 By leveraging a strong encryption standard like AES, organizations can realize a number of advantages, but they can also confront some downsides. Now, there’s a newly sanctioned approach that offers the potential to avoid some significant tradeoffs when employing AES encryption.
By leveraging a strong encryption standard like AES, organizations can realize a number of advantages, but they can also confront some downsides. Now, there’s a newly sanctioned approach that offers the potential to avoid some significant tradeoffs when employing AES encryption.
Advanced Encryption Standard (AES) is a strong algorithm that’s been widely adopted for some time. One of the positives of AES encryption is that it hides the original format (e.g. size and character set) of the clear-text data, making it very difficult to determine what type of data was encrypted. Here is a very simplistic example: The AES encryption of both a 9-digit social security number and a 16-digit credit card number would be ciphertext of at least 16 bytes in binary data. Just by looking at this ciphertext, you would have no idea what the original data type was, because the schema is destroyed.
Click to Tweet: Format Preserving Encryption - Now Approved by NIST @chvrles https://bit.ly/31ZVaKI pic.twitter.com/moD9PrXYhJ
However, this same attribute becomes a problem when encrypting clear-text data that resides in a fixed-length database field. Using the same example, if a field is designed to only contain a 9-digit social security number, the resulting 16-byte ciphertext would break the database schema.
Format preserving encryption (FPE) solves this problem by leveraging AES algorithms in such a way that the resulting ciphertext retains the original schema. A social security number can become 9 digits of ciphertext and a 16-digit credit card number can result in 16 digits of ciphertext. The database schema is maintained. Even a driver’s license number, which is a mix of letters and numbers, can appear as ciphertext comprised of letters and numbers. Voila—data remains secure and the database schema stays intact!
The challenge with FPE for most organizations was that the security of this approach hasn’t been broadly sanctioned. For example, the National Institute of Standards and Technology (NIST) hadn’t gone through its rigorous processes of analysis and established a standard for how FPE can be securely implemented. With the publication of NIST’s new FPE standard, which was published at the end of March, security teams can more confidently pursue FPE solutions and understand the specific approaches that have been tested and sanctioned.
Background on the NIST Standard
NIST operates as the governing body for the development of technical standards for federal government agencies in the U.S. However, NIST’s influence extends far beyond federal agencies. Security professionals in virtually any industry, and many government and industry regulators, view NIST as an authority in terms of ensuring that technologies and approaches employed adhere to best practices.
While the FPE standard was just released at the end of March, NIST’s standard development process has been underway for years. In fact, the NIST committee has been engaging with the industry on this topic for nearly a decade, and the first public comment periods in the development of the standard took place back in 2009.
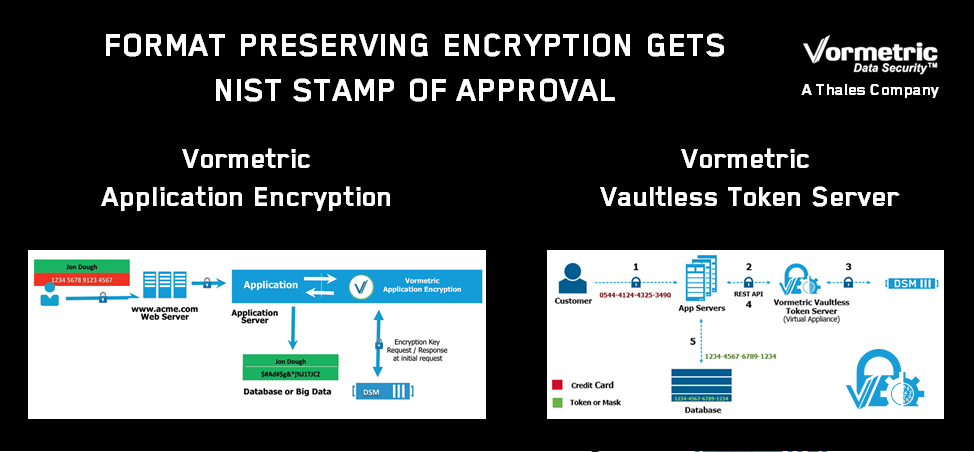
Vormetric FPE Capabilities Adhere to NIST-Approved Standards
We’d been closely watching developments on the NIST FPE standard development front for some time. As we tracked this progress, and began to feel confident about the direction of this process, we decided to invest in adding FPE capabilities to the Vormetric Data Security Platform.
Announced back in November of 2015, the latest version of Vormetric Application Encryption was extended, so now the solution supports both FPE-based AES encryption as well as standard AES. As a result, organizations can now leverage FPE capabilities in the Vormetric solution with the confidence that this approach is now a standard that has been fully vetted by NIST.
NIST has approved two specific forms of FPE, which it refers to as FF1 and FF3. The FF3 standard is the most recent and, for typical use cases, will tend to enable faster performance than FF1. Vormetric Application Encryption offers support for the FF3 standard.
In February, the Vormetric Data Security Platform was expanded again, with the addition of a Vaultless Tokenization option. FPE is the engine behind this solution. Moving forward, you will see many more innovations in the platform as we further leverage FPE technologies to address new data security use cases.
Conclusion
If your security team has been holding off on encryption because database schema changes presented obstacles, but you were concerned about adopting a non-standard approach, now may be the optimal time to explore FPE. That said, it’s important to start with a broader look at encryption alternatives, and determine whether file-level encryption, tokenization, or application-level encryption, and FPE approaches specifically, are truly best for your specific organization, technology environment, threats, and use cases. Whatever technology is best for each use-case you face, the Vormetric Data Security Platform is equipped to help.
For more information, be sure to start by reviewing the page, “Selecting the Right Encryption Approach” or Cracking the Confusion: Encryption and Tokenization for Data Centers, Servers and Applications a white paper and webinar by Securosis. Finally, if you’re interested in reading the full documentation of NIST’s FPE standard, be sure check out this link: NIST Special Publication 800-38G.

 Charles Goldberg | VP, product marketing
Charles Goldberg | VP, product marketing