 Gabby Ortiz | Product Marketing Manager
More About This Author >
Gabby Ortiz | Product Marketing Manager
More About This Author >
 Gabby Ortiz | Product Marketing Manager
More About This Author >
Gabby Ortiz | Product Marketing Manager
More About This Author >
TL;DR
- The United States can now access any and all foreign data entering or residing within their borders without a warrant
- These recent policy adjustments are contradictory to global data protection regulations like GDPR
- Organizations outside the U.S. are now having to reevaluate their cloud and identity infrastructure solutions, many of which are subject to new U.S. laws—instead, opting for local alternatives
- Thales makes digital sovereignty a thing again; by helping you assert control over your data, securing every identity across the entire digital journey
If you’ve so much as glanced at any news reporting lately, you’ve probably seen sweeping policy shifts, particularly emerging from the United States. These changes are impacting many different areas of our lives and how we do business, but also how we think about and approach regulatory compliance and digital sovereignty. Rising geopolitical tensions and new legislation have really shaken things up, especially for global security organizations, as they navigate now even stricter regulatory waters.
While regulations are always being updated and adjusted, which can be extremely challenging to keep up with as it is—this is really nothing new for security and GRC teams. However, recent legislation has these teams going back to the drawing board altogether. New legislation has led to a series of regulatory changes that not-so-clearly dictate how they should approach digital sovereignty going forward and what that means for their global identity and access management (IAM) strategies.
Before we dive in, we have an upcoming webinar where our VP of Workforce IAM, Guido Gerrits, goes even deeper on the topic with more insights and expert recommendations for traversing this complex set of circumstances.
What is digital sovereignty?
According to the World Economic Forum, digital sovereignty refers to the ability to have control over your own digital destiny—the data, hardware, and software that you rely on and create.
Establishing true digital sovereignty is already a massive feat, but maintaining it is harder than ever now that virtually every organization has data being accessed and moved across cloud environments, and regulations are constantly fluctuating claiming rights to your data and digital assets.
Recent regulatory shifts raise questions
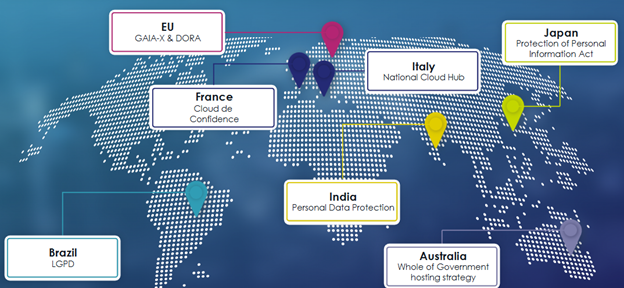
The complex web of global and local regulations just got more complex as the U.S. has rolled out significant changes to FISA 702 and the CLOUD Act —both of which have attracted a lot of attention from organizations, particularly those residing outside of the U.S.
Why, you ask? Let’s break down what these White House-driven adjustments could mean for you.
Foreign Intelligence Surveillance Act (FISA) 702 and Clarifying Lawful Overseas Use of Data (CLOUD) Act in detail
FISA 702
FISA Section 702 now authorizes U.S. intelligence agencies to collect communications of non-U.S. persons located outside the United States, without a warrant, for the purpose of foreign intelligence gathering.
This can impact many things since the U.S. is home to a lot of large cloud communications platforms—like Google, Microsoft, Meta, and the list goes on. But what I want to call attention to in this blog, is how this actually impacts identity infrastructure—because a lot of those types of solutions reside in the U.S., too, and are widely adopted across the globe.
According to these new FISA developments, if a company uses an IAM solution operated by a U.S.-based company, or a foreign company with a U.S. presence, the U.S. government can compel access to data about non-U.S. persons.
This could include:
- Usernames and passwords
- Authentication logs
- Biometric data
- Access patterns (what users accessed, when, and from where)
- Roles and privileges across enterprise apps
CLOUD Act
The CLOUD Act allows U.S. law enforcement agencies to demand access to data held by U.S.-based technology companies, regardless of where that data is physically stored in the world.
If your organization uses a U.S.-based IAM vendor, identity and access data for non-U.S. employees or customers can be 1) requested by U.S. authorities under the CLOUD Act, 2) accessed without notifying the data subject or foreign regulator, and 3) contradicts GDPR, PIPEDA (Canada), and other global data sovereignty laws.
How FISA 702 and the CLOUD Act contradict General Data Protection Regulation (GDPR) and other global regulations
GDPR and similar laws require personal data to be adequately protected and not to be transferred across borders whatsoever. This was already something difficult to accomplish once everything moved to the cloud. Now, almost every organization uses cloud applications—let's use Workday as an example—that contain copious amounts of personally identifiable information (PII) like social security numbers, banking information, residential addresses, etc. and even protected health information (PHI) like medical records, benefits, and more.
Under GDPR, individuals have the right to contest any misuse of their data. However, non-U.S. persons have no standing in U.S. courts, and they have no way to request their data be collected or removed, should their data be accessed within the U.S.
Before the adjustments to FISA 702 and the CLOUD Act, to move data from the EU to the U.S., organizations had to issue Standard Contractual Clauses (SCCs) as well as Transfer Impact Assessments (TIAs) to make sure said data was well-protected and individuals kept ownership and rights over their own data.
However, all of this has been thrown out the window because U.S. vendors can no longer resist governmental data access, even if this data doesn’t reside within the U.S.—putting security teams under legal uncertainty.
How security organizations are moving forward
So much has changed in the realm of security and compliance in the past decade already, but this clash of compliance frameworks has created a legal minefield that organizations must now navigate with greater diligence than ever before.
Organizations outside of the United States are reevaluating the cloud solutions they rely on and instead, considering non-U.S. alternatives for identity infrastructure to legally separate themselves from being subject to U.S. data laws.
Reestablish Complete Digital Sovereignty with Thales
Thales helps security teams assert control over their digital identities—wherever they do business—while minimizing exposure to geopolitical risks and cross-border regulatory friction. Our IAM solutions secure every identity interaction from your own employees to third parties that engage with your systems and access your data, both in the cloud and on-prem.
With a wide range of authentication methods and even passwordless login capabilities, your organization can achieve the highest MFA adoption rates in the industry—a principle now heavily enforced by residency laws and local regulations—without any added user friction.
Not only does Thales protect every identity—we secure the entire digital journey. From the moment a user signs up, we verify their identity, then ensure secure and continuous access through phishing-resistant MFA and single sign-on (SSO). Thales takes a highly context-aware approach with adaptive and fine-grained authorization, delegation, and relationship management. And when access is no longer needed, we support seamless and secure account deletion to close the loop on any potential vulnerabilities.
A named leader in passwordless authentication for enterprises by KuppingerCole and recognized in the Best of Cybersecurity Awards as a top solution in IAM by Expert Insights, Thales continues to serve more than 35,000 customers worldwide by being their trusted partner in navigating these complex geopolitical circumstances.
To learn more, take a closer look our complete IAM portfolio or skip ahead and request a personalized demonstration.