One of the biggest challenges in data security today is the rapid growth in complexity of the average enterprise IT infrastructure. An organization’s IT infrastructure is no longer limited to desktop computers and servers. Instead, there is a clear growth in the adoption of multi-cloud services. According to the 2020 Thales Data Threat Report - Global Edition, organizations use 29 different cloud services on average. With increasingly blurred security perimeters, organizations are challenged to implement and manage consistent unified policies to their distributed IT resources.
Every business has a mix of legacy and new platforms. However, with new platforms come new risks. Each new environment that an IT security team needs to learn to configure, monitor, and secure is one more opportunity for an oversight or mistake that can easily result in a data breach. This is further complicated by the increasing number of global and regional privacy regulations with differing compliance requirements. To effectively comply, organizations can no longer rely on siloed and traditional approaches to secure their sensitive data.
Let’s solve the complexity problem
In addition to the high amount of regulations and increased cloud use (not to mention a highly-distributed workforce), we have witnessed explosive data growth. All of these factors combined is putting sensitive data at risk. And a lack of visibility and operational complexity has resulted in organizations not knowing where all of their sensitive data is stored. This concern around complexity is real, as pointed out in the 2020 Thales Data Threat Report-Global Edition in which nearly 40% of the respondents identified it as the number one barrier to security.
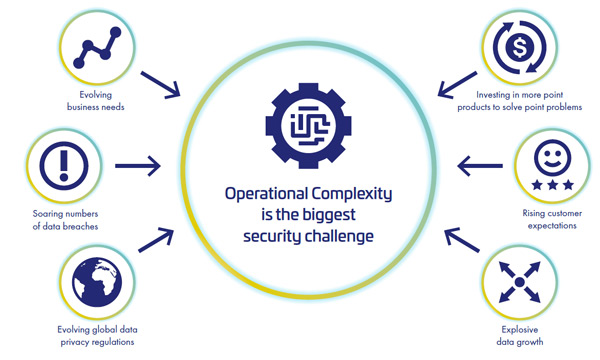
Fig.1: Operational complexity is the top barrier to deploying data security
Introducing next-generation unified data protection
Leveraging Thales’s years of data protection innovation, we’ve combined the best of our Vormetric and SafeNet KeySecure technologies to give organizations the power to keep sensitive data secure on premises and in the cloud, all from a single platform. Thales’s new CipherTrust Data Security Platform also reduces total cost of ownership for organizations of all sizes by simplifying data security, accelerating time to compliance, and securing cloud migrations.
Built on an extensible infrastructure, the new platform enables IT and security departments to discover, classify and protect data-at-rest in a uniform and repeatable way. Additionally, data security administration is simplified with a ‘single pane of glass’ centralized management console that equips organizations with powerful tools to combat external threats, guard against insider abuse, and establish persistent controls.
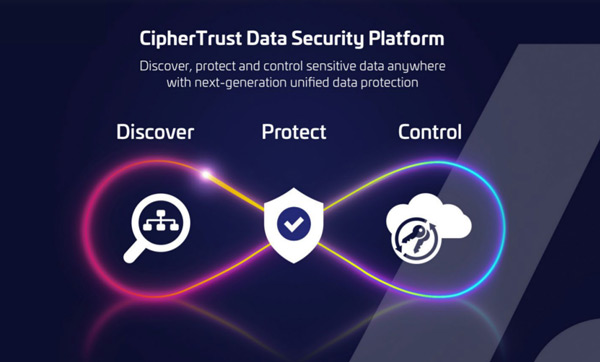
Fig.2: Thales CipherTrust Data Security Platform
Complexity no longer has to be an issue. With the introduction of Thales’s CipherTrust Data Security Platform, organizations can secure their most sensitive data. Here’s how:
- Discover: An organization must be able to discover data wherever it resides and classify it. This data can be in many forms: files, databases, and big data and it can rest across storage on premises, in clouds, and across back-ups. Data security and compliance starts with finding exposed sensitive data before hackers and auditors. The new solution enables organizations to get complete visibility into sensitive data on-premises and in the cloud with efficient data discovery, classification, and risk analysis.
- Protect: Once an organization knows where its sensitive data is, protective measures such as encryption or tokenization can be applied. For encryption and tokenization to successfully secure sensitive data, the cryptographic keys themselves must be secured, managed and controlled by the organization. The new platform provides comprehensive data security capabilities, including file-level encryption with access controls, application-layer encryption, database encryption, masking, vaultless tokenization with policy-based dynamic data masking and vaulted tokenization to support a wide range of data protection use cases.
- Control: Finally, the organization needs to control access to its data and centralize key management. Every data security regulation and mandate requires organizations to be able to monitor, detect, control and report on authorized and unauthorized access to data and encryption keys. The platform delivers robust enterprise key management across multiple cloud service providers (CSP) and hybrid cloud environments to centrally manage encryption keys and configure security policies so organizations can control and protect sensitive data in the cloud, on-premises and across hybrid environments.
As the business landscape continues to change (especially as data migrates to the cloud at a rapid pace from a highly-distributed workforce) organizations need a clearer view of all of their data so it can be discovered, protected and controlled.
For more information on how to simplify data security, watch our webinar, “Discover, Protect & Control Your Data in the Cloud.”

 Nisha Amthul | Senior Product Marketing Manager
Nisha Amthul | Senior Product Marketing Manager