Incident detection and response are crucial for effective security operations and business continuity. SOAR (security orchestration, automation & response) systems empower security operation teams to identify threats sooner, make smarter incident response decisions, and automate corrective playbook actions that would otherwise be subject to manual processing glitches.
During the Thales Trusted Access Summit 2021, Rishi Bhargava, VP, Product at Palo Alto Networks, and Dirk Strauch, NTT Data, and I discussed how security teams can leverage Cortex XSOAR and SafeNet Trusted Access to build a solid security posture for the enterprise.
The need for access management automation
The business threat landscape is evolving and expanding. Remote & mobile workforces, increased use of personal devices, proliferation of unauthorized shadow IT and apps, and cloud transformation all contribute to blurring the boundaries around the business ecosystem. This reduces visibility and increases complexity for security teams in implementing holistic security controls. The deluge of alerts from multiple, disparate security tools and manual tasks compound these problems for resource limited security teams leading to gaps in timely threat response.
Criminals are exploiting these security gaps and one of the most leveraged exploits is stealing or compromising user identities. Compromised identities or user accounts are then used to penetrate, navigate, and surveil corporate networks undetected, disrupting operations and exfiltrating sensitive data. Access security is a fundamental cornerstone of holistic enterprise security to ensure business assets stay protected and for business continuity. For remote access threats to be stopped in real-time, it is critical to automate your SOC’s response to untrusted login requests and suspicious access activity.
How Cortex XSOAR and Thales SafeNet Trusted Access work together
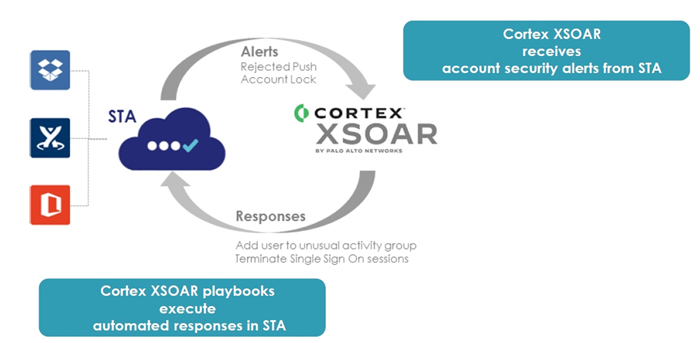
The SafeNet Trusted Access (STA) integration enables Cortex XSOAR from Palo Alto Networks to process alerts received from STA and other risk signal feeds from other SOC tools. The alerts from these tools and STA could indicate a security risk to end-user accounts. The integration also enables Cortex XSOAR to interact with STA to apply security remediation actions on user accounts and resources protected by STA. The remediation actions are automated through Cortex XSOAR Security Orchestration Playbooks. This integration, called the SafeNet Trusted Access Pack, is available on the Cortex XSOAR marketplace.
The SafeNet Trusted Access pack for Cortex XSOAR amplifies the overall enterprise security posture by enabling real-time control of suspicious access activity and authentication events, and decreasing workload for the SOC. SafeNet Trusted Access and Cortex XSOAR automatically trigger alerts and responses to enforce stronger access and authentication policies as needed.
For the alert handling process:
1. STA sends alerts to Cortex XSOAR that indicate user account security risks. For example, STA can alert Cortex XSOAR about end user account lockout situations due to repeated unsuccessful authentications, or rejected push OTP authentication requests on end user mobile devices.
2. Cortex XSOAR listens to alerts sent by STA and other SOC tools. XSOAR classifies the alerts received to handle the risk or threat by triggering remediation actions.
The remediation process involves the following steps:
1. Cortex XSOAR creates an incident, and executes automated security remediations through the defined orchestration playbook.
2. Cortex XSOAR can trigger remediation actions in STA. For example, XSOAR can trigger actions in STA to impose strong authentication requirements on a given user account where there is suspicious activity, or even terminate the user’s SSO session.
The integration of Thales SafeNet Trusted Access with Cortex XSOAR is depicted in the diagram below.
Benefits of the solution
Together, SafeNet Trusted Access and Cortex XSOAR enable you to:
- Reduce the risk of a data breach by detecting suspicious account activity, automatically triggering alerts, and orchestrate enforcement of stronger authentication & access policies in real-time.
- Reduce the SOC burden by automating workflow tasks to increase incident response efficiency and improve productivity for the entire team.
- Create a zero trust security posture by automating and orchestrating strong identity centric security controls.
If you want to find out more about how security teams can leverage Cortex XSOAR and Thales SafeNet Trusted Access to build a robust and effective access security posture for the enterprise, you can listen to our discussion entitled SOAR + IAM: The Perfect Recipe for Threat Management and Response.
