 Gregory Vigroux | Senior Product Manager
More About This Author >
Gregory Vigroux | Senior Product Manager
More About This Author >
 Gregory Vigroux | Senior Product Manager
More About This Author >
Gregory Vigroux | Senior Product Manager
More About This Author >
With sensitive data and apps dispersed across fragmented computing environments, multi-factor authentication (MFA) has emerged as the best way to authenticate and protect our digital identities in the zero-trust security framework. However, not all authentication methods are equally safe when facing complex cyberattacks. Deploying FIDO (Fast Identity Online) security keys within a business offers substantial benefits, such as improved security through phishing-resistant, passwordless authentication.
Unpacking FIDO Deployment Challenges
With FIDO security keys gaining traction (over 2 billion passkeys are in use globally as of 2025), effectively managing those hardware keys becomes essential to unlock their full potential. However, sometimes, this is easier said than done.
Managing the Security Key Lifecycle
Issuance is merely the beginning of the FIDO authenticator's lifecycle, which needs to be adequately examined. All phases of the authenticator's lifespan, including temporary disablement, revocation, and replacement, must be monitored, controlled, and guarded.
When FIDO authenticators are mismanaged, the following consequences may occur:
- You risk being a victim of fraud, phishing, and account takeover if you employ less secure authentication techniques for the FIDO authenticator, like username/password or SMS OTP.
- If the enrollment procedure is unclear or challenging to finish, users will become frustrated and lose productivity, decreasing user adoption and increasing the load on the helpdesk.
- Violations of security guidelines or legal requirements, if protected resources are accessed by unauthorized users or the enrollment procedure, is not accurately documented.
- If there is no control over the type of FIDO authenticator utilized, the use of an invalid, less secure, or even hazardous authenticator could occur accidentally or on purpose.
Having an MFA that is resistant to phishing attacks is insufficient; you also need to ensure that your management procedures are secure, reusable, and traceable.
FIDO Integration
Integrating FIDO authentication with existing IT infrastructure and non-FIDO-compliant applications poses another challenge. Organizations often have a hybrid IT environment with multiple Identity Providers (IDPs) and applications that must work seamlessly with FIDO keys. Ensuring compatibility and smooth operation across these systems requires careful planning and configuration.
The Need for FIDO Key Lifecycle Management
Effective FIDO key lifecycle management is critical for secure and efficient authentication. Businesses must define their deployment strategy, whether it involves user self-service or centralized control, and ensure they have mechanisms to handle lost or forgotten keys. Thales provides tailored solutions to meet the needs of organizations adopting either approach, ensuring secure and streamlined FIDO key management.
By addressing these challenges and leveraging Thales' solutions, organizations can successfully deploy FIDO authentication, bolster their security posture, and provide a seamless user experience.
Source: Page 23 of Passwordless 360°: Protecting Your Business, Empowering Your Users
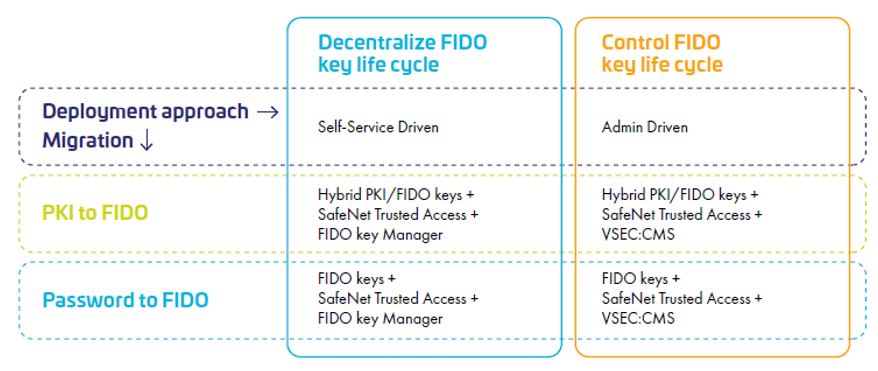
Centralized vs. Decentralized Approaches
Deciding between a centralized and decentralized deployment approach is critical. Centralized deployment, managed by IT administrators, offers higher security and control but requires sufficient IT resources. On the other hand, decentralized deployment, where users manage their keys, allows room for flexibility but can take more work to oversee and secure uniformly. Let’s take a closer look:
The Decentralized Approach
In a decentralized setup, users are responsible for managing their own FIDO keys. This method suits smaller entities, remote workers, or those with limited IT resources. Users buy their security keys, set up a PIN, activate the key, and handle any unblocking if needed. This approach offers greater flexibility and reduces the administrative burden on IT departments, but it can quickly lead to a lack of visibility as more employees use FIDO security keys.
