With more than 80 percent - the vast majority of enterprise businesses - now leveraging cloud environments, it’s no surprise that the infiltration of sensitive data into these environments is starting to turning heads. With that said, what can we do today to make both today's and tomorrow's use of cloud secure?
ClickToTweet: Top 5 Cloud Security Challenges facing the Cloud Adopting Enterprise @cjrad #DefenderOfData http://bit.ly/1aJjths
To explore the topic further, this week, the Cloud Security Alliance is hosting its annual summit prior to the RSA Conference 2015. Our very own Sol Cates will be on a panel from 9:45 -10:40 a.m. on Monday, April 20. The panel titled, “Top 5 Security Challenges Facing the Cloud Adopting Enterprise,” will feature several other CSA member companies providing commentary and deep expertise on the critical issues that face IT professionals today.
Since it seems appropriate, we decided to further expand on our point of view when it comes to the five challenges being discussed at the summit:
1: Data Security
Our recent Insider Threat Report – Cloud/Big Data edition featured survey results indicating the locations of where the largest volumes of sensitive data are stored:
- Databases (49%)
- File servers (39%)
- Cloud service environments (36%)
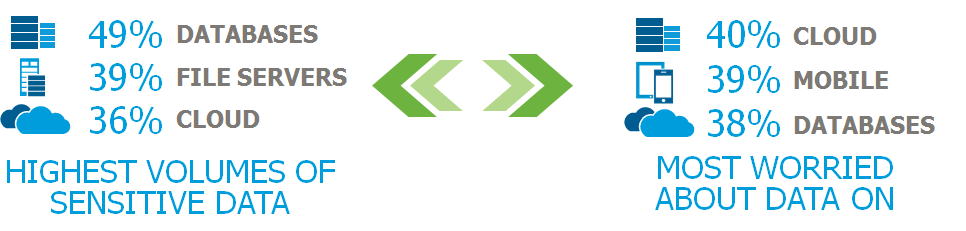 Cloud trails closely behind databases and file servers as a top location for the storage of sensitive data. Much of that data is sensitive, regulated or legally controlled information. Needless to say, a lot has changed in the past few years.
Cloud trails closely behind databases and file servers as a top location for the storage of sensitive data. Much of that data is sensitive, regulated or legally controlled information. Needless to say, a lot has changed in the past few years.
Ensuring that data is secure when deploying a cloud environment can be a daunting task. Naturally, as the adoption of cloud resources continues to grow, the risk of data breaches grows with it. The fear of a new data breach is so high, that preventing them tops the list as the number one spending priority, trumping compliance in our survey for the first time.
But, there are common sense strategies for protecting data. Implementing and designing a proper cloud security database structure can help mitigate the risk. This includes protecting data at the file level or application level through transparent and application level encryption. Additional methods of encryption can involve tokenization and dynamic data masking. In his latest blog, Vormetric’s CEO Alan Kessler breaks down the “when” and “why” behind these approaches.
2: Navigating Global Trust Issues
We think it’s fair to say the Edward Snowden/NSA revelations have seriously impacted global trust levels. An increasing number of enterprises (and their governments) are unwilling to put their data in the hands of U.S.-based cloud service providers (CSPs). This anxiety has manifested itself on the policy level; for example, many data-and-privacy-focused countries, such as Germany and Japan, have tightened up their data residency requirements even further.
For CSPs to increase their footprint in the enterprise, they must address enterprise requirements around security, data protection and data management. More specifically, CSPs need to provide better protection and visibility to their customers.
One company taking a proactive approach to assuaging customer fears is Amazon. In October of 2014, Amazon AWS announced it would open new data centers in Germany to ensure compliance with both EU and German privacy laws. In theory, this will allow German AWS customers to keep their data physically inside Germany and in compliance with German law.
3: Shadow IT
Businesses are evolving quickly and, via shadow IT, internal business units and operating groups are often bypassing IT and IT security controls altogether in order to get things done. While this might speed things up, it can open the door for security vulnerabilities that are expensive to fix. Keeping stock of, and tamping down on, shadow IT endeavors is vital, especially when it comes to the cloud.
One of the best ways to prevent against leakage of sensitive data due to shadow IT is to a) encrypt data and b) implement an intelligent key management model. Key management basically allows for access control, which means limiting access to encrypted data to only those whose work requires it.
When it comes to key management, there’s basically two models to consider for encrypted data. Either the enterprise owns and manages the key, or allows the CSP to own and manage the key on its behalf. Each model has its own risks, so the final decision should depend on the level of risk and cost the enterprise is prepared to take on. As a best practice, as the owner of the data, we recommend enterprises own and manage their own keys.
