The roots of encryption go deep into human history. Encryption has been used for centuries to encode messages, usually to keep government secrets, but also to protect business or trade secrets such as the formula to make silk or pottery. Early encryption was fairly simplistic, largely relying on paper and pencil techniques like steganography, transposition and substitution. In the last century, encryption methods have advanced at a rapid clip, first by leveraging automation and the use of machinery and then by employing advanced mathematics and powerful computers.
While encryption today involves powerful computers, it wasn't always so complicated or ubiquitous.
Early Encryption Methods
It is said that in 700 B.C., the Spartan military used scytales to send secret messages during battle. The sender and the recipient each possessed a wooden rod of the same diameter and length. The sender would tightly wind a piece of parchment or leather around the stick and write a message. The unwound document would be sent to the recipient, who would wind it around his stick to decode the message. In its unwound state, the message was gibberish.
Julius Caesar created one of the simplest and most recognized encryption techniques: the Caesar cipher. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on. He used this method in his private correspondence at a time when many of his enemies could not read and other may have assumed the message was written in a foreign language. It is therefore assumed to have been reasonably secure in the first century B.C., but today a single-alphabet substitution cipher is easily broken and offers essentially zero security.
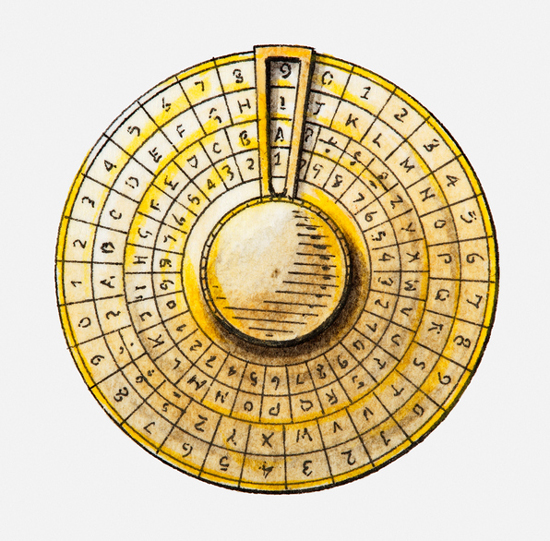
In the 15th century, Italy’s Leon Battista Alberti was the quintessential Renaissance man. Mostly known for being an artist, he also is credited as an author, architect, priest, poet, linguist, philosopher and cryptographer. In 1467, Alberti invented the first polyalphabetic substitution cipher. The Alberti Cipher consisted of two metal discs on the same axle, one inside the other, and involved mixed alphabets and variable rotations. It changed the course of encryption: unlike previous ciphers, the Alberti Cipher was impossible to break without knowledge of the method. This was because the frequency distribution of the letters was masked, and frequency analysis – the only known technique for attacking ciphers at that time – was no help.
During his tenure as George Washington’s Secretary of State, Thomas Jefferson invented the Jefferson disk, or wheel cipher. The system used a set of wheels or disks, and the letters of the alphabet were inscribed on each wheel in random order. Turning them would scramble and unscramble words. Each disk is marked with a unique number, and the hole in the center of the disk allowed them to be stacked on an axle in any order desired. To encrypt the message, both sender and receiver had to arrange the disks in the same predefined order. By using 36 disks, Jefferson’s disk was considered unbreakable at the time.
Encryption and War
Jefferson’s disk was independently reinvented in the late 19th century by Commandant Etienne Bazeries, and named Bazeries cylinder. It was used as a U.S. Army field cipher after World War I. But perhaps the most famous war time encryption machine is Engima. Invented by Arthur Scherbius, Enigma was Germany's main cryptographic technology during World War II. The Enigma machine consisted of a basic keyboard, a display that would reveal the cipher text letter and a scrambling mechanism. Each plain text letter entered via the keyboard was transcribed to its corresponding cipher text letter. Enigma was eventually broken due in large part to the work of Marian Rejewski, a Polish statistician, mathematician and code breaker. Before Germany invaded Poland, Rejewski transferred all his research to the English and the French. The team at Bletchley Park, including Alan Turing, used Rejewski's work to build bombes, electromechanical machines that were designed specifically to break Enigma. This work is credited with being a crucial step to ending World War II.
