 Is a data breach inevitable if hackers or internal bad actors are targeting your organization? Looking at the polling results from the our 2016 Vormetric Data Threat Report gives a distinctly mixed result ... With a high bias towards "Yes" for many organizations.
Is a data breach inevitable if hackers or internal bad actors are targeting your organization? Looking at the polling results from the our 2016 Vormetric Data Threat Report gives a distinctly mixed result ... With a high bias towards "Yes" for many organizations.
Let's talk about the negatives first ...
Data breach numbers highlight the problem
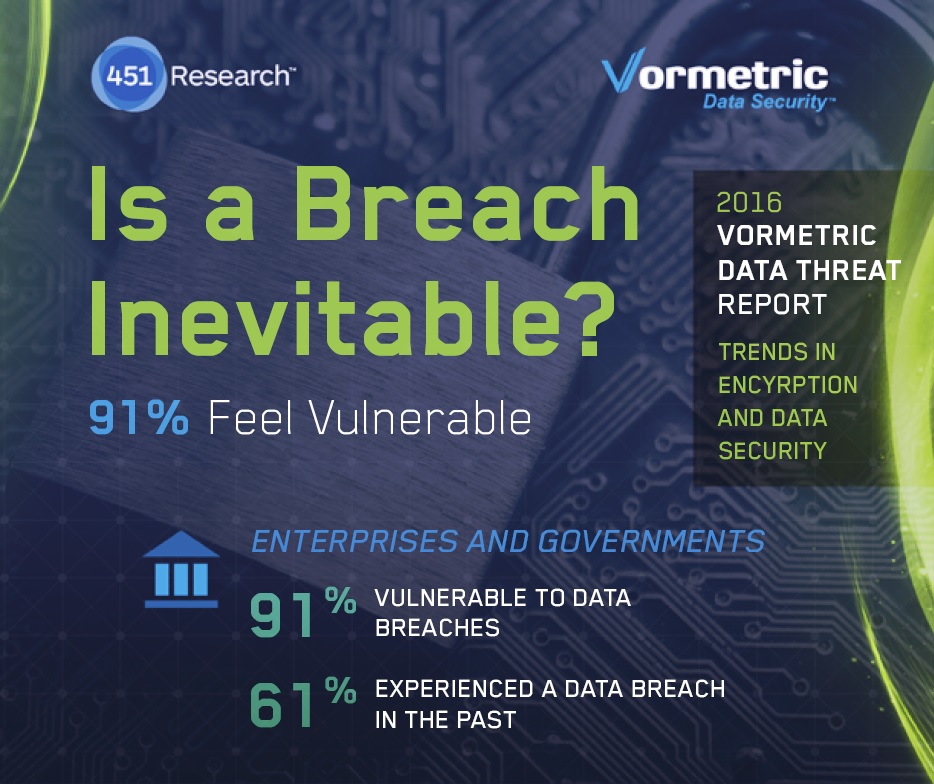
For a starting point, 91% of respondents felt somewhat or more vulnerable to a data breach and 30% were "Very" or "Extremely" vulnerable.
Next take a look at the number of data breach encounters reported - only 39% said they'd never had a data breach (61% did have one), and 22% had a data breach in the last year.
Let's put this another way - 1 in 5 large enterprises or government organizations get's breached every year. Almost 2 out of 3 have already been breached.
We don't have a direct comparison number for this from our last year's report, but we do have a comparison number for how many organizations encountered a data breach or failed a compliance audit in the last 12 months - The level held steady at 39% both years.
ClickToTweet: Is A #DataBreach Inevitable? @akicklighter http://bit.ly/20JleR4 pic.twitter.com/fawL7XIyBw
How are organizations protecting data?
Let's add the next set of data points - How organizations are protecting their critical information today.Well, many of them rely on compliance to protection them.
- 64% of respondents believe that meeting compliance requirements is very or extremely effective at protecting against data breaches.
What about Target, Home Depot and a host of others that were PCI compliant at the time they were breached? Here's also what Garrett Becker, Sr. Analyst Enterprise Security with 451 Research had to say about that:
"Compliance does not ensure security”
"..being compliant does not mean you won’t be breached"
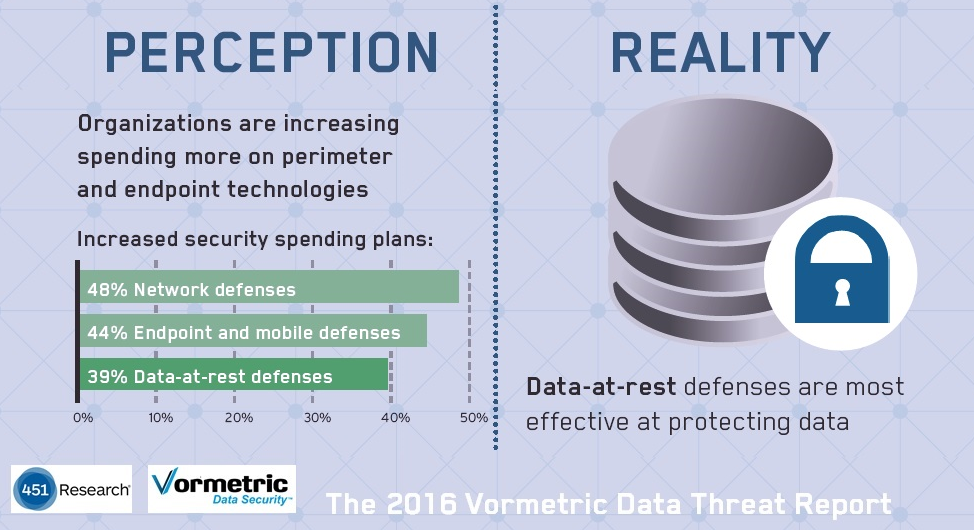
Another item to consider is how they are investing in security tools to protect their data. What we found is that people are investing most heavily in the tools that worked in the past - network, end point and mobile defenses, rather than what's working now to stop breaches after these perimeter defenses have failed (encryption, access controls, multi-factor authentication and security analytics with SIEM or other technologies).
