This year, with our 2015 Insider Threat Report, we've also been releasing extended information for target verticals and markets. Today we released the Healthcare results from the study, and earlier released financial and retail, cloud and big data and Japan and ASEAN results set. The release of the healthcare results seems especially timely with recent breaches from Anthem and Premera in mind.
ClickToTweet: Healthcare's most dangerous insider - Privileged Users(62%) @SocialTIS #2015InsiderThreat http://bit.ly/1OqSR44
Healthcare data has become one of the most desirable commodities for sale on ‘black market’ sites – and for good reason. Extensive healthcare data contains enough information to not just apply for credit cards or loans but it can compromise patients’ financial accounts and generate huge sums from fraudulent medical charges. As a result, healthcare data is at a premium, which does not bode well at time when data breaches are at an all-time high and organizations are still grasping how to handle these new and improved threats.
 The recent Anthem breach, which resulted from compromised IT administrator credentials, created an initial entry point that caused the breach and exposed 13.5 million patient records. Premera’s breach affected upwards of 78.4 million records after hackers accessed one of its databases.
The recent Anthem breach, which resulted from compromised IT administrator credentials, created an initial entry point that caused the breach and exposed 13.5 million patient records. Premera’s breach affected upwards of 78.4 million records after hackers accessed one of its databases.
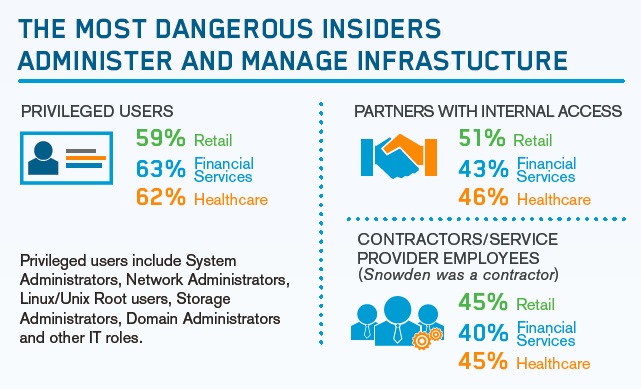
The most dangerous insiders
Not all insiders are the Snowdens of the world. Privileged users who act as operators and administrators have powerful access rights. Simply by having access, users may unwittingly put data at risk.
The big problem with privileged insiders? They traditionally have access to all resources available from systems that they manage and as a result, their credentials are a top target for hackers. In fact, privileged users were identified as the most dangerous insider threat, at 62 percent.
Slow and steady is not winning the race
Historically, healthcare has been slow to prioritize data protection. Patient care has always been the priority and while patient care has grown by leaps and bounds, security and protecting patients’ data hasn’t quite followed suit. The results point clearly to failure within healthcare organizations when it comes to protecting data. Among IT decision makers surveyed, 26 percent are protecting data because of a data-breach at an undefined time in the past. On one hand, we have an industry with huge amounts of sensitive data…on the other, we have an industry that has been slow on the IT security front.
A Step in the Right Direction
A number of compliance mandates are now required in healthcare to protect sensitive data. HIPPA, EPCS, PCI DSS and FDA… just to name a few. While compliance mandates must be met, complying with them is not enough to protect sensitive data today. Compliance requirements "evolve" slowly, while threats to data can change overnight. Years can pass between legislative and regulatory changes. As compliance no longer meets even baseline security requirements, as I said in my last blog (don’t worry – I won’t boom or clap), breaches are going on and on and on.
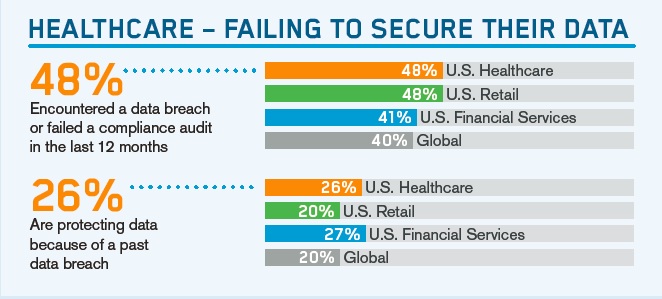 That's why it is a real problem that 48 percent of U.S. healthcare organizations reported either encountering a data breach or failing a compliance audit in the last year. It indicates that organizations in healthcare are not even passing the lowest bar for protection of their patient information.
That's why it is a real problem that 48 percent of U.S. healthcare organizations reported either encountering a data breach or failing a compliance audit in the last year. It indicates that organizations in healthcare are not even passing the lowest bar for protection of their patient information.
So let's shift some priorities
Respondents selected compliance requirements as the largest driver for securing sensitive data, at 54 percent. By focusing on compliance, organizations are paying less attention to larger threats that now need equal priority. According to our report, IT decision makers in healthcare feel their organizations are highly vulnerable. In fact, of those polled, 92 percent responded to being somewhat or more vulnerable, with nearly half (49 percent) being extremely or very vulnerable.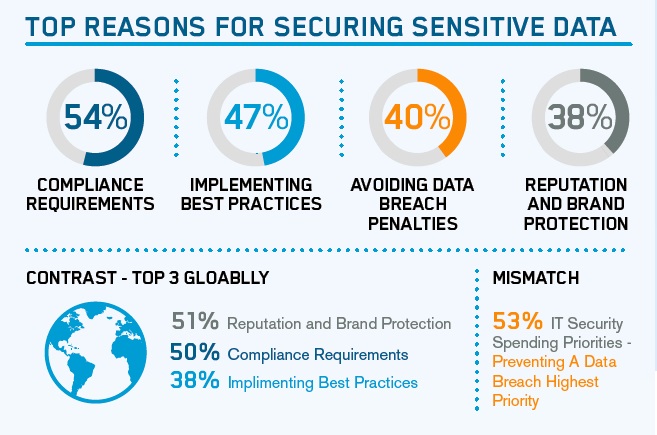
At Vormetric, we’ve developed the following tips for creating a data first strategy:
- With network and endpoint security solutions failing to stop or even detect attacks by employee insiders, and advanced attacks using employee credentials, a layered defense combining traditional as well as advanced data protection techniques is the path forward.
- Data protection initiatives need to concentrate on protecting data at the source. For most organizations, this will involve protecting a mix of on-premise databases and servers, and remote cloud and Big Data applications.
- Companies should integrate new encryption technology that minimizes operational impact and works with strong access controls for all important data sources.
- Implementing integrated data monitoring and technologies such as security information and event management (SIEM) systems to identify data usage and unusual and malicious access patterns is critical to maximizing security.
- To keep the whole organization safe, companies must develop an integrated data security strategy that includes monitoring, relevant access control and levels of data protection—and leaves security to the CISO, not the boardroom.
It’s time for change
Historically, healthcare has been slower to prioritize data protection and reasonably so – patient care has been the priority. Healthcare organizations are now required to not only prioritize the protection of physical health but personal data that can ultimately compromise financial and personal futures if exposed.
Encryption technology alongside strong access controls and key management is needed for all important data sources and includes the use of database or server, file, and data encryption, tokenization, data masking, and application encryption. By keeping healthcare data safe at the organization level, individuals can rest assured that when they go to bed at night, their most compromising information will not be exposed by those they trust to safeguard their physical well being.

 Tina Stewart | VP, Global Market Strategy
Tina Stewart | VP, Global Market Strategy