Data has been migrating from traditional data centers to third-party hosted environments, private/public cloud infrastructures and Software-as-a-Service (SaaS) applications by leaps and bounds. With this in mind, providing easy access to data for everyone (customers, partners, employees) and securing sensitive data has to be a priority.
Protecting sensitive data is the last line of defense
Data breaches continue to occur, in spite of all the perimeter and endpoint security controls being deployed to defend against sophisticated cyber attacks. In addition, a myriad of evolving data privacy and compliance regulations continue to be developed to provide governance over business critical data.
However, these counter measures have not been enough to stop sophisticated cyber criminals from stealing sensitive data including personally identifiable information (PII), credit card numbers and customer data. Companies have realized that protecting sensitive data through access controls, encryption and tokenization is the last line of defense for preventing data exposure and reducing overall business risks.
Selecting the right data security strategy
It can be challenging to manage multiple encryption technologies and crypto keys across a variety of data silos – file-systems, databases, containers, big data and private/public cloud environments. IT security teams need a centralized encryption and key management platform to accomplish this.
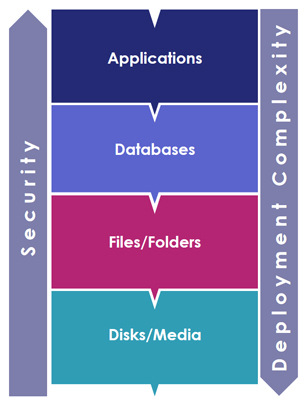
Encryption can typically be employed at four different levels in the technology stack - full-disk or media, files/folders, databases, and applications. When encryption is employed lower in the stack, deployment is much easier and it is less likely to interfere with operations in the layers above.
On the other hand, security improves and more threats are mitigated when encryption is applied in the upper layers closest to the application, since data is protected right at the source before the data leaves the application. While this data security strategy offers significantly increased protection as it guards against unauthorized users and applications gaining access, it is typically more complex, costly, and time consuming to implement because application developers need to modify every application that will require access to the encrypted data.
Implementing comprehensive data-at-rest protection
Once IT security teams discover and classify where sensitive data resides throughout their enterprise, they need to collaborate with each application/database owner in each business unit and decide where in the technology stack data should be encrypted. To enhance compliance with organizational and industry mandates around encryption and key management, your organization needs to extend data protection across more environments, systems, applications, processes and users. With the CipherTrust Data Security Platform from Thales, you can effectively manage data-at-rest security using the optimal solution according to use case, threats addressed, and acceptable deployment complexity
- Disk/Media Protection: CipherTrust Enterprise Key Management provides centralized key management to protect KMIP compliant storage-arrays and self-encrypting drives, and mitigate data exposure if disk drives are stolen. The disadvantage of this approach is that it addresses a very limited set of threats, only offering data protection if the physical drive is stolen
- File-system Protection: CipherTrust Transparent Encryption protects data at the file-system level on servers, databases, Windows/Linux/AIX OSs across virtual and physical servers. And it mitigates data exposure and unauthorized access to data. One of the key advantages of this approach is that it is transparent to users and applications, meaning organizations don’t have to rewrite applications or change associated business processes.
- Database Protection: CipherTrust Database Protection provides functions to encrypt columns within databases. Using this approach, organizations can establish strong safeguards against a range of threats, including malicious insiders—even in some cases a malicious database administrator.
- Application Protection: CipherTrust Application Data Protection provides crypto functions for encrypting, hashing, signing specification application-level data. In general, the advantage to these solutions is that they typically protect very specific subsets of data, such as fields in a database. CipherTrust Tokenization is offered both vaulted and vaultless and can help reduce the cost and complexity of complying with data security mandates such as PCI DSS.
Most experts agree that nearly every organization will suffer a data breach at some point – it’s a matter of “when”, not “if”, you’ll be attacked. Imagine the peace of mind (and risk reduction) in knowing that any data siphoned out of your organization is encrypted and therefore worthless to the cybercriminal who stole it. With the CipherTrust Data Security Platform, organizations can leverage a comprehensive solution that can address a wide range of environments and use cases. Through these advanced capabilities, organizations can handle their security mandates, while minimizing costs and administrative efforts.
While building your plan to protect sensitive data, explore the CipherTrust portfolio of products.

 Nisha Amthul | Senior Product Marketing Manager
Nisha Amthul | Senior Product Marketing Manager