The access management market has been more relevant this year than ever before. The new normal of remote working brought on by the pandemic has demonstrated the clear need for organizations to be able to deliver secure access to both cloud and on-premises enterprise applications for their remote workforces. This need was already being driven by the increased use of cloud services, but the pandemic put a spotlight on how critical access management services are for the ability of businesses to continue to operate.
Gartner estimates that the access management market will be $4.42 billion by 2021 according to its last Information Security forecast report. Given the growing use and importance of access management services, here are six key principles to consider when choosing the right access management solution.
1. Opt for SaaS-delivered Access Management
SaaS-delivered access management is becoming the predominantly delivery model. In fact, according to the Gartner Magic Quadrant for Access Management, “90% or more of clients based in North America and approximately 65% in Europe and the Asia/Pacific region countries are also seeking SaaS-delivered models for new AM purchases.” The advantages of a cloud-based access management are very clear: agility, quicker access to new features, elimination of ongoing software upgrades, and the reduction of infrastructure that is need to be supported. And the list goes on.
2. Go for a Solution that Addresses Your Use Cases
Your organization likely has unique needs, especially if you are expanding your cloud footprint to address very specific use cases and expand access security to additional apps in a phased approach. In this regards, Gartner states in its recently released Magic Quadrant for Access Management that “by 2024, 30% of all new purchasing for AM solutions will be ‘best fit,’ as opposed to “best in class.” Just because an access management vendor can support B2C, B2C and a wide range of other use cases doesn’t necessarily mean it is the right solution for your organization. By implementing an integrated access management, single sign on and authentication solution that addresses the specific needs of enterprise use cases, organizations can reduce the inefficiencies, administrative overheads, elevated risk and higher costs that result from having to manage multiple access security silos.
3. Not Everyone Needs the Same Level of Authentication
According to the Verizon 2020 Data Breach Investigations Report, cloud migration, remote working and complex security systems were the most dominant contributing factors to increasing the cost of a data breach. At the same time, the leading cause of breaches are compromised credentials. In this high-risk security climate, it’s imperative that organizations go beyond merely checking boxes. Not all security solutions are created equal and this is doubly true of access management and authentication solutions.
Authentication is key to security. The depth and breadth of authentication methods, form factors and technologies offered by an access management service play a key role in providing the right level of protection for the right user for any given enterprise application. Admins and privileged users need more stringent methods of authentication than other users. C-level users need strong protection but demand mobility and convenience, but not all users can use mobile apps. In general - the majority of users will find work arounds if logging onto dozens of apps daily is too burdensome. Only by combining different authentication methods and technologies and enforcing them consistently through access policies, can organizations achieve security, while still offering a convenient familiar logon experience to their users.
Zero Trust security offers a blueprint for cloud transformation. The need to support secure anytime-anywhere access for users has accelerated cloud adoption, while exposing the weaknesses of perimeter security. The notion of being able to verify people at a single point of entry to the enterprise data center doesn’t line up with the fact that more and more applications are no longer delivered from the data center. Zero trust security concepts offer the most effective blueprint for securing data in distributed, dispersed environments.
4. Separate Access Management and Authentication from Your Cloud Services Provider
Expanding privacy regulations and high profile breaches underscore how important it is to implement an agnostic dedicated access management and authentication solution that segregates security from the service provider. This is all the more relevant in multi-cloud environments where according to the Cloud Security Alliance “variations in ownership introduce complexity and risk” and where an organization’s “overall security posture is defined by its weakest link”. In its shared security model between customers and cloud service providers, the Cloud Security Alliance clearly states that Identity and Access Management ownership and control sits squarely with the customer, not the cloud service provider. The best way to ensure you have control over your identities, is to adopt a “bring your own access security” policy. By doing so, you’ll reduce risk and ensure seamless and agnostic access to multiple cloud services.
5. Simplicity is Key, So Make It Easy for End Users
Users access dozens of on-premises and cloud apps on a daily basis. Easing the login burden by eliminating passwords and repetitive authentications is therefore key to increasing productivity, reducing log outs and cutting help desk calls.
6. Insist on Getting the Best TCO
COVID-19 has rapidly accelerated digital transformation initiatives, forcing enterprises to speed up strategic projects that enable secure remote access and cloud adoption. At the same time, budget pressures are high and rising as a result of the pandemic. According to a recent survey of CFOs conducted by Gartner, “Many CFOs are seeking to revive stalled growth investments while optimizing costs to better reflect new business realities. Chief among these realities are meeting new customer preferences shaped by the pandemic, including greater expectancy for speed, multichannel delivery and always-on availability.”
Selecting an access management service that supports your key business initiatives while offering superior value is critical for business viability. That is why it important to strongly consider access management solutions that offer all-inclusive pricing with transparent licensing. This includes single sign on, conditional access, free hardware tokens, unlimited software tokens, and a broad range of authentication methods and technologies, such as multi-factor, adaptive and pattern-based authentication.
Gartner recently released its Magic Quadrant for Access Management (Nov 2020) and SafeNet Trusted Access, Thales’s cloud-based access management solution, is included in the report. For more than 25 years, Thales has been a leading provider of access management and authentication services for many of the most recognized and trusted brands in the world. Offering flexible policy controls, powerful adaptive and multi-factor authentication capabilities and Smart Single-Sign-On, SafeNet Trusted Access protects applications in the cloud while ensuring a convenient and familiar logon experience for your users.
You can find more than 120 customer reviews of SafeNet Trusted Access on Gartner Peer Insights from IT security professionals in a wide range of industries from all over the world. Below are just some of the customer reviews:
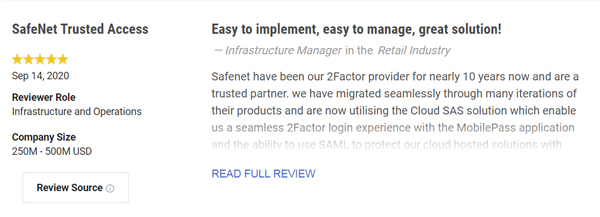
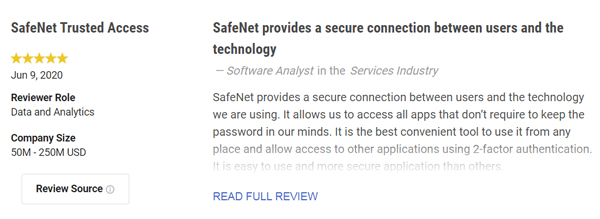
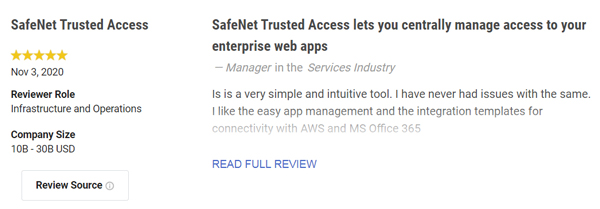
Whether you have already deployed or are planning to deploy, read more about SafeNet Trusted Access.

 Danna Bethlehem | Director, Product Marketing
Danna Bethlehem | Director, Product Marketing