In past years’ Thales Data Threat Reports, we asked IT security pros around the world separate questions about whom they believed were the riskiest internal threats and external threats. The results were useful but didn’t allow us to compare which category proved most worrisome.
This year, we restructured the two separate questions into a single one, and that gave us some very interesting results about who worries these IT security professionals the most.
For data, insiders are the top threats
When it comes to their data, IT security pro are more worried about insiders within their organizations than they are about external attackers.
If we look just at those chosen as the most dangerous threat actor, four out of the top five categories selected were insiders. The single most dangerous threat actor category that our survey identified was privileged users (23%), followed by cyber-criminals (16%). This pattern recurs when we look at the top three selections: privileged users are at the top, followed by cyber-criminals and other insiders with potential access to sensitive data.
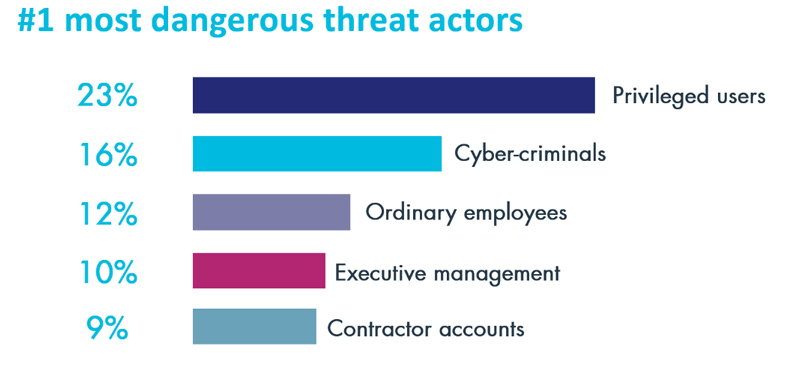
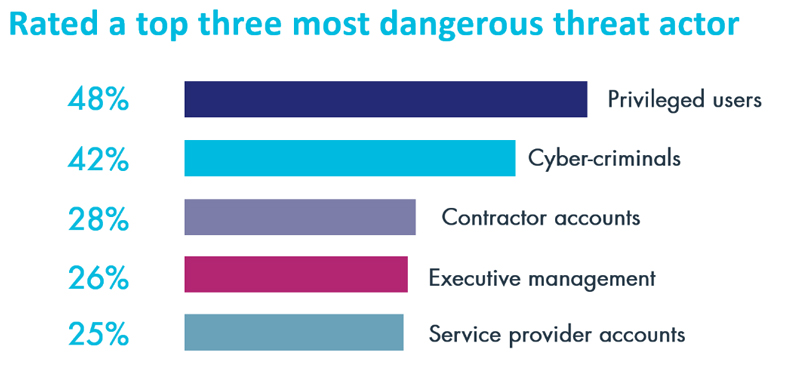
What’s most interesting about this? If you are an IT security pro, many of us (and all the vendors) make a yearly pilgrimage to San Francisco for the yearly RSA trade show. Although there are security conference rivals, this show continues to be the preeminent show for the industry. One would think the conference would at least partially focus on insider threats – but I simply didn’t see this issue emphasized. While there were vendors showcasing privileged user and insider solutions, external threats appeared to claim the lion’s share of attention.
IT security spending patterns: Yet again, protecting data is not the priority
We asked separate questions about which tools are most effective at protecting data, and where our respondents’ organizations are increasing their IT security spend. What did we find? Enterprises are consistently spending on the tools that won’t make the biggest difference in protecting data. We even found this year that people knew what worked best at protecting data, but are not prioritizing their IT security spending increases on what works best: data-at-rest security.
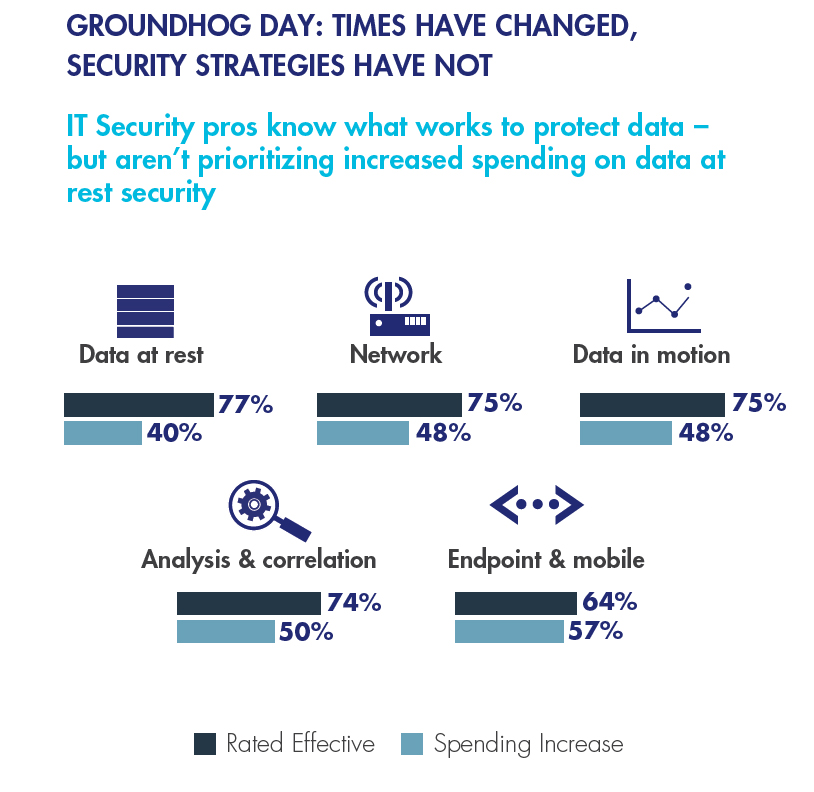
So what’s going on?
It seems clear that for most organizations, protecting their data is a secondary priority. No wonder data breach rates around the world are soaring! Here in the U.S., almost half (46%) experienced a data breach in the last year, and the pattern repeats (with some variations) around the world.
Perhaps as regulations such as the GDPR in Europe and PIPA in South Korea start to be heavily enforced, and with substantial penalties, the priorities will change – but that will be a tale for another year.
Here’s what Garrett Bekker from 451 research (the author of the 2018 Thales Data Threat Report) had to say:
“Clearly, doing what we have been doing for decades is no longer working.”
“Re-prioritize your IT security tool set - With increasingly porous networks, and expanding use of external resources (SaaS, PaaS and IaaS most especially) traditional end point and network security are no longer sufficient. Look for data security tool sets that offer services-based deployments, platforms and automation that reduce usage and deployment complexity and staffing requirements.”
For more on the results, find our global, regional and vertical Thales Data Threat Reports here.

 Andy Kicklighter | Director of Product Marketing
Andy Kicklighter | Director of Product Marketing