The Centralized Approach
A centralized deployment is managed by IT administrators and is ideal for larger enterprises. This approach ensures higher security through phishing-resistant authentication, controlled distribution, and the ability to unblock or replace keys if users forget or lose them. Centralized management provides a cohesive security policy across the organization and simplifies the administration of FIDO keys on a large scale.
Thales Solutions for FIDO Deployment
To address the complexities of FIDO deployment, Thales offers comprehensive solutions tailored to meet the diverse needs of organizations.
SafeNet FIDO Key Manager
Thales SafeNet FIDO Key Manager is a standalone application that helps end users manage, configure, and set up or change PINs on their Thales FIDO security keys. This solution supports a decentralized approach, empowering users to handle their own FIDO key setup and administrators to manage what end users are authorized to configure management.
For larger organizations seeking greater control and scalability, Thales developed the Enterprise Edition with dedicated management tools designed specifically for complex enterprise environments. Together, they deliver advanced capabilities that simplify deployment, enhance security governance, and make passwordless authentication easier to manage at scale.
- Centralized key management and policy enforcement
- Streamlined onboarding and PIN reset processes
- Enhanced visibility and control for IT teams
- Enterprise-grade features built for high-security environments

OneWelcome FIDO Key Lifecycle Management solution
Thales OneWelcome FIDO Key Lifecycle Management simplifies the deployment and administration of FIDO security keys at scale by removing traditional barriers to passwordless adoption. By giving IT teams full control over the entire key lifecycle - from preregistration to revocation - this solution reduces user frustration and IT overhead, accelerates secure passwordless rollouts, and boosts end-user productivity. Integrated with Microsoft Entra ID, it enables seamless, secure authentication from day one.
SafeNet Trusted Access and Versasec Credential Management System
Previously, highly regulated sectors relied on Public Key Infrastructure (PKI) for certificate-based authentication, qualified digital signatures, and secure file encryption. While effective against phishing, they struggled to apply PKI-based authentication to modern cloud and web applications, particularly from mobile devices that are now widely used. FIDO is increasingly favored for its interoperability and simplicity, as it offers a future-proof alternative that circumvents complex IT infrastructure requirements.
Issuance Options
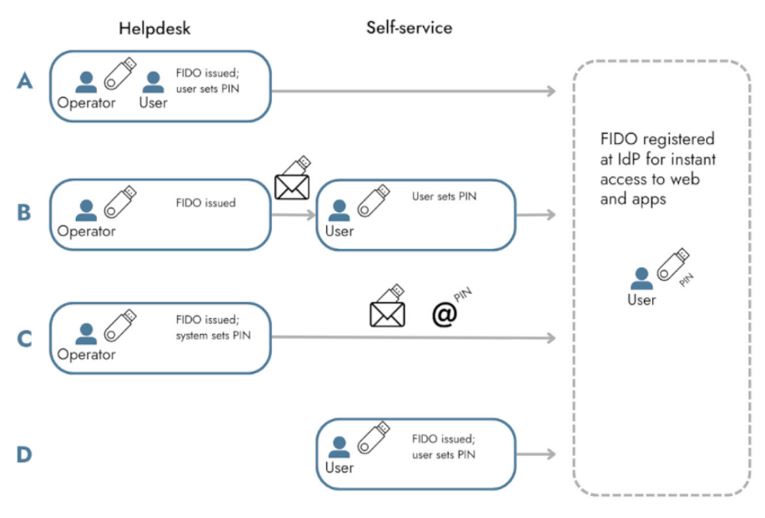
For entities migrating from PKI to FIDO and who want to control the FIDO key life cycle in the same way they manage their PKI credentials, SafeNet Trusted Access combined with Versasec CMS allows them to let IT administrators control the FIDO key enrollment and secure access to their web apps in no time. This solution enables IT administrators to manage FIDO key enrollment, define security rules, and automate key management processes. STA and Versasec CMS ensure secure access to web applications and provide a scalable solution for managing FIDO keys in large organizations.
With so many use cases for FIDO keys, effectively managing their lifecycle becomes both a business and a security necessity. But rest assured, we have the answer to your concerns about FIDO authenticator management. Read our dedicated solution brief, to learn more.