CipherTrust Transparent Encryption for SAP HANA
CipherTrust Transparent Encryption safeguards SAP HANA data enabling enterprises to meet rigorous security, data governance, and compliance requirements. The solution can be quickly deployed and requires no changes to SAP HANA or the underlying database or hardware infrastructure. With this solution, organizations can encrypt SAP HANA data and log volumes, and establish strong governance and separation of duties.
CipherTrust Transparent Encryption for SAP HANA is reviewed and qualified by SAP as suitable for use in SAP solution environments
- Benefits
- Features
Establish Strong Controls
Encrypt SAP HANA data and log volumes and prevent privileged users from gaining unauthorized access to sensitive data.
Streamline Encryption Implementation
Protect and control access to the SAP HANA Persistence Layer without having to make any changes to SAP HANA or associated applications and infrastructure.
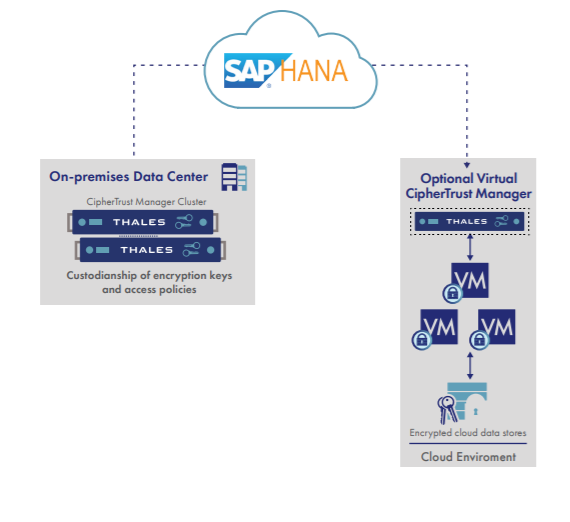
Retain Control in the Cloud
Encrypt data in cloud environments and other multi-tenant infrastructures while retaining custodianship of encryption keys.
Centralized Policy and Key Management
Leverage the CipherTrust Manager to establish robust, centralized control over encryption keys, security policies, and audit logs. Capture granular audit logs that support audits and compliance reporting. Logs can easily be integrated with SIEMs to foster improved intelligence, remediation, and controls.
Comprehensive Coverage
Establish safeguards to structured and unstructured data in SAP HANA’s persistence layer, associated databases, and log and configuration files. The CipherTrust Live Data Transformation option eliminates the downtime required for initial encryption and scheduled rekeying operations.
Robust Controls
Establish auditable, granular controls to guard against abuse of privileged users and other internal staff. Implement well-defined, strong separation of duties between data and security administrators. Leverage a FIPS 140-2 Level 3 compliant appliance.



