Results from the 2018 Thales Data Threat Report
*Source – Dataset for 2018 Thales Data Threat Report
High SaaS usage – and with Sensitive Data
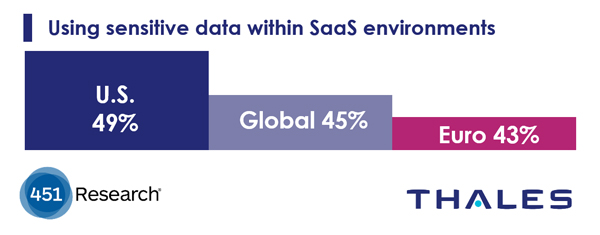
In the 2018 Thales Data Threat Report, one fact that came through very clearly is that SaaS usage by enterprises is high, and so is their use of SaaS with sensitive data. This sensitive data use in SaaS environments today is a real problem.
There are good reasons that enterprises adopt SaaS applications. One of the key reasons is that they no longer have to implement applications that their organization or business units need for HR, productivity, sales, business automation or even simple shared file share/storage inside their organizations or on their hardware. Add to this the lifetime of support, maintenance, infrastructure and training required. Organizations purchase the service and use it as needed, and are billed for what they use.
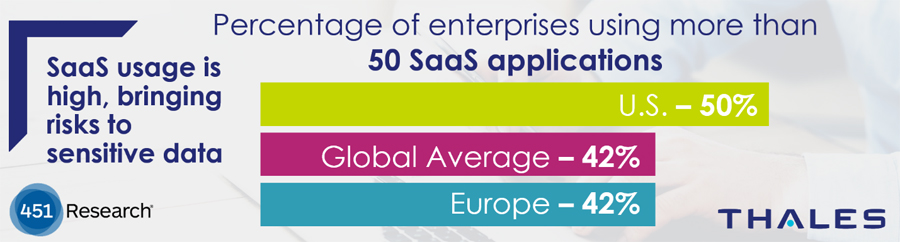
That seems simple and clear – but not when you look one step farther into the scope of enterprise SaaS deployments and their use of sensitive data within SaaS environments. In our survey data, the U.S. had the widest overall adoption of SaaS applications with 50 percent of enterprises using more than 50 services. The global and European averages were somewhat lower at 42 percent.
The biggest complication for sensitive data within SaaS environments is who has access to it. Regulatory, compliance, legal and best practice requirements limit who can be allowed to see the data—typically a small pool of enterprise groups, roles, or people who need access for their work. This small pool does not include the SaaS provider personnel.
*Source – Dataset for 2018 Thales Data Threat Report
One problem for the vast majority of SaaS applications is that they are a “black box” to the enterprise. As a result, the enterprise does not have access to, or control of, underlying infrastructure, location, architecture or security controls, to name a few of the issues. When applications were implemented within the legacy four walls of the enterprise, even if implemented using software from an outside vendor, the vast majority of these items could be put under the enterprise’s control. However, a “black box” eliminates this control set almost entirely.
Some of the leading SaaS vendors have already implemented solutions to this problem – but today it’s a small set. Leading SaaS environments such as SalesForce and Microsoft’s Office 365 have implemented interfaces and tools that allow organizations to encrypt their data-at-rest within these environments while preserving full functionality. If organizations have the resources and tools available to build out secure infrastructure and interfaces, they are able to control their encryption keys. However, this is far from the rule today. The vast majority of SaaS applications have not enabled this level of functionality. For many, the problem is simply resources – they lack the scale and people to build-out and maintain these capabilities. So in order to meet organizational requirements, customers look to third-party options that can help them implement what’s needed (we at Thales are among the few making this possible for medium and smaller SaaS vendors).
Other problems – Who manages the keys? All of those keys?
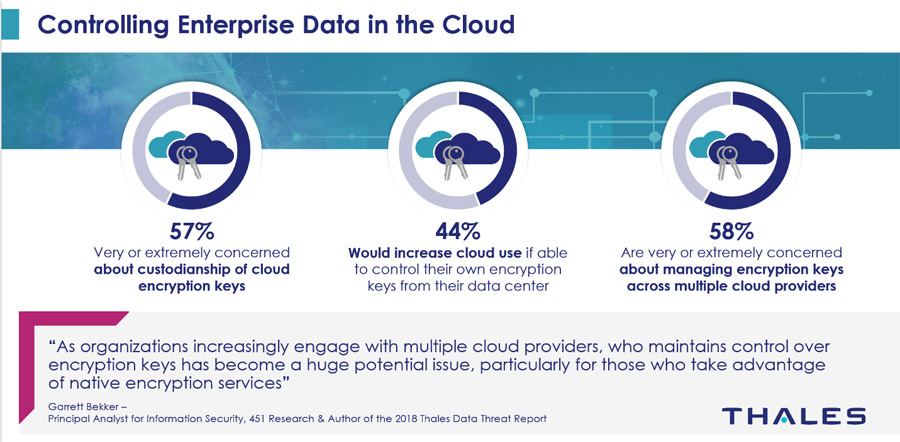
If the enterprise manages and stores their encryption keys remotely from the SaaS provider’s environment, a whole host of worries around their sensitive data is eliminated, including:
- Compromises due to attacks at the SaaS provider. Even if a SaaS infrastructure is compromised, enterprise data is safe as it requires the key for access;
- Location of their data – It’s always encrypted and the enterprise has the keys. Even if stored in a remote legal jurisdiction, data can only be compelled from the organization itself, not the SaaS provider; and,
- Compliance requirements – So long as the SaaS application also has access controls built in, requirements for access controls within and without the enterprise are met.
However, many organizations seem to miss the point that control of their keys equals control of their data. Forty-one percent of respondents identified that their organization would increase cloud usage via encryption with keys managed by the cloud provider. Yes, this is better than not encrypting the data at all, but this option still leaves enterprises at risk from issues at the SaaS provider as noted earlier.
Another problem also becomes managing encryption keys and security controls across the wide range of SaaS environments in use (remember that 50 percent of enterprises are using more than 50 SaaS solutions today). Solutions and platforms that help organizations reduce the complexity of keeping access policies and encryption controls consistent with centralized policy management need prompt consideration as well.
What needs to be done?
Organizations need to understand just where their sensitive data is being stored and used. The next step is to evaluate whether the advantage of SaaS resource use offsets any risks to compliance, regulation and operational practice for their organization. SaaS providers that can provide the degree of security required for enterprise data should get precedence for selection and use.

 Andy Kicklighter | Director of Product Marketing
Andy Kicklighter | Director of Product Marketing