Today, organizations are struggling to control their data environments. The amount of data created is forecasted to grow and be spread in a wide diverse ecosystem: the cloud, on premises, in data lakes and big data. The shift to working from home over the past year, as reviewed in “451 Research’s Voice of the Enterprise: Digital Pulse” published on October 2020, identifies the “information security as the priority respondents cited most often as having become greater”.
In addition, according to the “2020 Year End Report of Data Breach” from QuickView, the number of records compromised in 2020 revealed a 141% increase compared to 2019. One of the two main causes of cloud data breaches is due to data exposed as a result of misconfigurations based on “Cost of a Data Breach Report” of 2020 by IBM.” These numbers raise an important question, how should organizations coordinate their efforts to have in place effective security strategies?
Many organizations deploy solutions to help protect data using encryption, tokenization or data access management, but this approach is like finding a needle in a haystack. To establish and align a data security program with controls and technology applied correctly, organizations need to have complete data visibility. For example, what data they have, where it is, who has access and what is the right protection method that will eliminate risk. Otherwise, an organization might implement a solution that is not compliant with important security requirements or causes adverse effects to the business. Also, they have to make sure that the selected products are integrated or coordinated. Moreover, using siloed solutions or products that do not support on premise and in the cloud data visibility, may generate inconsistences and increase ongoing misconfiguration and management.
The Added Value of Data Visibility
Having an understanding of the data allows organizations to manage it in line with internal business requirements, and within the confines of privacy law mandates. Therefore, organizations will benefit from:
a. Enhanced security. Organizations can visualize what type of data they have, where it is, who can access it and the risk of exposure. They are able to highlight the security risks to prioritize and apply appropriate remediation actions, avoid misconfigurations and rectify compliance gaps.
b. Improved efficiency. Knowing the data an organization handles allows defining holistic strategies focused on it. The inconsistences and management can be reduced by taking advantage of articulated management of the security and privacy policies through central coordination.
It quickly becomes evident that data visibility is the first step an organization should take for a successful security strategy.
The Suggested Path to Follow
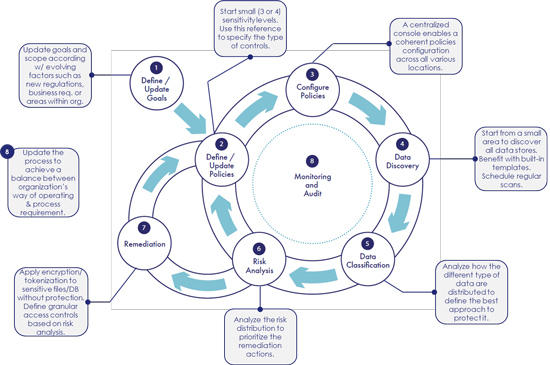
The data visibility process is not a one-time event. On the contrary, it is an ongoing process comprised of data discovery and classification. Before initiating this process, a typical organization may start by identifying the pain points related to understanding sensitive data, tracking relevant regulations, reducing data access risks, validating digital transformation initiatives or implementing effective remediation.
Once the main objectives are established, it’s important to articulate the strategy to implement a classification process based on agreed upon goals. It would normally involve analyzing the different types of data the organization manages, defining the required categories together with the controls to apply, and the impact in the event of a data security violation.
When the policies have been defined, organizations need to use a solution to automate the data visibility process. At this point, they need to identify the data stores to search for sensitive data and determine what type of data to find (for example, personal, financial, or healthcare data). Once the policies are established, the data discovery step can start. This is an iterative process that will provide data visibility to the organization. Being able to schedule a scan and automatically apply remediation actions makes the process repeatable and scalable.
The data classification step is key for understanding the type of data that organizations hold. With this step, organizations can decide how to manage data properly, whether they are subject to a privacy regulation, how to protect their data, and who should have access to it. Indeed, based on the “2021 Cloud Data Security Report” from Netwrix, organizations with data classification implemented were able to resolve incidents like ransomware, data theft by insiders or hackers, accidental data leakage and data loss in minutes or hours, while other organizations needed days, weeks or months.
The next suggested action is to analyze the risk of exposure based on the insights of the scan’s results. This helps an organization plan the best approach for mitigating or removing the existing risk through remediation. The following step is to take a remediation action based on the risk analysis performed. Actions such as data encryption, tokenization, or a proper configuration of data access will reduce an organization’s risk of exposure.
In parallel, organizations might consider a monitoring task to achieve their goals. Therefore, the last step is to run audits to check that controls are in place and are working properly.
The following image explains the main steps to follow, and provides recommendations for each stage.
The Importance of a Unified Data Visibility Platform
Automating data visibility is key for improving efficiency and enhancing security. Thales CipherTrust Data Discovery and Classification helps organizations efficiently discover, classify and protect sensitive data across their traditional as well as modern repositories like the cloud and big data, no matter if the data is structured or unstructured.
Simple to deploy, the solution provides organizations with a centralized and integrated view, as it is part of the Thales CipherTrust Data Security Platform. It brings discovery, protection and control all together to optimize data security.
Discover information on our data visibility process, in our Data Visibility Planning Guide.

 Ludmila Rinaudo | Product Management
Ludmila Rinaudo | Product Management