There is a growing momentum around Self-Sovereign Identities (SSI) with real value to be captured by individuals, countries, and businesses. When privacy is at stake, SSI puts individuals back in control of their personal data. Moreover, it helps organizations to operate in an environment they trust and control to significantly reduce Know Your Customer (KYC) and GDPR costs and to more easily comply with regional privacy rules while improving user experience.
Identity is evolving in the changing global business environment
Although privacy regulations are constantly changing, businesses are still responsible for protecting employee and customer information. Doing so is much easier said than done. Organizations have an average of 17 apps to process or store customer data, and ensuring compliance across each of those apps is a complex task. If you also consider that the US hosts 92% of the western world's data and the laws there often conflict with European regulations, the data protection task at hand compounds in complexity exponentially.
The most crucial concern is that a small number of large technology companies control massive amounts of data about their users. And with so many users and so much information, the policies and actions of this small number of large tech companies can have a significant influence.
So, these privacy concerns gave birth to the concept of digital sovereignty, defined by The World Economic Forum as “the ability to have control over your own digital destiny – the data, hardware and software that you rely on and create.”
Digital sovereignty includes two key pillars: data sovereignty and technological sovereignty.
- Data sovereignty refers to a company’s control over its data.
- Technological sovereignty is a company or nation's control over the digital technologies it uses.
In a highly decentralized ecosystem, digital identities have emerged as a crucial component of digital sovereignty because they are the only true means of security and access control. However, traditional approaches to digital identities and managing digital user journeys create many challenges for both individuals and organizations, including:
- Poor customer experience and registration fatigue
- Lack of control over data privacy
- Higher probability of identity theft and, consequently, data breach
- Higher abandonment and churn rates
- Inaccurate and stale data about business customers
To address these challenges, the concept of Self-Sovereign Identities has emerged.
What are Self-Sovereign Identities?
Self-sovereign identity (SSI) is an architecture for managing digital identities where individuals or organizations have full ownership and control over their identities and personal data. Individuals with self-sovereign identities can store their data on their devices and selectively share it with third parties that they want to interact with, in a peer-to-peer manner. In this type of information exchange, there is no centralized repository or owner of the data. And there is no intermediary in the middle of the exchange that can keep track of who is accessing what service.
In contrast to centralized identity management, people are the boss of their own digital identities and decide who has access to their data. They can also revoke that access at any time.
The concept of decentralized digital identities, where people maintain sovereignty over their data, presents several advantages, including:
- Higher level of security
- Individuals are in control of their privacy
- Enhanced customer experience
- Inclusiveness
