NIST 800-53, Revision 4
Regulation | Active Now
NIST Special Publication 800-53, Revision 4 provides a catalog of security controls for federal information systems and organizations and assessment procedures.
Thales helps organizations with NIST 800-53 compliance through the following:
- Data encryption and key management
- Access policies and privileged user controls
- Security intelligence
- Regulation
- Compliance
NIST Special Publication 800-53, Revision 4
According to NIST Special Publication 800-53, Revision 4:
[It] provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations … , organizational assets, individuals, other organizations, and the Nation from a diverse set of threats ….
The controls are customizable and implemented as part of an organization-wide process that manages information security and privacy risk. The controls address a diverse set of security and privacy requirements across the federal government and critical infrastructure, derived from legislation, Executive Orders, policies, directives, regulations, standards, and/or mission/business needs.
The NIST 800-53 publication also describes how to develop specialized sets of controls, or overlays, tailored for specific types of missions/business functions, technologies, or environments of operation.
Finally, the catalog of security controls addresses security from both a functionality perspective (the strength of security functions and mechanisms provided) and an assurance perspective (the measures of confidence in the implemented security capability). Addressing both security functionality and security assurance ensures that information technology products and the information systems built from those products using sound systems and security engineering principles are sufficiently trustworthy.
How Thales Can Help You Comply with NIST 800-53, Revision 4
Core Thales capabilities that help meet all these NIST 800-53, Revision 4 compliance standards include:
- Encryption and Key Management: Strong, centrally managed, file, volume and application encryption combined with simple, centralized key management that is transparent to processes, applications and users.
- Access Policies and Privileged User Controls: Restrict access to encrypted data – permitting data to be decrypted only for authorized users and applications, while allowing privileged users to perform IT operations without the ability to see protected information.
- Security Intelligence: Logs that capture access attempts to protected data, providing high value security intelligence information that can be used with a Security Information and Event Management (SIEM) solution and for compliance reporting.
For a full look at how Thales solutions map to NIST 800-53 compliance requirements, see our Vormetric NIST 800-53 Mapping white paper with detailed mapping of security controls to Thales product features.
In addition to helping you comply with NIST 800-53, Revision 4; FISMA; FIPS 140-2; FIPS 199; FIPS 200 and FedRAMP, Vormetric security solutions from Thales are designed to help you comply with:
- Common Criteria
- HIPAA-HITECH
- PCI DSS
- Other standards that will arise
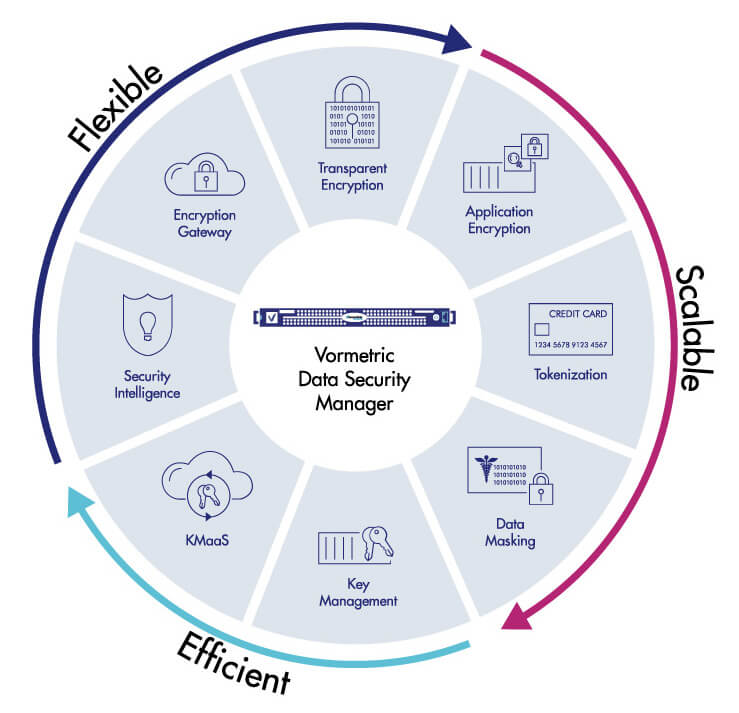
The Vormetric Data Security Platform
The Vormetric Data Security Platform from Thales is the only solution with a single extensible framework for protecting data-at-rest under the diverse requirements of Federal Agencies across the broadest range of OS platforms, databases, cloud environments and big data implementations. The result is low total cost of ownership, as well as simple, efficient deployment and operation.
Vormetric Transparent Encryption
Vormetric Transparent Encryption from Thales provides file and volume level data-at-rest encryption, secure key management and access controls required by regulation and compliance regimes.
Vormetric Key Management
Vormetric Key Management from Thales enables centralized management of encryption keys for other environments and devices including KMIP compatible hardware, Oracle and SQL Server TDE master keys and digital certificates.
Vormetric Data Security Intelligence
Vormetric Data Security Intelligence from Thales provides another level of protection from malicious insiders, privileged users, APTs and other attacks that compromise data by delivering the access pattern information that can identify an incident in progress.
Vormetric Application Encryption
Vormetric Application Encryption enables organizations to easily build encryption capabilities into internal applications at the field and column level.
Vormetric Tokenization with Dynamic Masking
Vormetric Tokenization with Dynamic Masking from Thales lets administrators establish policies to return an entire field tokenized or dynamically mask parts of a field. With the solution’s format-preserving tokenization capabilities, you can restrict access to sensitive assets, yet, at the same time, format the protected data in a way that enables many users to do their jobs.
Andere wichtige Datenschutz- und Sicherheitsvorschriften
DSGVO

VERORDNUNG
JETZT AKTIV
Die DSGVO ist vielleicht die bisher umfassendste Datenschutznorm und betrifft jede Organsation, die personenbezogene Daten von EU-Bürgern verarbeitet - unabhängig davon, wo die Organisation ihren Sitz hat.
PCI-DSS

MANDAT
JETZT AKTIV
Jede Organisation, die eine Rolle bei der Verarbeitung von Kredit- und Debitkartenzahlungen spielt, muss die strengen PCI-DSS-Anforderungen für die Verarbeitung, Speicherung und Übermittlung von Konteninformationen erfüllen.
Gesetze zur Benachrichtigung bei Datenverletzungen

VERORDNUNG
JETZT AKTIV
Vorschriften zur Benachrichtigung bei Datenschutzverletzungen nach dem Verlust personenbezogener Daten wurden von Ländern rund um den Globus erlassen. Sie variieren je nach Gerichtsbarkeit, enthalten aber fast immer eine "Safe-Harbour"-Klausel.



