Introduction
Imagine a world where hackers could easily crack the encryption protecting your most sensitive information. With the potential challenge of quantum computing on the horizon, such a scenario could become a reality. Cryptography plays a vital role in safeguarding data and verifying its authenticity, but traditional methods are vulnerable to these powerful machines.
This blog post explores two key guidelines, CNSA 2.0 and FIPS 140-3, to help you prepare for the transition to post-quantum cryptography (PQC) algorithms – the future of secure data protection.
Understanding CNSA 2.0 and FIPS 140-3
- CNSA 2.0: A Foundation for Strong Algorithms
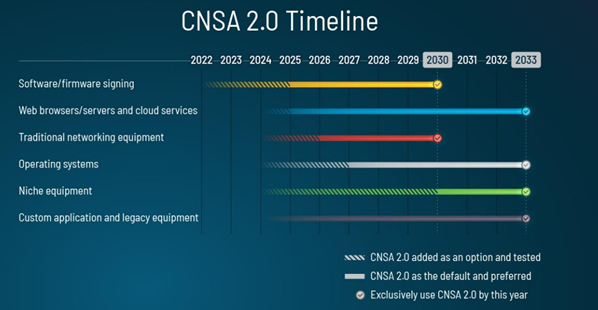
The National Security Agency's (NSA's) CNSA Suite specifies a set of robust and secure cryptographic algorithms for protecting sensitive US government information. It focuses on the "what" – the recommended algorithms for tasks like encryption and digital signatures. Announced in September 2022, CNSA 2.0 introduces the first recommendations for PQC algorithms, paving the way for a smoother transition. CNSA2.0 has stated the following transition timeline, outlining the urgent use cases to implement PQC and by what date: - Software and firmware signing: begin transitioning immediately, support and prefer CNSA 2.0 by 2025, and exclusively use CNSA 2.0 by 2030.
- Web browsers/servers and cloud services: support and prefer CNSA 2.0 by 2025, and exclusively1 use CNSA 2.0 by 2033.
- Traditional networking equipment (e.g., virtual private networks, routers): support and prefer CNSA 2.0 by 2026, exclusively use CNSA 2.0 by 2030.
Operating systems: support and prefer CNSA 2.0 by 2027, exclusively use CNSA 2.0 by 2033.
You can find more details on the phased approach in the official FAQ here.
- FIPS 140-3: Ensuring Secure Implementation
FIPS 140 (Federal Information Processing Standard 140), published by NIST, is a distinct standard outlining security requirements for cryptographic modules. Unlike CNSA Crypto, it focuses on the "how" – ensuring the modules that implement these algorithms are secure throughout their lifecycle. FIPS 140 has a broader global adoption due to its focus on best practices. While FIPS 140-3 (effective from September 2019) itself hasn't yet incorporated PQC, the groundwork has been laid so that future updates can accommodate PQC implementations. Here's a summary of the key updates in FIPS 140-3 (https://csrc.nist.gov/pubs/fips/140-3/final):- Support for hybrid deployments, including hardware, firmware, software, and combinations.
- Incorporation of ISO standards for broader compatibility (aligned with ISO/IEC 19790:2012(E)).
- Preparation for PQC algorithm certification.
Analogy: Crypto's Recipe and Restaurant
Imagine CNSA Crypto as a recipe book with trusted recipes (algorithms) for secure data protection. FIPS 140-3 functions like a restaurant certification program. It verifies that the kitchen (cryptographic module) maintains a clean and secure environment (security measures) regardless of the specific recipe used. Obtaining FIPS 140-3 certification is a complex process, requiring evaluation of both the cryptography and the implementation environment.
Securing Your Cryptographic Future
There’s no doubt, the transition to PQC algorithms is essential for ensuring continued data security. Here's a roadmap to get you started:
1. Stay Informed: Regularly check the NIST PQC project page (NIST PQC project page) for updates. Also considering subscribing to relevant resources like the NIST PQC project page and the Thales cybersecurity blog for the latest updates. Global regulatory bodies such as ANSSI, BSI, and more, will all be updating their guidance based on the NIST PQC project, so be sure to stay current on the regulations for your region of the world as well.
2. Evaluate Your Cryptographic Landscape: Conduct a risk assessment to understand your current cryptographic use cases and dependencies. Consider leveraging the Thales PQC assessment tool (Thales PQC assessment tool).
3. Develop a Comprehensive Phased Transition Plan: Collaborate with security consultants to create a full plan for migrating to CNSA 2.0 and PQC algorithms, prioritizing based on your specific needs and the CNSA guidelines. The transition will take quite a long time so getting ahead of the game will be critical to ensure a smooth transition.
4. Embrace PQC Readiness: Explore the Thales Luna PQC Starter Kit, a secure environment for testing and integrating PQC algorithms. This FIPS 140-3 certified HSM solution can give you a head start on the transition (Thales Luna PQC Starter Kit). For data-in-motion, Thales also offers an High Speed Encryptor PQC Starter Kit.
By following these steps and leveraging expert guidance, you can ensure your organization's cryptographic infrastructure is robust and future-proofed against the challenges of quantum computing.

 Shaun Chen | VP APJ strategic account sales engineering, Thales CSP
Shaun Chen | VP APJ strategic account sales engineering, Thales CSP