Software supply chain attacks have been rapidly increasing in the past few years. Also called backdoor attacks, they cleverly exploit third-party software vulnerabilities to access an organization’s systems and data. These infiltrations tend to be very lucrative for criminals and devastating to businesses, as a single breach can impact thousands of victims in a rapid domino effect. However, the combined partnership of Thales and DigiCert offers solutions to help protect against these security risks.
By 2025, Gartner predicts that 45% of organizations worldwide will have experienced attacks on their software supply chains. The news has already captured some very high-profile incidents, including attacks on an American retailer, a software vendor, and more recently a multinational investment and financial services bank.
How are the hackers getting in?
Attacks are most commonly executed by hijacking software updates, undermining code signing, and compromising open-source code. Hackers tend to target software with poor security. In most cases, criminals sneak in behind legitimate processes to get unrestricted access to an organization's software ecosystem to wreak havoc. Examples include covertly inserting malware or manipulating unprotected code-signing keys.
How can organizations protect their data?
Fortunately, there are several preventive measures organizations can take which are recommended by the Cybersecurity and Infrastructure Security Agency (CISA). These include the 4 following best practices:
1 – Protect software releases with Code Signing
Most modern software is a compilation of code and packages from multiple sources. This may include open source, third party, and various libraries – in addition to possible multiple components from internal and external DevOps and Continuous Integration/Delivery (CI/CD) teams. Multiple security measures need to be integrated and automated during each build and release cycle. Tampering, such as inserting malware, can occur at any point during this process. Tampering can involve inserting 3rd party code (often coming from open-source software components), manipulating the organization’s proprietary source code, or even manipulating the artifacts that are used to build the software.
Software releases can be protected by code signing. This framework uses digital certificates and the public key infrastructure (PKI) to sign program files so that users can authoritatively identify the publisher of the file and verify that the file hasn’t been tampered with or accidentally modified. Organizations can stop application and software tampering by using DigiCert Code Signing Certificates to ensure their downloaded files are published as intended. Additionally, software developers can use DigiCert Extended Validation (EV) code signing certificates to digitally sign apps, drivers, and software programs as a way for end-users to verify that the code they receive has not been altered or compromised by a third party.
2 – Protect Private Keys
The most significant issue with code signing is protecting the private keys associated with the code signing certificates. If the keys are compromised, the certificate and software can no longer be fully trusted. To protect keys, organizations generally can choose to apply software or hardware protections. However, due to several high-profile hacks into systems using software-only protections, the trend is increasingly to embrace more robust forms of hardware-based solutions. For example, both the National Institute of Standards and Technology (NIST) agency and the Certification Authority Browser Forum (C/AB) consortium recommend using hardened cryptographic hardware products to protect keys, such as Hardware Security Modules (HSMs) as a security best practice. For example, Thales Luna Hardware Security Modules (HSMs), are intrusion-resistant, tamper-evident FIPS validated and Common Criteria EAL 4+ certified hardware devices that provide a secure root of trust for code signing. For organizations needing flexible deployment models, Luna HSMs are one of the few available on-premises, as-a-service, or in a hybrid model. Luna HSMs can also be used to securely generate, store, and manage the private keys used in code-signing applications. They also provide strict access and control over the use of keys (which must be kept inside the HSM to perform the code signature), as well as generate a secure audit log to track access. All of these protections, ultimately ensure the private code signing keys aren’t stolen or misused.
3 - Proactively detect software vulnerabilities
To minimize any code signing process vulnerabilities, centralized solutions that combine advanced binary analysis and threat detection are recommended. DigiCert Trust Software Manager improves software integrity through deep binary static analysis to verify software is free from known threats like malware, software implants, software tampering, and exposed secrets before the final software is code signed. Additionally, DigiCert Trust Software Manager works in conjunction with both on-premises Luna HSMs and Luna Cloud HSM services (available on Thales Data Protection on Demand), to ensure customers can protect their data on-premises, in the cloud, or across hybrid environments.
4 – Reduce risk with SBOMs
Following several major software supply chain attacks, Executive Order 14028 was issued outlining the value of a Software Bill of Materials (SBOM) to improve cybersecurity. A Software Bill of Materials is a list of components attached to the software as a nested inventory. It lists every piece of code that makes up the full software package, so you can know what to trust and more easily trace and eliminate vulnerabilities or malware. Leveraging automated tools for scanning to minimize oversight risks that can also generate SBOMs, such as DigiCert Software Trust Manager can greatly benefit organizations seeking to apply protective and compliance measures more rapidly.
Thales and DigiCert Architecture Overview
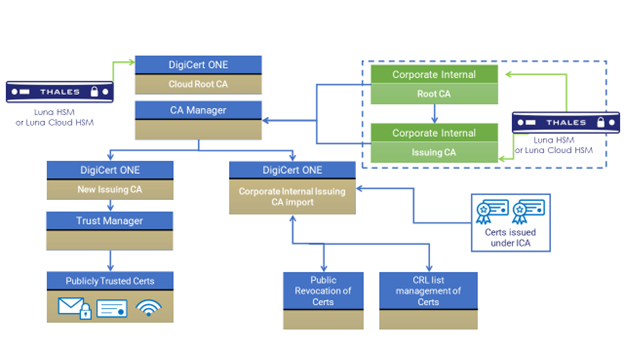
Conclusion
While the threat of software supply chain attacks looms large on the horizon, there are several ways to defend against these breaches. Together, both Thales and DigiCert together can help protect against software supply chain attacks by ensuring software integrity for organizations. To learn more, please join our upcoming webinar on April 23rd.

 Melody Wood | Partner Solutions Marketing Manager, Thales
Melody Wood | Partner Solutions Marketing Manager, Thales