 New Product - The Vormetric Cloud Encryption Gateway
New Product - The Vormetric Cloud Encryption Gateway
In our professional lives, we’re often confronted with a choice between expediency and security. In that arena, security, more often than not, comes out the loser.
Employees have grown increasingly reliant on technology, and if a new technology helps them to do their jobs better, faster, or more efficiently, they’ll use that technology—security consequences be damned [with little or no consideration of the security risks they may introduce].
ClickToTweet: Security & Expediency for Cloud Storage in AWS S3 and Box @chvrles #DefenderOfData http://bit.ly/1JqbdiW
Employees all have their specific charters, performance objectives, and incentives. Most often, those have nothing to do with IT security. This reality has created a recurring pattern over time. IT security teams will restrict a new technology or ignore a new approach, employees will go their own way, and, sooner or later, IT will be forced to catch up, and do it the right way.
Years ago, security folks were wary of Wi-Fi—and for good reason. That didn’t keep employees from bringing in their own wireless routers so they could start checking email when they were stuck in conference rooms. If corporate email policies were too restrictive, people would use their own personal email accounts. (Insert your own Hillary Clinton or Sarah Palin joke here, depending on the side of the aisle you live on). It wasn’t too long ago that many IT teams were still trying to stem the BYOD tide; we all know how that went.
Therefore, it shouldn’t be a surprise that with limits on email attachment sizes not increasing as fast as the size of files needed for collaborating with distributed teams, people started going their own way and using cloud storage services. Where this usage may have started with occasional posting of a large slide deck, video or graphics file, now entire departments are using cloud storage services like Box as their standard repositories. Another example: In exactly the same way that users have been pulling out credit cards to instantly bring up a server in the cloud, instead of waiting for an IT provisioned service, they are are now using services like Amazon Simple Storage Service (Amazon S3) to create elastic storage and backup repositories.
There have been plenty of examples already in which these cloud storage vehicles have been breached—and it’s not just celebrities being exposed. As the use of cloud storage becomes more strategic, increasing volumes of sensitive corporate data will be in play. Like other technology shifts before, cloud storage has emerged as a broadly used technology—and left unchecked this usage can result in some serious damage. Like with the other trends outlined above, ignoring the risks won’t make them disappear. 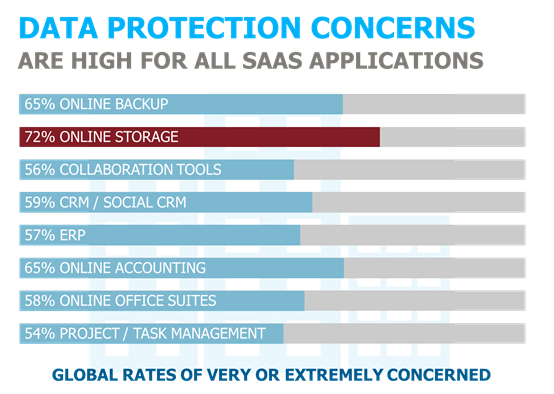 It's a top worry for IT, as shown in the results of our 2015 Vormetric Insider Threat Report where cloud storage environments returned the highest rates of concern of any SaaS application.
It's a top worry for IT, as shown in the results of our 2015 Vormetric Insider Threat Report where cloud storage environments returned the highest rates of concern of any SaaS application.
If you can’t beat them—join them. Sooner or later, IT teams began delivering the secure and controlled solutions that eliminated the need for personal Wi-Fi for getting wireless access. Ultimately, IT teams establish the controls, technologies, and policies that enable employees to take advantage of the capabilities they need to be productive, while mitigating the risks posed by having them go it alone. Now’s the time for IT teams to do the same with cloud storage.
We know what users want is simple—no change to the current file sharing experience that makes them more productive. What does IT and the compliance office want? They want to unlock cloud storage services for their organization, while locking down their data. Enterprises need to be able to prove to auditors that the data never leaves their premises unencrypted and thereby removing any concerns about the security of the cloud provider's environment. Equally important, they must show that they control this data because they never relinquish control of the encryption keys. They need to have audit trails of which users and applications are accessing the cloud storage files, and in some cases they want to protect themselves from unknowingly losing their data to a government agency that has subpoenaed the service provider.
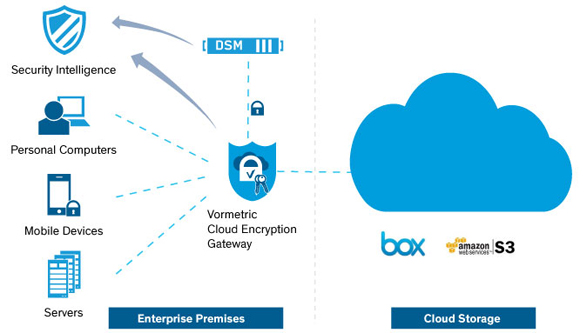
Now is the time. It has never been easier for IT organizations to offer secure and compliant cloud storage services to their organization. The new Vormetric Cloud Encryption Gateway is a virtual appliance that can be deployed in the cloud or on the customer premises. It is part of the Vormetric Data Security Platform, and therefore uses the same Vormetric Data Security Manager as used with other Vormetric products, to keep encryption keys secure and in IT’s control.
The solution encrypts sensitive data before it is saved to the cloud storage environment, enabling security teams to establish the visibility and control they need around sensitive assets. Offering support for Amazon S3 and Box environments initially, the solution is built on an extensible architecture that will enable Vormetric and its partners to support other SaaS and cloud storage environments in the future. To learn more about the solution, be sure to visit the Vormetric Cloud Encryption Gateway page.

 Charles Goldberg | VP, product marketing
Charles Goldberg | VP, product marketing