How does SSI work?
There are three main participants in the SSI workflow:
- The holder is the individual or the organization that owns the digital identity and specific information or attributes; this information is stored in the form of Verifiable Credentials in a digital wallet app.
- The issuer is the authority that issues the Verifiable Credentials.
- The verifier is the party checking the credential. The verifier can be another organization (i.e., a bank), a retailer, or an individual’s employer.
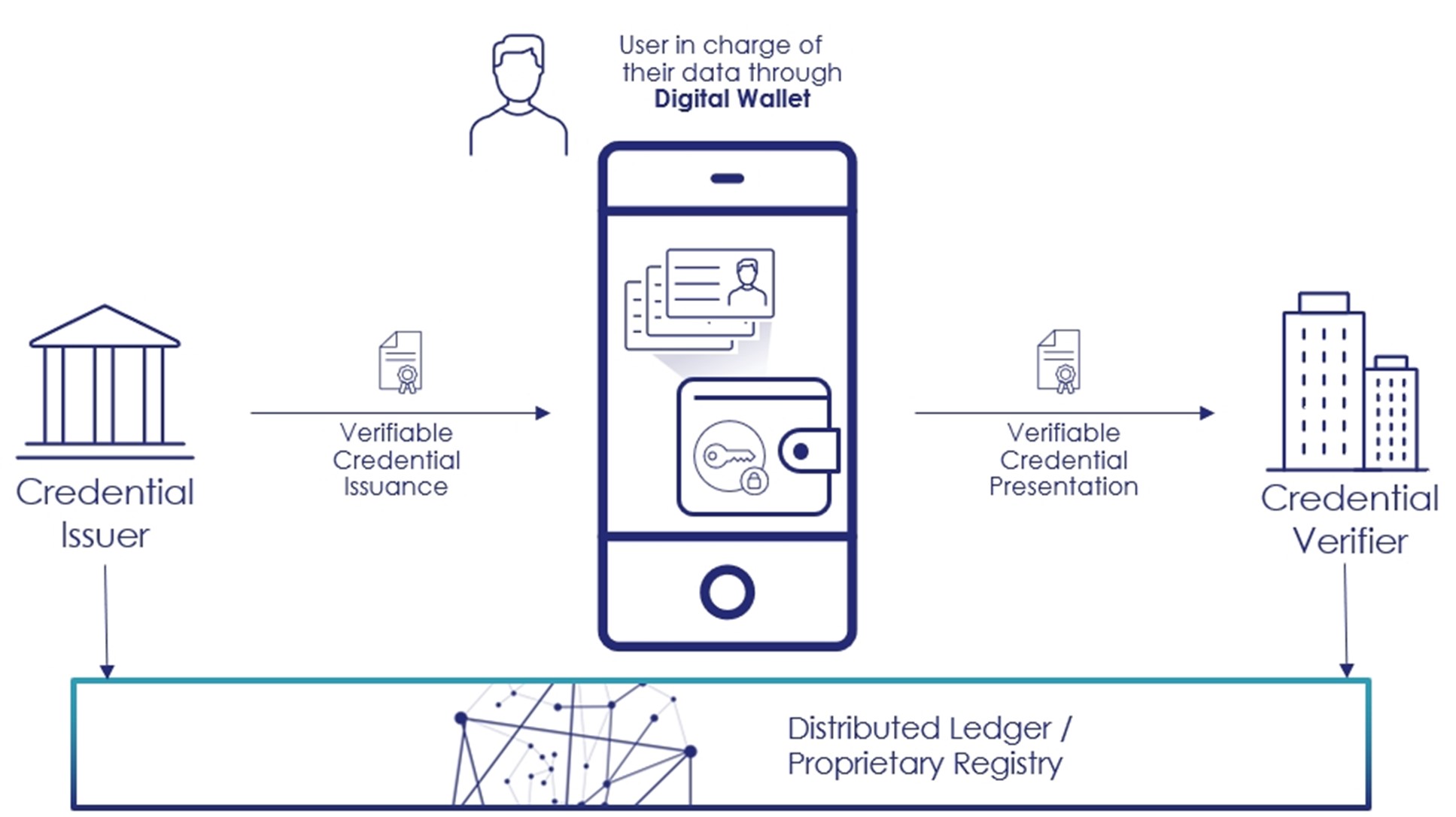
At the heart of the SSI architecture is a digital wallet. Digital identities and credentials are most frequently stored on mobile devices. Every participant in the digital identity ecosystem, whether a human, company, or machine, has a digital wallet to collect their proof of identity or other verifiable information. Thus, they always control the most current identity data.
Digital evidence in the form of verifiable credentials is provided by authorities, institutions, companies, or even individuals who are trustworthy issuers of proof of identity. The verifier plays the third role in this digital ecosystem, and they ask to verify the digital identity when interacting with the holder. The holder chooses whether to allow the verifier to access the evidence in his e-wallet each time it is requested. A verifier can choose to assign a given level of trust or assurance to any verifiable credential based on who the issuer was.
With SSI, the underlying infrastructure is typically provided by some form of a decentralized blockchain; it can store all public identifiers of the issued credentials to provide authenticity about the issuance; however, the data itself is never stored on the blockchain.
SSI technology connects people, businesses, and machines and breaks down barriers to digital interaction. Instead of having to re-identify themselves for every action – buying a train ticket, driving a rental car, checking into a hotel – users pull out their digital wallet, allow access, and control all the stages of their digital journey without unnecessarily handing over sensitive data, a concept known as “zero knowledge proof.” SSI allows the selective disclosure of identity attributes since data owners can choose which data they want to share under specific circumstances.
The way ahead to privacy-first user experience
The story of Self-Sovereign Identities is not isolated. On the way to widely adopting SSI, several challenges must be overcome, including interoperability issues, regulatory frameworks, fallback mechanisms for offline use cases, and general education for the general populace.
Service providers like Thales must build the necessary infrastructure and provide digital wallets for consumers and citizens. Several issues need to be addressed to serve the needs of individuals; progressive profiling, privacy and consent, data encryption, access policies, and identity lifecycle management.
The Thales OneWelcome Identity Platform can help you get on board today the Self-Sovereign Identity journey and be prepared for all the transitions and disruptions that will emerge. The platform includes orchestration, authorization, and sovereignty capabilities that make you future-proof.
Listen to the presentation “Self-Sovereign Identity: The Next Step in Privacy-First User Experience” at the Gartner Identity and Access Management Summit at Grapevine, TX, on Wednesday, March 22, 2023 / 11:10 AM - 11:30 AM CDT.

 Jason Keenaghan | Director of Product Management
Jason Keenaghan | Director of Product Management