 Gregory Vigroux | Senior Product Manager
More About This Author >
Gregory Vigroux | Senior Product Manager
More About This Author >
 Gregory Vigroux | Senior Product Manager
More About This Author >
Gregory Vigroux | Senior Product Manager
More About This Author >
Initially designed for the consumer market, the FIDO (Fast IDentity Online) standard aims to replace passwords with more secure authentication methods for online services. While recent versions, like FIDO2.1, have begun to address enterprise needs, significant gaps remain that organizations must address to simplify, accelerate, and secure their deployment.
Enterprises face unique challenges compared to consumers when deploying FIDO security keys. For instance, they must secure a range of digital resources, from legacy systems to modern cloud applications. Also, employees use an array of computing devices, further complicating the integration of FIDO keys.
In addition, the sheer number of users in an enterprise makes the deployment and management of FIDO keys complex. Finally, enterprises must adhere to stringent security and data privacy regulations, which FIDO standards must support.
Challenges Businesses Face When Deploying FIDO Keys
There are several challenges IT security professionals in large organizations face when deploying FIDO keys regarding user experience, administrative overheads, and security. These include:
User Experience and Education
- The Learning Curve: Transitioning from traditional passwords to FIDO keys requires users to adapt to a new authentication method. This shift necessitates a significant change in behavior and understanding, as users need to learn how to handle and use FIDO keys effectively. Any unfamiliarity with this new technology can lead to confusion and frustration, especially for those who are not tech-savvy.
- Initial Setup: Self-registering Enterprise Identity Provider (IDP) keys can be particularly complex for non-technical users. The process often requires substantial IT support to guide users through the initial setup and can become cumbersome in large companies, particularly when identity verification relies on email OTPs. This method can be challenging for newcomers who do not have access to company email addresses, complicating the registration process further and potentially delaying the deployment of FIDO keys.
- Blocked Keys: If users forget their PIN, the only solution is to fully reset and re-register the key, which adds to the overall complexity and inconvenience. This additional step can be particularly arduous, as users must go through the registration process again, often needing further IT help to finish the task.
Administrative Overhead
Assisting users who misuse FIDO keys through loss, forgotten PINs, or accidental resets creates substantial administrative overhead. Each incident requires intervention from IT support, which can be time-consuming and resource heavy. This burden is amplified in large enterprises with multiple users and devices, as the volume of support requests can quickly escalate. Managing these issues on a large scale involves resolving individual problems and implementing processes and policies to prevent them, further adding to the administrative burden.
Security Holes
Weak Initial Authentication: Relying on less secure methods such as username/password combinations or SMS one-time passwords (OTPs) for FIDO authenticator registration exposes the system to phishing attacks, account takeovers, and fraudulent activities. These vulnerabilities can undermine the security benefits of FIDO authentication from the start.
PIN Length: The FIDO 2.0 standard allows users to set PINs with 4 digits which do not meet the high-security assurance levels many organizations require, especially in regulated markets. Although FIDO 2.1 introduces the ability to enforce minimum PIN length settings and increase to 6 digits or more, organizations must ensure that these settings cannot be bypassed during key resets. Proper enforcement of PIN length is crucial to maintaining strong security.
Lack of 2FA: Certain online services may not always prompt users to provide their PIN or biometric data during authentication, reducing overall security. IT security professionals must regularly audit these authentication processes and enforce two-factor authentication (2FA) wherever necessary to ensure robust protection.
Lost/Stolen Keys: Firms must establish a clear and efficient process for revoking lost or stolen FIDO keys to prevent unauthorized access. This includes having protocols for users to report lost keys and for administrators to swiftly deactivate them, helping to mitigate the risk of security breaches.
How to Overcome the Challenges
When implementing FIDO security keys within an enterprise, it is crucial to not only focus on the authentication step, but to strengthen each step of the lifecycle, from FIDO Key activation to revocation.
CISO’s and IT security professionals have two options:
1. Benefit from FIDO 2.1 standard (i.e., CTAP2.1 Enterprises standard capabilities) and enforce standard features such as PIN change at first use, enforce user verification or minimum PIN length.