Vormetric Cloud Encryption, for example, includes encryption key management within the solution and is completely transparent to applications and users. This allows for existing processes and usage to continue with no changes. Thus, enterprises can protect any data file within cloud environments simply, easily and efficiently.
4: Advanced Attacks & Cyber Conflicts
In 2014, I predicted there would be a major cloud or SaaS provider data breach in 2015. Threat actors are gaining in sophistication, and attacks are becoming more complex. While we can’t predict the future, we can take steps to prevent cybersecurity attacks and create a safer environment.
In our opinion, the best way to do this is to encrypt, encrypt, encrypt. As Alan noted back in October, very people at very smart companies have come to the conclusion that encrypting a vast majority of their data is one of the best things they can do to reduce risk and assuage customer fears. While no company or CEO wants to discuss a data breach, having a broad-based strategy to make data protection a priority plays well from both a security and marketing perspective.
5: Service Provider Visibility & Translating Enterprise Requirements into the Cloud
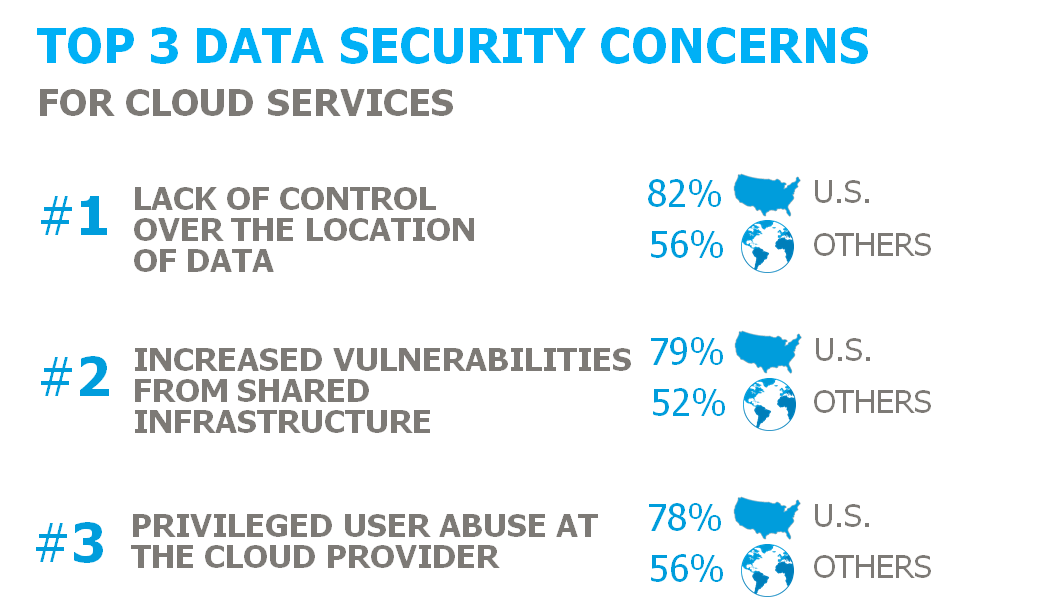
Nurturing a safe, compliant environment is an ongoing concern, particularly as business continue to expand their global networks. According to our 2015 Insider Threat Report – Cloud/Big Data edition, enterprise clients say that adoption levels would be even higher and involve more key enterprise applications if the service providers did more to assail their fears on security, data protection, and data management issues. Specifically, the top three concerns about data safety for cloud services include:
- Lack of control of the location for data (69% globally)
- Privileged user abuse at the cloud provider (67% globally)
- Vulnerabilities from shared infrastructure (66% globally
 This is an issue that CSPs have to come to terms with. Some are better placed than others, but as an industry the position is very mixed. Some providers are already promoting their “baked in” security protection and management services. Others are still dabbling while building their strategies and are not ready to address the major security and data protection issues that worry the enterprise.
This is an issue that CSPs have to come to terms with. Some are better placed than others, but as an industry the position is very mixed. Some providers are already promoting their “baked in” security protection and management services. Others are still dabbling while building their strategies and are not ready to address the major security and data protection issues that worry the enterprise.
When courting enterprise business, CPS should have their security stance front and center. Even if they have met the enterprise bar for compliance, their offerings need to take into account that much wider data sets than just compliance data now need protecting. With the threat level as high as it is today, it’s only a matter of time before CSPs will be requested and required to meet security needs to continue doing business to earn enterprise's business.
Conclusion
As this blog makes clear, improving cloud security is not impossible. For more on this topic, come visit us at RSA booth No. 515 (South Hall) to participate in some exciting giveaways and check out Vormetric’s Cloud Encryption Gateway.
Defending your data in the cloud with Vormetric? Have a different perspective on 2015 cloud security? Let us know if you have any feedback. I can be reached at cradford@vormetric.com or twitter @cjrad.
