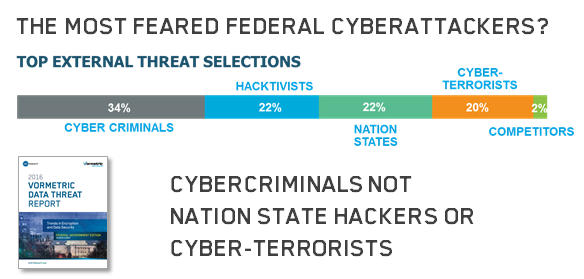
 What were the most surprising things that we learned from the U.S. Federal Edition of the Vormetric Data Threat Report? At the top of my list was the rating for the top threat selection by 100 U.S. IT security professionals working for Federal Agencies of their top external threats.
What were the most surprising things that we learned from the U.S. Federal Edition of the Vormetric Data Threat Report? At the top of my list was the rating for the top threat selection by 100 U.S. IT security professionals working for Federal Agencies of their top external threats.
After numerous incidents over the last several years fixed on Chinese government sponsored hackers (can you say APT?), Iranian hackers, North Korean cyber attacks, ISIS cyberterrorists, possible Russian state-sponsored hacking and many incidents where the cyber terrorists were not identified, the top external threats identified were from cyber criminals out for personal gain like those recently revealed to have hacked the IRS at 34% with Nation State hackers and Cyber-terrorists at much lover 22% and 20% selection rates.
Click To Tweet: Most Feared Federal Agency Hackers? Cyber Criminals not Cyber Terrorists http://bit.ly/1oieFXl pic.twitter.com/xJNr0xsz50
Which would you find more important? A cyberattack where the personal details of all the people who've applied for a security clearance in the last 10 or 15 years were stolen reportedly by nation state hackers from China (and even the fingerprints for a fair percentage of them), or a the financial data from the more recent IRS breach?
Keep in mind that the same hackers who stole the security clearance data were also reported to have breached United and other airlines flight records. So for some people, their personal contacts, addresses, family backgrounds, and other details could be combined with flight data.
Match these pieces of information up, and there are real issues for the safety of people in these positions AND their families. Is combating illegally filed tax returns really more important?
To be fair, the reading could well represent the differing priorities of federal agencies. DOD and Homeland Security are bound to have different priority lists than DOE, Commerce or Health and Human Services. Some agencies may feel they have few critical secrets to protect from foreign attackers. But I'd like to argue that there are actually few federal agencies that DO NOT have critical secrets that need protecting.
What else? Budgeting and Resource problems
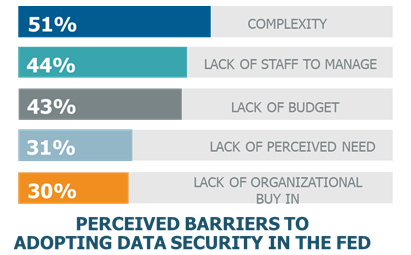 Another surprise - The size of the budget and resource problem. Lack of budget a much bigger problem than other verticals that we measured
Another surprise - The size of the budget and resource problem. Lack of budget a much bigger problem than other verticals that we measured
Even with recent expansions in cybersecurity funding, 43% in Government versus only 23% in Financial Services made budget a top barrier to deploying data security. The biggest concerns for Government were complexity at 51% and lack of staff at 44% - and these all lead in to the lack of budget problem.
And Where are Federal Agencies Planning to Increase IT Security Spending?
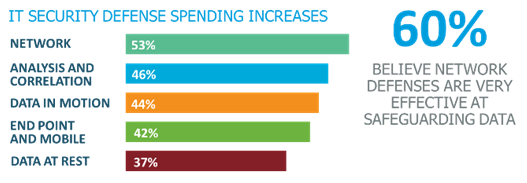 Well, highest increases in spending are not on the defenses that are best at protecting data once defenders have broken into the secure perimeter - Data at rest defenses. Network defenses at 53% are getting the biggest increases, and correspondingly, 60% believe that they are very or extremely effective at preventing data breaches.
Well, highest increases in spending are not on the defenses that are best at protecting data once defenders have broken into the secure perimeter - Data at rest defenses. Network defenses at 53% are getting the biggest increases, and correspondingly, 60% believe that they are very or extremely effective at preventing data breaches.
But the last defense for the information that cyber attacks are usually designed to go after are data at rest defenses, and these are getting the least funding increases (37%). There is good recognition that we need secure sessions and transactions, best done with data in motion defenses, but what attackers are most interested in getting to is data. Time after time, a way is found by determined attackers to breach traditional perimeters, find their way through IDS/IPS and DLP defenses, heavily segmented networks and other network defenses to get to what they seek.
It isn't that traditional end point and network defenses are not important, and don't need funding. They are a required element in a layer defense in depth strategy ... but a shift in priorities to include data at rest security should be on the agency "to-do" list.

 Andy Kicklighter | Director of Product Marketing
Andy Kicklighter | Director of Product Marketing