Encryption in Today’s Computing World
Advances in computing led to even greater advances in encryption. In 1979, the National Bureau of Standards invented Data Encryption Standard (DES) using what was then state-of-the-art 56-bit encryption – even supercomputers of the day could not crack it. In general, the longer the key is, the more difficult it is to crack the code. This holds true because deciphering an encrypted message by brute force would require the attacker to try every possible key. DES was the standard for encryption for more than 20 years, until 1998, when the Electronic Frontier Foundation broke the DES key. It took 56 hours in 1998, and only 22 hours to accomplish the same feat in 1999.
As we can see, as technology advances, so does the quality of encryption. Once the internet began to see increased commercial transaction use, DES was finally replaced by the Advanced Encryption Standard, or AES, which was found through a competition open to the public and approved by NIST. This method is still in use today.
But perhaps one of the most notable advances in the study of cryptography since World War II is the introduction of the asymmetric key ciphers (also known as public key encryption). Whitfield Diffie and Martin Hellman were pioneers in the field of asymmetric cryptographic techniques. These are algorithms that use a pair of mathematically related keys, each of which decrypts the encryption performed using the other. By designating one key of the pair as private, and the other as public (often widely available), no secure channel is needed for key exchange. You can reuse the same key pair indefinitely – as long as the private key stays secret. Most importantly, in an asymmetric key system, the encryption and decryption keys are not identical, which means that, for the first time in history, two people could secure communications without any prior interaction – ideal for internet transactions.
Ronald L. Rivest, Adi Shamir and Leonard M. Adleman were inspired by Diffie and Hellman to create a practical public key system. The result was RSA, which was based on the difficulty of factoring large numbers, and is a common cryptograhic technique on the internet today.
Now that we have widespread use of encryption, what challenges do we face? To break encryption, the most basic method of attack is brute force. This is why keys are getting longer and longer – to create more possible solutions and increase the resources required to perform such large computations. There are more than a few informed experts who believe that quantum computing may bring forth the ability to break codes in the foreseeable future. Some of the industry’s brightest minds are working on quantum-resistant encryption so that we can continue to exchange sensitive information privately.
There are also concerns about cost and downtime when deploying encryption schemes. For enterprise-class encryption, you used to need to account and plan for downtime while tens of thousands of files or a large database was getting encrypted. But now you have the option of enterprise encryption without downtime, with Vormetric Live Data Transformation. In fact, a database of any size or any number of files can be used while undergoing encryption. We call it zero-downtime encryption, and it’s an industry game-changer.
And now as we have more and more services moving to the cloud, encrypting and securing data is even more critical. More sensitive data is residing in the cloud, and ensuring that data is secure can be a challenging task. However, there are new strategies for cloud data protection such as transparent and application-level encryption. Additional methods of encryption can involve tokenization and dynamic data masking. I would be remiss if I didn’t add key management to the mix, as well. Compliance mandates, data-residency requirements, government regulations and best practices require that enterprises protect and maintain encryption keys in accordance with specific frameworks and laws. Allowing organizations to “bring your own key,” also known as BYOK, enables maximum control and trust between the data owner and cloud provider, and is considered a best practice for internal and external compliance controls.
Later this month, Thales will release the results of our annual Global Encryption Study. While I won’t give away the findings, I can share that keeping pace with cloud adoption and escalating threats is a major pain point for organizations and business leaders. It is our focus and vision to make protecting your data as transparent and operationally “invisible” as possible. It is a tough mission, but a worthy one. I hope you’ll download that report when it becomes available, as I think you’ll find the results eye-opening.
