With more and more organizations embracing digital transformation and accelerating their pace to digitize every piece of information, they become increasingly vulnerable to sophisticated cyber-attacks and data breaches.
As highlighted in the 2019 Thales Data Threat Report, an increasing number of organizations across the globe are now using sensitive data on digitally transformative technologies like cloud, virtualization, big data, IoT, blockchain, etc. that further increases their exposure to data breaches, as safeguarding sensitive data within these new technology environments becomes a complex task.
With the global spend on digital transformation slated to reach a whopping $2.3 Trillion by 2023, data security challenges are further poised to go up – unless organizations take a conscious decision to implement a cohesive data protection strategy at an organization level that shuns the traditional siloed approach towards data security.
In our earlier blog post, we had urged organizations to rethink their Enterprise Data Protection Strategy and recommended four key technologies for optimal data protection. In this post, we’ll elaborate on how organizations can finalize the best approach to implement data encryption at an organizational level in an agile and efficient way.
When it comes to optimal data protection, encryption is widely considered as the best strategy to safeguard data from cyber attacks, as any encrypted data is rendered useless without its corresponding decryption key. The surest way of safeguarding sensitive data is first identifying where it flows and resides (on-premises, cloud and virtual environments, within file servers, applications, databases, and virtual machines, and the network through which it flows) and then encrypting it. In a nutshell, no matter it’s data-at-rest or data-in-motion, it should be encrypted regardless of its state.
Ground Reality: The Problem of Plenty!
While most organizations acknowledge that encryption is the best data protection technology available today, the ground reality is that many organizations procrastinate data encryption because they find it a complex and arduous task.
With both legacy in-house applications and new digitally transformative environments to protect, organizations today find themselves encumbered with a multi-point ecosystem of diverse data encryption solutions. The complexity is further aggravated with each solution requiring its own contract, maintenance, infrastructure, internal resources, integration with other enterprise tools, etc.
This silo approach of multiple islands of encryption leads to a problem of plenty that makes the entire encryption exercise complex, inefficient and expensive.
The Way Forward – Choosing the Correct Approach to Data Encryption
With multiple environments to protect simultaneously, a silo approach complicates the situation instead of resolving it. To break this conundrum, organizations should adopt a comprehensive approach by asking – what are the various risks we aim to mitigate by implementing data encryption?
How is data stored and used: What are the risks and how to mitigate?
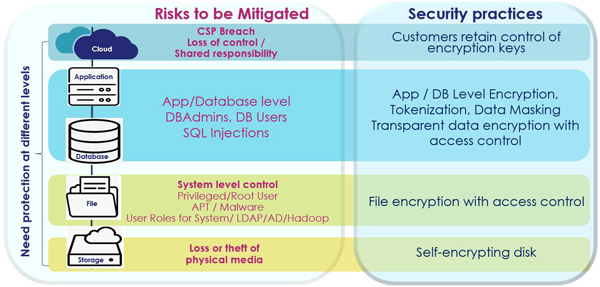
A pertinent point to note in the above table is that the lower the items in the stack, the weaker is the protection level they offer, though being the easier to implement.
Begin with the bottom of the stack that covers the protection of physical devices through Full Disk Encryption (FDE) that offers basic protection in the event of the physical loss, theft or improper disposal of a storage device. A rudimentary approach at best, FDE is rendered useless when the physical device is turned on, as there is no defense mechanism against data access threats from within the device’s systems or applications. While FDE may work for individual devices like a laptop, it offers no cohesive protection to an organization’s system and network infrastructure. Barring a cursory checkmark on the encryption mandate from a compliance perspective, FDE offers very little protection against data breaches.
As we move up the stack, the protection level progressively strengthens with each layer as protection is offered against the risks from the layer below, as well as from those at its own layer.
The second layer of the stack covers system-level protection controls. Using File Folder Encryption (FFE), these protection mechanisms control and manage access at the system level, that includes privilege system users such as system administrators, storage administrators, network administrators, etc. that have master access to all the data of a respective system that they have access to. The FFE approach is best suited for organizations that need to deploy a protection mechanism quickly. With RESTful APIs, data protection can be easily customized for each system and quickly deployed in a fully automated manner.
At the third layer of the stack, we encounter App/Database Encryption that encrypts data at its source of generation itself by allowing developers to protect the data from within the applications and databases along with the system and physical layers. For database protection, a Transparent Data Encryption (TDE) Key Management solution is recommended to safeguard and manage the master encryption key to prevent the database administrator from misusing it. While App/Database Encryption offers the highest level of protection, it is also one of the most complex data protection mechanisms to implement.
Lastly, we come to Cloud Data Encryption. While Cloud Service Providers (CSPs) provide data-at-rest encryption, the industry best practice defined by the Cloud Security Alliance recommends that the encryption keys should be stored and managed remotely from the CSP’s systems and encryption operations. Popularly known as Bring Your Own Key (BYOK), the encryption keys of the cloud data are controlled and managed by the customers themselves that give them the flexibility of the separation, creation, ownership, and control – including revocation, of the encryption keys or tenant secrets that were used to create them. For optimal data protection in growing multi-cloud environments, leading organizations across the globe use Thales’s BYOK solution that is seamlessly integrated with Microsoft Azure, Amazon Web Services and Salesforce.com.
While TDE Key Management (for databases) and Cloud Encryption solutions offer the best level of data protection, they are quite complex to implement due to the proliferation of multiple environments. With thousands of databases and hundreds of cloud applications, just managing the encryption keys throughout their lifecycles becomes a daunting task. This is where a centralized, robust key management platform comes handy in efficiently managing the ever-growing heterogeneous encryption environments in large organizations.
To Sum It Up
One of the key findings in the 2019 Thales Data Threat Report is that no organization is immune to data security threats. As cyber-attacks get more sophisticated, encrypting the sensitive data-at-rest and implementing robust access control mechanisms must be the fundamental component to any organization’s successful cybersecurity strategy.
But mere data encryption will not suffice as key management plays an equally pivotal role in optimal data protection. Organizations should ask themselves the below pertinent questions:
- Where are our encryption keys stored?
- Who controls them?
- Do they work seamlessly with our 3rd party applications?
- Are these keys trusted?
- Will they easily pass an audit?
Thales Cloud Protection & Licensing offers a cohesive solution that addresses all these questions. From consulting to deploying the apt encryption solution, Thales’s wide gamut of security solutions spans data centers, WAN environments, public, private and hybrid clouds, big data and other digitally transformative technologies. Through Thales’s single platform, organizations can seamlessly manage their entire data security environment centrally.
No matter where the data moves within an organization or the new security mandates introduced or new disruptive technologies implemented in an organization, Thales’s robust data security platform will cohesively facilitate a centrally controlled and consistent data security strategy with its inherent flexibility, scalability, and the efficiency to meet both existing and new use cases.
For questions, please contact ved-v.prakash@thalesgroup.com.
