Protect data anywhere
Add data protection easily – regardless of the layer or use case – with CipherTrust Data Security Platform (CDSP).
CDSP provides developer-friendly tools to decrease the time and resources required to manage data security and achieve compliance.
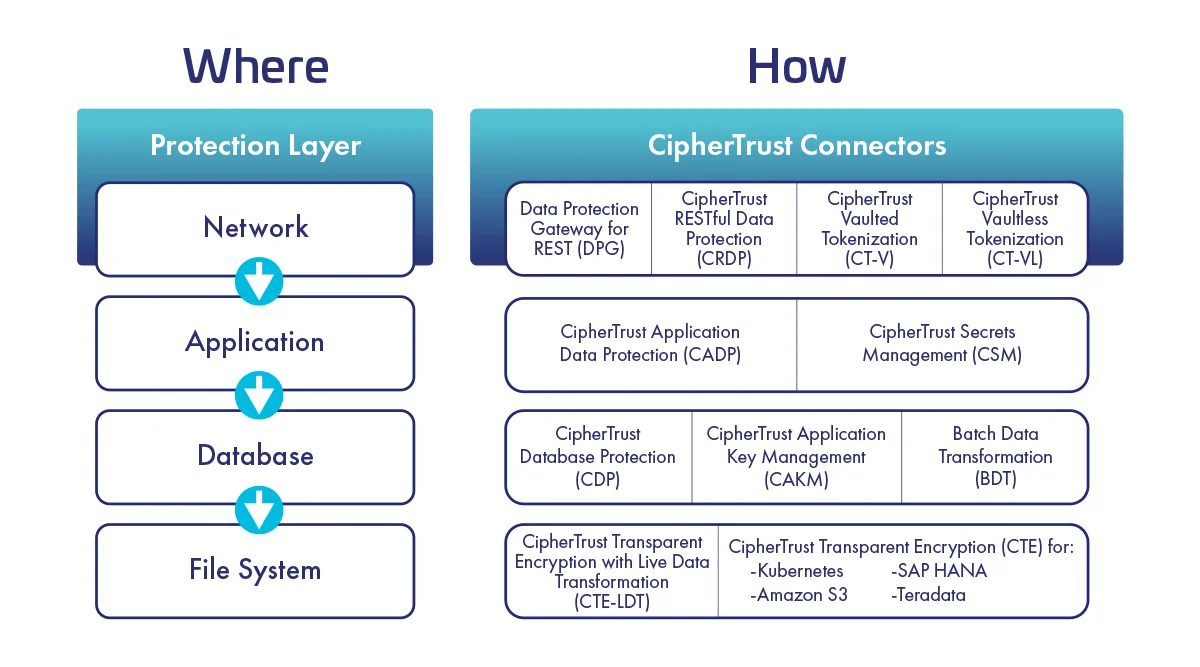

Solutions for each layer of technology stack to match your security requirements and infrastructure.
Simplify secrets management
Be agile changing ciphers, parameters, keys
Minimize DevSecOps effort to add and maintain data protection
- Developer-friendly APIs. Zero cryptography skills needed
- Deploy code quickly while managing security centrally
- No Dev dependency to update ciphers, parameters or keys
DevOps (Development Operations) tries to maximize the velocity of software delivery, while Data Security ensures that sensitive data does not fall into the hands of bad actors or the competition. The CipherTrust Data Security Platform bridges the gap between DevOps and Data Security, by providing a clear separation of duties allowing each to successfully fulfill their responsibilities efficiently.
Demonstrate compliance
- SIEM-compliant audit records show who had access and how they saw the data
- Sensitive data is protected
- Separation of duties
Our most popular resources for DevSecOps
Thales docs
Home to all of your Thales product and service documentation needs.
Thales GitHub repositories
Get access to sample code, APIs, and open-source solutions.




