While ransomware attacks have been around for decades, their frequency has exponentially increased in the last few years, let alone the past several months during the pandemic.
The potency of a ransomware attack lies in its diabolical ingenuity. Once the hackers gain an inside entry in an organisation’s IT systems, they deploy a file-encrypting malware known as ransomware. The attackers then demand a ransom for decrypting the affected files.

With cybercriminals getting more sophisticated with every passing day, ransomware attacks have evolved from “spray-and-pray” attacks targeted at small and medium businesses to “big game hunting (BGH)” attacks targeted at large businesses that have the financial capability to pay large ransoms. Global GPS giant Garmin and leading camera-maker Canon are two recent examples of ransomware attacks on large businesses.
Cybersecurity Ventures predicts that businesses will fall victim to a ransomware attack every 11 seconds with the global ransomware damage costs reaching $20 billion by 2021. The ransomware threat landscape is no different in India.
Sophos’ recent report, The State of Ransomware, reveals that paying the ransom can end up costing companies double the overall remediation cost versus not paying or getting the data back through backups or other methods. For example, the average cost to remediate a ransomware attack costs US$1,448,458 and US$732,520 for those that did not pay the ransom. India topped the global ransomware attacks chart with 82% of Indian organisations revealing that they were hit by ransomware last year. The report further reveals that 66% of the affected Indian companies paid ransom to get their data back.
Mitigating Ransomware Attacks
With rising incidents of ransomware attacks, organisations are finally realising that merely implementing perimeter defense systems no longer suffice to protect their sensitive data. To that end, my colleagues have published blog posts over the past couple of months about the rise in ransomware attacks, how to prevent them and specifically how to protect remote desktop protocol endpoints.
While front line defense mechanisms like firewalls, anti-theft, anti-spyware, etc. act as a deterrent against cyberattacks, they are rendered useless when a hacker gains inside entry by exploiting their vulnerabilities to bypass them.
Since almost all enterprises have well established backup and restoration processes in place, their primary worry is around the leakage of sensitive data in the public domain. So, even if they can confidently restore their operations from a ransomware attack, they still end up paying the ransom to ensure the data does not get into the public domain. For optimal data protection, organisations should first identify where their sensitive data resides – on premises, in the cloud or in hybrid environments, and then encrypt it. Encrypting data-at-rest makes the data worthless to intruders when they attempt to steal business-critical or sensitive data and threaten to publish it, if the ransom is not paid. Some ransomware selectively seeks out sensitive data and will only encrypt those files. In these cases, pre-encrypted files aren’t able to be scanned by the malware and are thus not attacked.
However, merely encrypting data is not sufficient. With data encryption, the risk is transferred from the data to the encryption keys, and hence safeguarding the encryption keys is pivotal to data protection.
Decoupling Encryption Keys From Encrypted Data
One of the common mistakes many organisations commit is storing encryption keys together with the encrypted data. This practice renders the entire encryption exercise futile as in the event of a breach, cyber criminals can easily acquire the encryption keys and thereby obtain control of the encrypted data.
As a best practice, encryption keys should always be decoupled i.e. separately managed from the encrypted data.
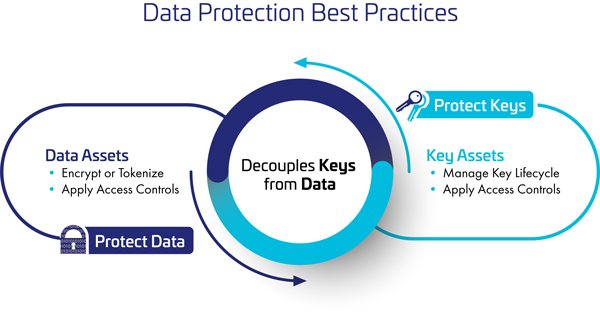
Fig.1 Data Protection Best Practices
Below are a few pertinent questions that organisations should ask during the decoupling exercise:
1. Is the encrypted data and its corresponding encryption keys managed and owned by the same custodian?
2. How is the separation of duties that is ensured during the encryption process implemented in individual applications?
3. Do respective application owners also manage and own the encryption keys used for encrypting their applications’ sensitive data?
4. Do the storage/system administrators also own and manage the encryption keys used for data-at-rest encryption?
5. What is the secure escrow procedure followed for these keys?
6. What is the rotation schedule of these keys and how are they managed and audited?
To Sum It Up
Securing and managing encryption keys is critical to ensure the integrity of any encryption system. In a future blog post, I will cover the fundamentals of key management and the best practices organisations should adopt to protect their sensitive data from sophisticated ransomware attacks.
In the meantime, Prevent Ransomware Attacks From Disrupting Your Business will help you understand the anatomy of ransomware attacks and the steps you should take to prevent them from disrupting your business.

 Rana Gupta | APAC Regional VP, Data Protection
Rana Gupta | APAC Regional VP, Data Protection