- Minimum PIN Length: Enterprises can define a minimum PIN length during the setup phase. This practice strengthens security policies and ensures compliance with regulatory standards.
- Enforce User Verification: Through this feature, user verification is enforced directly in the FIDO key to ensure that users are required to register their PIN or biometric regardless of the authentication context. This eliminates the risk of lost or stolen keys being used by unauthorized individuals.
- PIN change at first use: This feature enforces end-users to define their own PIN before using the key, improving by this way the security and usability of the user verification step.
To accomplish that, they need to equip their end users with FIDO keys supporting FIDO2.1 and fully certified by FIDO Alliance, such as the new SafeNet Token Fusion NFC PIV, provided by Thales.
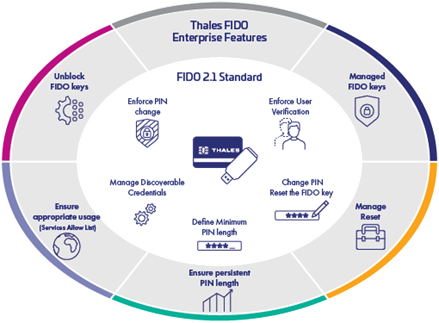
2. Go beyond FIDO 2.1 standard and benefit from Thales unique FIDO enterprise features, in addition to FIDO2.1 standard features
- Managed Mode: Ensure IT operator is the only personnel to manage sensitive operations on the keys such as setting security policies, tracking usage, unblocking or revoking FIDO keys. Centralized management of FIDO keys enables entities to control the keys' lifecycle and reduce gaps that could transform into authentication risks.
- Configure Services Allow List: Limit the usage of organization-managed FIDO keys to authorized services only. This practice ensures that keys are not used for personal purposes, maintaining security and compliance.
- Ensure Persistent PIN Length: Prevents end users from changing the minimum PIN length defined by the IT operator.
- Unblock FIDO Keys: Enables IT operator to unblock FIDO keys after several failed attempts, reducing the need for users to reset their keys entirely, saving time, and reducing administrative overhead.
- Manage Reset: Protect valuable user information stored in the FIDO key from unintentional deletion. It also prevents users from fully resetting their keys by mistake, preserving the integrity of the authentication process.
In this option, organizations need to equip their end users with Thales FIDO keys in the Enterprise Edition, such as SafeNet eToken Fusion NFC PIV Enterprise, that support FIDO 2.1 Standard and Thales FIDO Enterprise Features.
Thales FIDO Enterprise features
Accelerate and Secure FIDO Keys Deployment with a Centralized Lifecycle Management
Centralized FIDO key management enables organizations to control the key lifecycle and reduce gaps that could turn into security risks or low end-user adoption. Thales innovates in FIDO key management with robust enterprise features that are unique to the market.
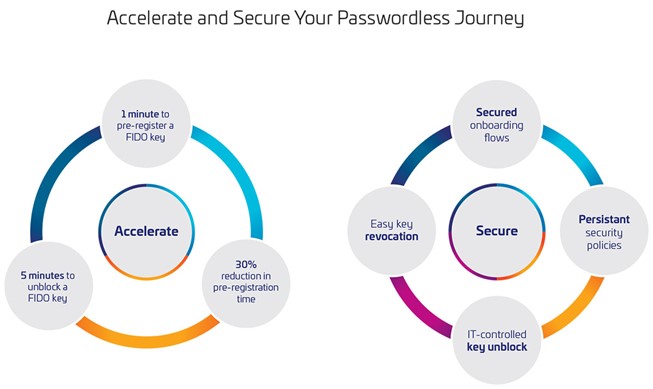
Thales end-to-end solution, that combines an interoperable management platform with Thales FIDO security keys specifically designed for use in large organizations, helps Enterprises accelerate and secure their passwordless journey:
- Provide secure and seamless authentication to their users from day one by pre-registering FIDO keys on behalf of their users and configuring security policies in less than a minute.
- Manage FIDO keys easily and securely at each step of their lifecycle, from onboarding to revocation.
Want to know more? Watch our joint webinar “The Secret to Scalable FIDO Success” together with experts from Microsoft and Versasec now.