included some of Vormetric’s sales leaders and they all asked that we play down the word “encryption” in our high-level messaging. They said their prospects’ eyes just glazed over when they heard the word. What a difference 18 months—and some of the largest data breaches in history—can make.
I’ve been working in the data-at-rest encryption field for almost three years now. In this short amount of time I’ve seen a real change in the market’s perception and acceptance of encryption. In fact, less than two years ago I was running a marketing and messaging meeting that included some of Vormetric’s sales leaders and they all asked that we play down the word “encryption” in our high-level messaging. They said their prospects’ eyes just glazed over when they heard the word. What a difference 18 months—and some of the largest data breaches in history—can make.
We recently shipped the Vormetric Cloud Encryption Gateway. The product was originally slated to go out as the “Vormetric Cloud Gateway”, but some of the very same sales leaders who wanted us to avoid the word “encryption” before now wanted us to add it in. These sales managers now say customers’ eyes light up when they hear “encryption”. Leading enterprise CISOs and architects clearly understand the value that encryption brings in a world where you can no longer build a security perimeter and keep your data inside it.
ClickToTweet: Storage teams shouldn't choose your IT Security encryption solutions http://bit.ly/1HtqBL4
Vormetric isn’t the only company enjoying the growth that comes with the accelerating adoption of encryption. Sales of full-disk encryption (FDE) solutions for laptops are also growing. Analyst firm MarketsandMarkets expects the laptop disk encryption segment to grow substantially in the coming years. In fact, disk encryption, along with file/folder encryption and database encryption, was listed in the top three applications in terms of anticipated adoption growth. The laptop disk encryption category is expected to grow by a compound annual growth rate (CAGR) of 13.7% between 2014 and 2019, when it is expected to exceed $1.6 billion. File/Folder encryption and database encryption have a predicted CAGR of 22% and 26.7% respectively (Source: MarketsandMarkets, “Encryption Software Market: Global Forecast and Analysis 2014-2019”).
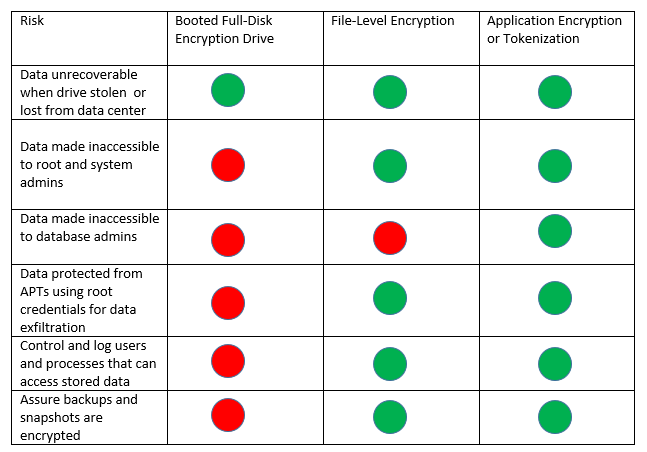
It is no wonder that enterprise storage vendors are looking to grab a piece of this expanding market. Most major network-attached storage (NAS) and storage-area network (SAN) vendors now offer some flavor of FDE. However, these FDE drives come at a very large premium. Typically, FDE-enabled platforms cost 30-40% more than those without built-in encryption. Further, they lock you in because you can’t mix FDE and Non-FDE systems, even from the same vendor, when extending your storage solution. The result of this FDE decision is that you can’t bring in a second storage vendor and have them compete for your business. For the storage vendor, who’s is typically selling to the storage team rather than security team, FDE is a great upsell and lock-in. But is it a good deal for the customer?
If you’re in charge of making these investments for your business, you have to think about your most critical risks, and you also need to look at which investments will give you the best value. How would a security professional compare the protections offered by FDE to those delivered by other solutions? I expect that they would start with a table like the one below:
It is important that security teams are the ones making the security technology decisions, and that they do so with a clear focus: keeping the company’s brand and customer data safe. Security decisions are simply too important today. Just because other groups, such as storage teams, may have budget, that doesn’t mean they have the security expertise required to procure optimal encryption technologies. If these investments provide a false sense of security, the risks could be significant.
Don’t let your storage team be the Justin Bieber of your company—they may have the budget, but it doesn’t mean they know how to use it responsibly. It is up to the security teams to be the responsible adults and to protect corporate data. They need to be the ones guiding the entire company to adhering with best security practices and making mature, well thought out decisions. After all, a lapse in judgement in the high-stakes world of IT security can be a lot more harmful than some thrown eggs and an abandoned monkey.

 Charles Goldberg | VP, product marketing
Charles Goldberg | VP, product marketing