Deployment Services
- Standard deployments
Our Professional Services team can propose an off-the-shelf offer called “ServicePack”, for every standard solution deployment not requiring any custom scope.
ServicePacks are pre-defined service offerings that deliver on the most common requirements associated with our access management and encryption products.
Each ServicePack comes with:
✔ A pre-defined contractual Scope of Work ready to be signed
✔ Standard terms and conditions
✔ A fixed price
More than 75 ServicePacks are already available for both Access Management and Encryption solutions, with options for deployment approach (onsite or remote) and associated services:
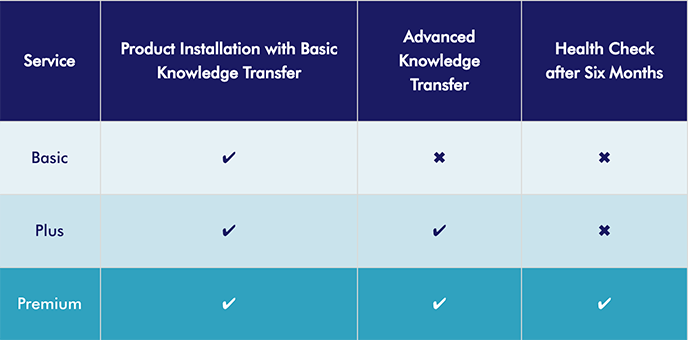
Such off-the-shelf services shorten the project planning and execution while maintaining high quality in our service delivery engagements.
In case our standard services do not meet your needs, we also propose custom deployments to address your specific needs and objectives.
- Custom deployments
Our expert team is fully dedicated to understanding your needs and designing the best solution for you.
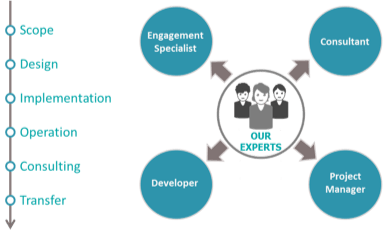
Services are delivered by our experts who offer complementary profiles covering the full range of services for a successful deployment:
✔ Project study & feasibility
✔ Solution architecture & design with development services
✔ Smooth and efficient project delivery
✔ End-to-end testing in the customer’s environment
✔ Guidance & technical expertise during project life cycle
✔ Knowledge transfer & handover with the customer
✔ Additional consultancy if needed, visit our Consulting Services
Should you need more information please contact your Sales Representative.
