You've likely seen the headlines about ransomware attacks and the monumental challenges they pose for organizations. But what should you do when an attack occurs, even if you have a ransomware protection solution in place?
In this post, we will delve into the forensics of a ransomware attack, showing you how to classify the attack and recover from it if a ransomware protection solution is in place. The old saying “an ounce of prevention” holds true in this context.
Using real examples from WannaCry and Crytox ransomware attacks, we will highlight effective recovery strategies. You will gain the knowledge to navigate these crises and understand how ransomware affects your files given you have a ransomware protection solution in place.
Learn more from our ransomware blog series by selecting:
Understanding Ransomware Attacks
How Ransomware Encrypts Files
Ransomware attacks often use cached I/O to encrypt files quickly. This method allows ransomware to encrypt many files in cache rapidly.
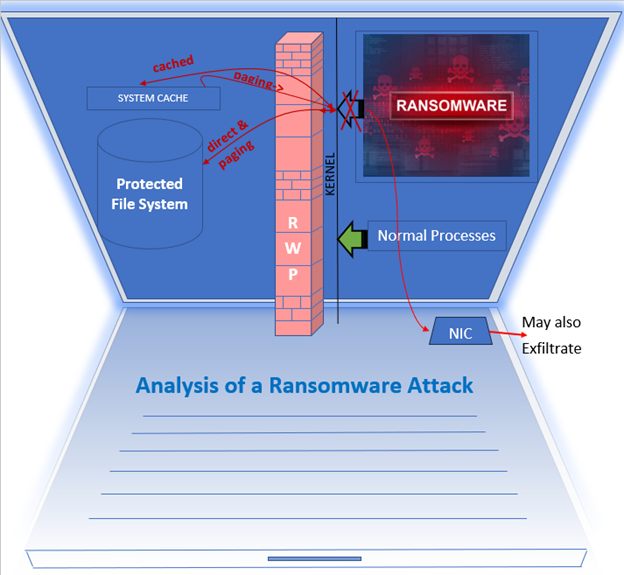
Types of Ransomware Attacks
There are two basic types of ransomware attacks:
1. Across-file attacks: The ransomware encrypts the data and writes it to a new file, potentially with a randomized or email-syntax filename.
2. In-place attacks: The ransomware reads data from the original file, encrypts it, and writes it back to the same file.
Let us explore these through real-world examples: WannaCry and Crytox.
Across-file Ransomware Attack: WannaCry
By simulating a WannaCry ransomware attack, we can accurately identify its characteristics and behavior. For this discussion, we have intentionally partially disabled our ransomware protection, allowing two files to be encrypted on disk. This controlled scenario creates a smoke trail, providing valuable insights for discussion and analysis.
Detecting and Investigating WannaCry
Let us look at a four-step process to detect and investigate the ransomware attack. For our discussion, we will use CipherTrust Transparent Encryption Ransomware Protection (CTE-RWP) as a tool to help us in detecting and investigating these attacks. CTE-RWP protection sensitivity has been relaxed to allow a few files to get infected before CTE-RWP blocks it. Here is a short video that shows this.
1. Detection: When the attack starts, you will get a CTE-RWP pop-up and a detected log entry.
2. Log Analysis: Check the log entry to see which directory was last accessed by the ransomware.
3. File Inspection: Navigate to the directory and examine the files. You will notice the extension ".wncry" on several files, indicating shadow files. The original files next to them should be clear if blocked before any paging write occurred. This separate original file indicates an across-file encryptor.
- Please note that for some ransomware, if any network shares were previously accessed by that agent, then the ransomware may have additionally accessed files on that remote system, including directories on that system other than just the share. It is important to check files on any remote system previously accessed by this system.
4. Volume Check: Search the all volumes for files with the ".wncry" extension to see which files were encrypted on disk. Since we relaxed our ransomware protection, 2 files were encrypted to disk for this discussion.
Recovery from WannaCry
The ransomware may have compromised other aspects of the system, such as disabling Task Manager or blocking access to the Windows console. Please note that without ransomware protection installed, the only recovery options may be paying the ransom or restoring from an unaffected backup.
To recover:
- Shut down the system and move the data volumes to another system.
- Verify the integrity of the original files.
In-place Ransomware Attack: Crytox
Next, let's examine an in-place ransomware attack using Crytox. For this discussion, we will continue utilizing CipherTrust Transparent Encryption Ransomware Protection (CTE-RWP) tool to detect and investigate the attack. We have adjusted CTE-RWP's protection sensitivity, allowing a few files to become infected before the protection mechanism blocks further encryption. This controlled scenario creates a smoke trail for analysis. Here is a short video illustrating this process.
Detecting and Investigating Crytox
1. Detection: When Crytox attacks, it will be detected quickly.
2. Log Analysis: Check the CTE RWP log to see which path Crytox was accessing, which in our example is through svchose.exe and explorer.exe.
3. File Inspection: The encrypted files have the ".waiting" extension with no original filenames left next to them, indicating an in-place attack. Check remote systems you had previously accessed shares on those remote systems.
4. System Reboot: Since Crytox does not restart on reboot, reboot the system to clear the cache. Ideally, remount the volume to another system to be safe. Check all files with the ".waiting" extension to ensure they are clear.
Recovery from Crytox
The ransomware may have compromised other system components, such as disabling Task Manager or blocking access to the Windows console. Please note that without ransomware protection, the only recovery options may be paying the ransom or restoring from a backup that predates the attack.
To recover:
- Remount the volume on a separate secure system.
- Verify the integrity of the original files. In this example, we relaxed ransomware protection to allow a few files to be encrypted, showing how encrypted data has high entropy.
- Remove the ".waiting" extension on the files to restore accessibility. Your original clear files should now be back to accessible.
Beware: Ransomware Can Access Remote Shares
One crucial but often overlooked aspect of ransomware attacks is the ability of certain types of ransomwares to exploit remote shares, gaining access to all directories on the connected system. Lockbit is a prime example.
If Lockbit compromises System A and System A has previously accessed a share on Remote System B, then Lockbit can potentially access all directories on System B. This means that after an attack on System A, it is imperative to promptly and thoroughly check all other systems that System A accessed to prevent further spread and damage from the ransomware. If a share is indeed seen to have been attacked, then check all other directories on that remote system as well.
Summary
Here are the steps to take after detecting a ransomware attack:
1. Find the last directory accessed by the ransomware using the CTE-RWP logs.
2. Explore the affected directory to find the extension or name pattern the ransomware used for encrypted files.
3. Check remote systems previously accessed by this system.
4. Shut down and remount the data volumes onto another system.
5. Search the volumes for files with the ransomware's extension or name pattern.
6. Verify the integrity of the files, focusing on the original files for cross-file attacks and the encrypted files for in-place attacks.
Watch How Ransomware Attacks Unfold and Get Stopped in Their Tracks!
Want to dive deeper? Register for our upcoming webinar Bouncing Back: How to Protect and Recover After a Ransomware Attack to learn more.
Check out a short video to see firsthand how two notorious ransomwares operate. See CipherTrust Transparent Encryption Ransomware Protection (CTE RWP) in action, halting the attack even if the ransomware was already lurking undetected in your environment before CTE-RWP was installed.
Have questions about CTE-RWP and the robust power of our ransomware protection? Contact THALES to book a discovery call and discover how we can help you safeguard your data.

 Russel McDonald | Principal Software Engineer, Thales
Russel McDonald | Principal Software Engineer, Thales