We all know the story of the Little Dutch Boy that Mary Mapes Dodge made famous in Hans Brinker, or The Silver Skates. It is a story within a story, in which a Dutch boy saves Holland by putting his finger in a leaking dike. AWS has a lot of features to protect Amazon S3 buckets, but unfortunately they don’t have the equivalent of a “Little Dutch Boy” generally available.
The difficulty in configuring and maintaining S3 isn’t new. I did a quick search and found an article from 2013 that highlighted how private data could be exposed due to Amazon S3 buckets being left open. Back in 2017, I was actually on a panel discussing S3 data leaks, and, as it turned out, that was a particularly bad year for Amazon S3 configuration mishaps (some of the biggest stories that you’re thinking about right now took place in 2017). Incredibly, the leaks keep happening.
Don’t believe me? All you have to do is a Google search ‘AWS S3 Data Leak’ and select ‘past month’ under tools. Unfortunately, there are always new stories of companies losing their data. And one can only imagine how much data was siphoned off and not reported. On average, a misconfigured S3 bucket is discovered in 10 minutes. There is no room for error.
Why doesn’t AWS do something about this problem?
AWS has given customers opportunities to acquire many tools to help address this problem. Here are some examples:
- Macie, August 2017
- GuardDuty, November 2017 with additional S3 security features added in October 2019
- Access Advisor, December 2018
- Scanning Public IP Addresses, September 2019
- New Enhanced (less expensive) Macie, May 2020
AWS also offers Amazon S3 encryption by default (hint: you need to enable it!). This is good, but if your key management policy is equivalent to your access policies, then you will still leak data when you make a mistake on your access policies. In short, this means if you allow your employees to create their own S3 buckets and policies, encryption being enabled on S3 probably won’t avoid a leak if they don’t have cloud and access management expertise. (hint #2: when you enable default encryption—data already in your bucket is still in clear-text).
Protect your company from becoming a data leak search result
Security professionals know that native cloud encryption, like S3, is similar to full disk encryption (FDE). FDE makes sense on laptops and phones because these are devices that we lose control of—they are easily lost and stolen. Whomever has these devices doesn’t have access to the passwords or keys and therefore no access to the data. This is why governments hate device level encryption. However, when FDE is used on data center storage (in your data center or virtual storage in the cloud) the risk isn’t that these storage solutions will be stolen. The risk is that a misconfiguration will leak the data or a hacker will gain access to these drives. Once the encryption key is applied to these kinds of storage solutions, the data is in the clear. It is the same as if someone steals your cell phone while it is unlocked. They will have access to all your information.
The only two groups that like FDE in data centers are compliance bureaucrats because it gets them a checkmark and hackers because it doesn’t stop their access to the data in clear-text once they breach the perimeter security. Aberdeen has written a great white paper on the risks addressed with different types of encryption.
Security professionals typically run encryption on the workload servers, database servers, file servers or they assure that the application uses encryption or tokenization from the time of data creation. It is odd that so many organizations have lost this hygiene when moving to the cloud. We can’t blame Amazon, as they make it very clear in their shared responsibility model. There is even a song about it! Sing with me, “They protect what’s of the cloud, you protect what’s in, and that’s security best practices!”
The answer is simple, treat cloud storage like your own storage
When you want to control data, anywhere, you encrypt and manage the keys. This is data security 101 and most organizations follow this practice within their own data centers. So why haven’t we done this for S3? One reason for not encrypting data stored in S3 is that that vendors, like Thales, didn’t make it easy. Amazon S3 is object storage, and traditional agent based encryption solutions didn’t support object storage the same way they have supported block and file storage like Amazon Elastic Block Store (EBS), Amazon EC2 Instance Store and Amazon Elastic File System (EFS). In the past, in order for a traditional agent solution to encrypt data destined for object storage it needed a proxy to convert protocols from block storage to object storage, such as the AWS Storage Gateway. The gateway is an additional cost, adds latency, and adds complexity. It isn’t a graceful solution.
A graceful solution for protecting Amazon S3 to the rescue
The Vormetric Data Security Platform from Thales offers scalable, low latency encryption of files and databases using Vormetric Transparent Encryption. For almost a decade this solution has supported the block and file storage solutions from AWS, and practically every other virtual and physical storage solution you’ll encounter in any cloud and data center. The same solution now natively supports Amazon S3 buckets with additional object storage solutions on our roadmap. In addition, this solution offers FIPS 140-2 centralized enterprise key management from virtual and physical appliances.
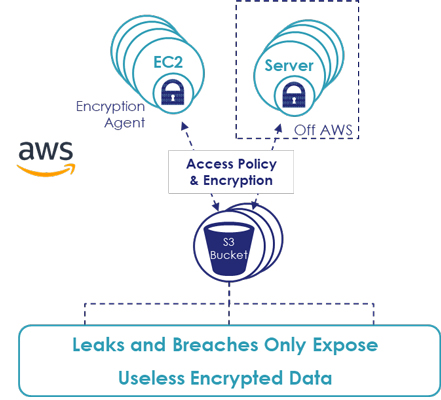
As a result, you can deploy these agents on your AWS EC2 servers or your on-premises servers, so that data destined for S3 buckets will be encrypted starting at the server, through the network, and at rest in the S3 bucket. The access polices are centralized and controlled by your security professionals. If this is a business S3 resource, no data goes in or out that isn’t encrypted, controlled, logged and made available to only authorized users and processes. This solution enables you to take responsibility for all your company’s data in the cloud and prove it to auditors through audit logs. It is simple and it is graceful. If for any reason data was to leak, it would be encrypted and the company would be saved because their sensitive data wouldn’t flood out. It is like having the Little Dutch Boy personally on hand to protect your company.
You can learn more by reading our white paper, Avoiding Amazon S3 Data Leaks with Scalable Encryption and Access Controls.

 Charles Goldberg | VP, product marketing
Charles Goldberg | VP, product marketing