- 48% increasing spending on Network defenses
- 44% increasing spending on mobile and end point defenses
- While only 39% are increasing spending on data at rest defenses
Adding up the bad news
Let's add this negative news up, then we'll look at the positive side:
- 91% vulnerable to data breaches, 30% Very or Extremely vulnerable
- 61% have had a data breach already - 22% in the last year
- 39% had a data breach or a compliance failure in the last year
- 64% believe compliance is very or extremely effective at stopping breaches
- Spending increases are focused on perimeter defenses that are failing to stop breaches - 48%/44% on Network and end point defenses versus 39% on data at rest defenses
Hopeful signs
But there are some hopeful signs - A fair number of organizations are recognizing the problem and some are increasing spending in areas that make sense to protect their data.
- 58% are increasing spending to protect data
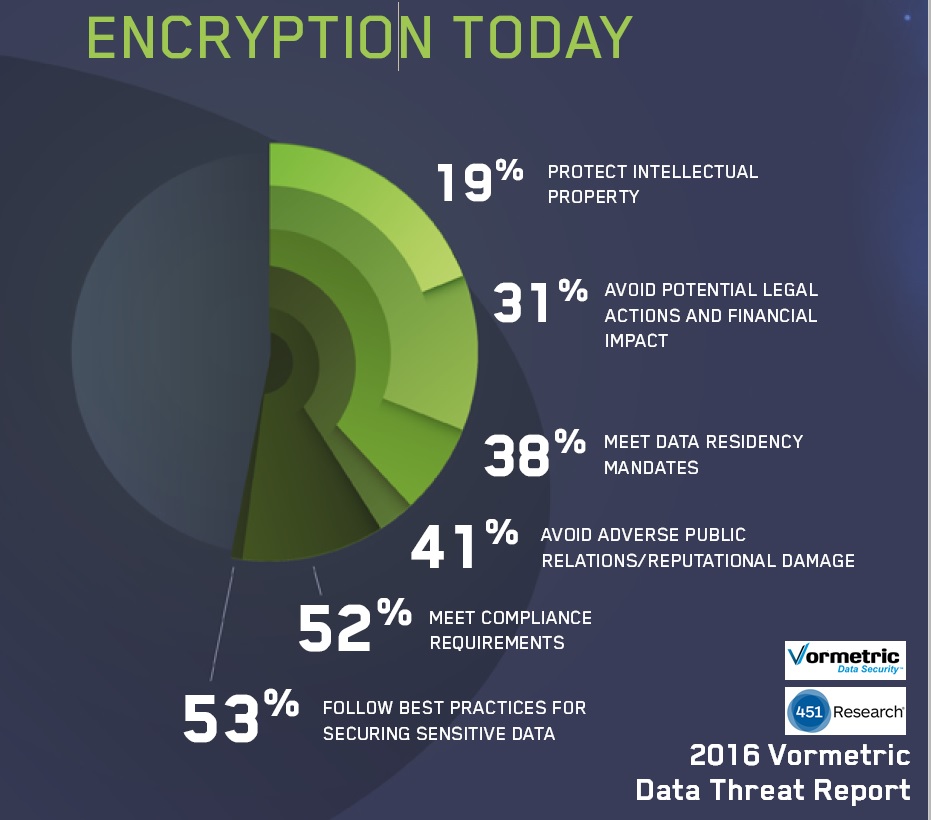
- Many are implementing tools that are effective in offsetting the problem
40% - Application layer encryption
39% - Multi-factor authentication
38% - SIEM systems
Encryption and access controls for data-at-rest and data-in-motion are well recognized tools for stopping data breaches once peripheral or service provider defenses are breached and is use today at many organizations to help offset the problem.
So - Is a breach inevitable?
Sadly, for organizations that are prioritizing compliance over breach protection, and who are not adding a layer of defenses around data assets both at-rest or in-motion, within the data centers or in their cloud and other outsourced resource environments, the answer will be "Yes". While those who are adjusting their IT Security stances to these new realities will be able to minimize or stop the breaches entirely.
Note: To build the report we polled 1100 individuals in IT Security roles for enterprise and government organizations - 500 of those in the U.S., and then 100 or so each from Mexico, Brazil, Japan, the U.K. and Germany.

 Andy Kicklighter | Director of Product Marketing
Andy Kicklighter | Director of Product Marketing