I’m limiting this discussion to public clouds, in particular Infrastructure as a Service and Platform as a Service (IaaS and PaaS), because these are the cloud consumption models where you have choices in data protection. With Software as a Service, you are wholly dependent on the provider for data protection in their cloud/service.
The shared responsibility for cloud security model has been with us for many years, and over the past five years, I’ve personally seen familiarity with the model grow from as low as 10% to nearly 90% (among American audiences). The model says that the cloud provider is responsible for the security of the infrastructure they provide, and the cloud consumer remains responsible for the security of any data that they store and/or use in the cloud.
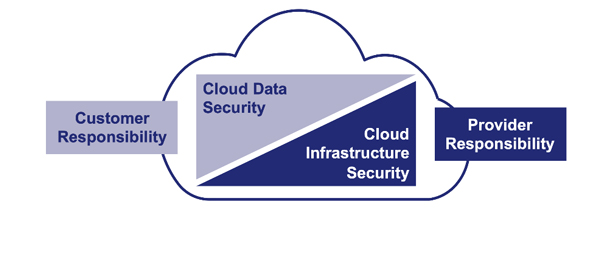
Check out the AWS and Azure content on the shared responsibility model.
How to protect data in this environment? You can certainly depend on the wisdom of the crowd, but for several years running, the Thales Data Threat Report-Global Edition consensus has been that encryption is the best way to protect data in the cloud. Many IaaS/PaaS providers offer their own encryption, and you can choose to Bring Your Own Encryption (BYOE) keys to help make their encryption more secure and compliant with your organization’s various data protection mandates. But, frankly, the only way you can truly and fully control access to your data in the cloud is through BYOE. Managing data security across multiple public clouds and different cloud storage options gets complex…quickly. BYOE allows you to secure your data as well as reach compliance rapidly and effectively. So how do you exactly implement BYOE? It can be summed up in a few steps:
1. Finding an encryption vendor whom you trust;
2. Ensuring the vendor’s encryption product is cloud-friendly; and,
3. Deploying it to your cloud workloads (which I discuss below).
This brings me to the launch of the CipherTrust Data Security Platform and how it makes it easy for you to BYOE to multiple clouds with uncompromised security and operating efficiency. At the core of the platform is the CipherTrust Manager, which manages keys and data protection policies for platform BYOE solutions. For cloud data security, you can deploy CipherTrust Manager on premises (as a hardware appliance with an embedded FIPS 140-2 Level 3-certified Luna HSM or as a virtual appliance), or in AWS, Azure, Google Cloud, or several other cloud providers. The flexibility of CipherTrust Manager is what delivers the operational efficiency I mentioned above. You might have a preferred cloud, or you might want to adopt a hybrid cloud approach. Practically wherever you are most knowledgeable and skilled, you can deploy CipherTrust Manager. The only requirement is that CipherTrust Manager needs to be able to “reach” (network) the BYOE solutions to deliver keys and policies.
In terms of Bring Your Own Encryption solutions…
- CipherTrust Transparent Encryption is your data protection solution for IaaS. You can embed it in your cloud operating system templates so that each time you instantiate an OS from a template in your cloud, it will find CipherTrust Manager and download keys and related data protection policies. CipherTrust Transparent Encryption includes huge security enhancements relative to cloud provider “native” encryption including server-based granular access controls (that can blind even cloud provider superusers from the data) and the ability to encrypt AWS S3 buckets with the same granular access controls.
- CipherTrust Tokenization is a great option for PaaS. Typically, in PaaS you get control of and access to the data flows with scripts. You can embed RESTful calls to CipherTrust Tokenization to protect (tokenize) or gain access to (detokenize) PaaS data into your scripts. You can deploy the Tokenization Server as a cluster – with nodes on premises and in the cloud as needed -- so you can tokenize data on premises and detokenize it in the cloud, or vice-versa. With tokenization, we’re talking comprehensive hybrid cloud data protection. (CipherTrust Transparent Encryption also provides hybrid cloud data protection.)
- CipherTrust Vaultless Tokenization includes dynamic data masking, which is totally cloud-friendly as well. Based on AD or LDAP lookups, you can define who can see how much of each detokenized data element. And all tokenization and dynamic data masking setup is completed with a fast, easy, and efficient graphical user interface.
One final mention about operating efficiency:
- If you use multiple clouds then you have to manage each cloud provider’s security solutions in their consoles. If you’re really sharp, you can automate this with their APIs and CLIs.
- In contrast, with CipherTrust BYOE solutions, data security management for the IaaS/PaaS clouds you use is centralized on CipherTrust Manager. No cloud consoles. And CipherTrust Manager has the APIs you need to automate centralized security management too!
- Because you’re managing keys centrally, you can move a data set from one cloud to another or repatriate it without having to decrypt and re-encrypt it. Now that’s efficient data mobility.
I’ll close with just one more benefit of BYOE with the CipherTrust Data Security Platform. If you decide to bring CipherTrust Manager to the cloud, you can rest assured that it is a wholly protected black box to the cloud provider. As a virtual appliance deployed in the cloud, no cloud superuser can gain access to it. Same goes for the tokenization server.
To learn how to simplify data security in the cloud, visit our Bring Your Own Encryption web page.
You can also Tweet me @cyberswimmer or send me a note on LinkedIn at linkedin.com/in/cyberswimmer

 Eric Wolff | Senior Product Marketing Manager
Eric Wolff | Senior Product Marketing Manager