 We've all been there - it's a place called denial. It's what happens when you know there's something that you should be doing, but you put it off, refuse to recognize it, or just pretend it will go away.
We've all been there - it's a place called denial. It's what happens when you know there's something that you should be doing, but you put it off, refuse to recognize it, or just pretend it will go away.
Well that is what we're seeing when looking at the investments that many enterprises are making in data security in the results from our 2016 Vormetric Data Security Report.
ClicktoTweet: Visiting denial: Enterprise Data Security Spending Plans @akicklighter #2016DataThreat http://bit.ly/1TjBTbs
The Problem
The numbers on the problem side are a bit daunting:
- 61% experienced a data breach - 22% in the last year
- 32% failed a compliance audit - 17% in the last year
(this means that there were more compliance failures in the last year, than in all previous years combined)
If you are in IT Security, by now you've heard the analyst mantra "It's no longer if you will be breached, it's when". It's the result of the peripheral, end point and network defenses we've all relied on for years now reaching a measurable failure rate in the face of new external attacks or even insiders bent on personal gain. If you want a realistic view of how vulnerable your organization is - just run a penetration test using a phishing email. The results won't be heartening. A year or two ago the Verizon Data Breach Report highlighted that there is a 90% chance of a click after 15 spear phish attempts. You might even find that to be "optimistic".
Here's what Analyst Garrett Bekker from 451 had to say (In the 2016 Vormetric Data Threat Report):
"It’s no longer enough just to secure networks and endpoints”
".... perimeter defenses offer little help defending against multi-stage attacks”
"... data-at-rest approaches have proven to be effective at protecting the data itself"
 Not Getting the Mix Right
Not Getting the Mix Right
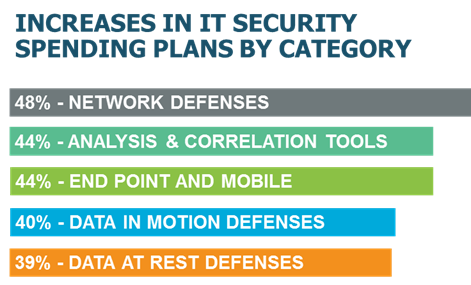
But many are getting their spending priorities wrong and putting more spending into the tools that won't stop the problem. Yes - we definitely need network, end point and mobile defenses (a short categorization for a very long list of security controls), but until we get this problem under better control, a bigger emphasis on the defenses that are effective even when these traditional defenses have been bypassed is what we need. What are they?
- Data-at-rest and in-motion defenses
- Analysis and correlation tools
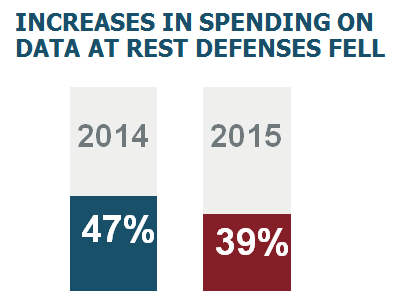
We also found that people weren't increasing data at rest spending as much as in previous years:
- 47% were increasing data-at-rest spending in 2014
- While only 39% were increasing spending in this category in 2015
What do the ones getting it right do?
First - Recognize that there is a problem and take action.
- With 58% increasing IT Security spending to protect sensitive data that's a really positive step. But as we've seen above, it's not always effectively applied at correcting the problem.
- 36% now have policies that make preventing data breaches a top 3 IT security spending priority. Again, a great step in the right direction, but not always well applied. Many people are trying to fix a new problem with their old tools
Next implement tools that will make the biggest difference -
- Tools that recognize threat patterns (Like SIEM or Big Data for Security instances)
- That apply protections for access controls directly on the data (like encryption, access controls, tokenization and data masking)
- That reduce attack surfaces by making it harder to connect inappropriately (like multi-factor authentication)
- And that take into account that unless IT makes available the latest tools in a controlled fashion, shadow IT and additional security risks to data will happen - like a cloud security gateway system for cloud storage
And for those increasing spending on data security a fair amount of that is happening:
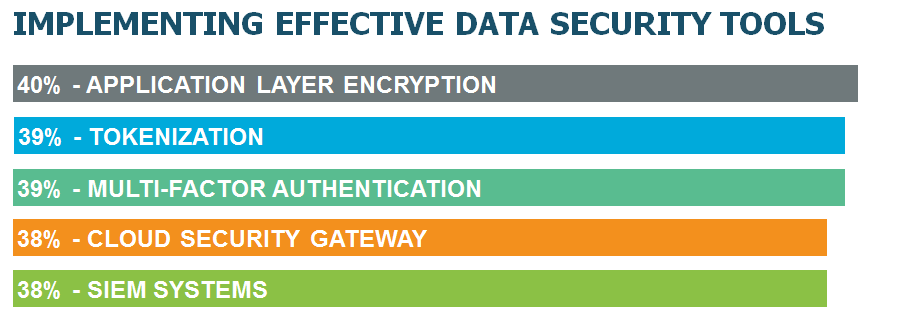
- 40% increasing spending on Application layer encryption
- 39% adding spending on Tokenization
- 39% implementing more Multi-factor authentication
- 38% spending more on Cloud security gateway systems
- 38% investing the SIEM systems

 Andy Kicklighter | Director of Product Marketing
Andy Kicklighter | Director of Product Marketing